14 May 2017
WannaCry ransomware widespread attack may indirectly hit Industrial organizations
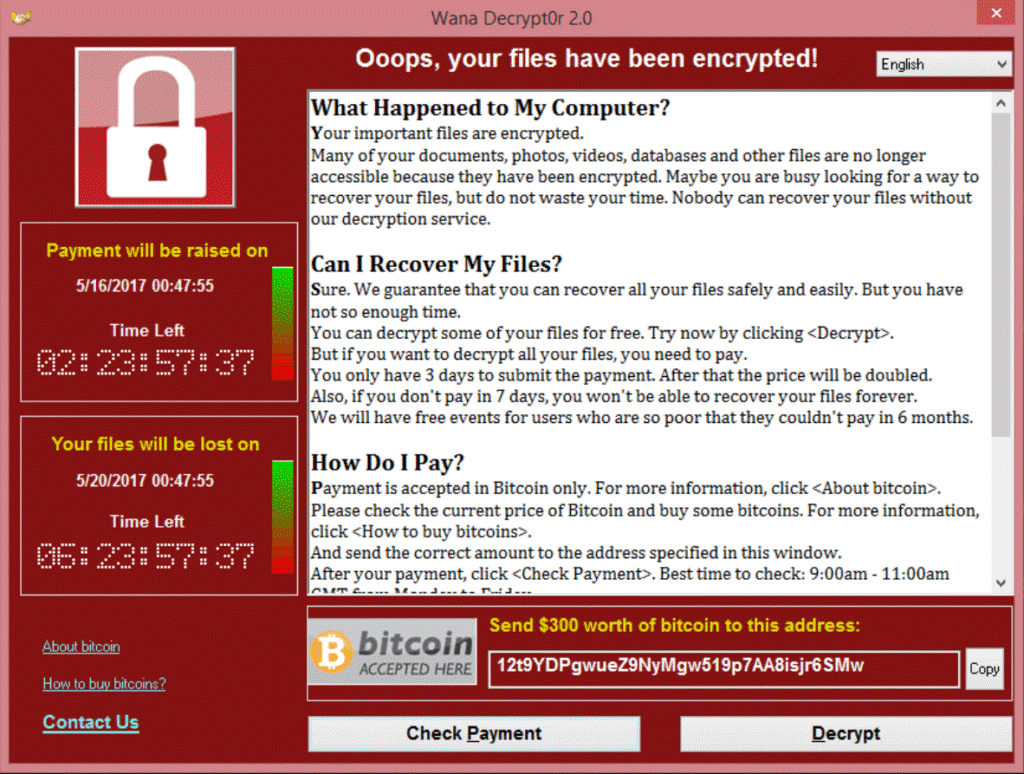
The WannaCry outbreak has being reported on May 12 2017 by many independent sources all over the World. It targets most of Windows operating system. The ransomware is not specifically designed to attack industrial systems. However, based on KL ICS CERT live reports we decided to warn industrial organizations that they might indirectly become a victims of this widespread attack.
The ransomware exploits known Windows SMBv2 software vulnerability that allow the attacker to execute remote code on compromised system. The original exploit code was available to public from April 14 2017. Microsoft has released a new patch that fixes this security flaw on March 14 2017.
Although this attack does not target Industrial facilities, KL ICS CERT team still recommends industrial organizations to immediately take the following safety actions
- As soon as possible install the official patch (MS17-010) from Microsoft, which closes the affected SMB Server vulnerability used in this attack;
- Download and install latest antivirus product and signature updates for your antivirus solution. If you are using Kaspersky Lab antivirus solutions, please enable Kaspersky System Watcher, Application Startup Control or Anti Cryptor. These features will detect and block malicious attempts to encrypt any data. Also all the Kaspersky Lab’s solutions containing Intrusion Detection mechanisms will detect and block this threat on the network layer;
- Make sure that you have backup copies of all sensitive data;
- Scan all your systems with antivirus software. In case if the threat was detected and removed please, reboot your systems.
In case if you have any questions or need help please reach us with email on ics-cert@kaspersky.com
Indicators of compromise
Samples observed in attacks so far
4fef5e34143e646dbf9907c4374276f5 5bef35496fcbdbe841c82f4d1ab8b7c2 775a0631fb8229b2aa3d7621427085ad 7bf2b57f2a205768755c07f238fb32cc 7f7ccaa16fb15eb1c7399d422f8363e8 8495400f199ac77853c53b5a3f278f3e 84c82835a5d21bbcf75a61706d8ab549 86721e64ffbd69aa6944b9672bcabb6d 8dd63adb68ef053e044a5a2f46e0d2cd b0ad5902366f860f85b892867e5b1e87 d6114ba5f10ad67a4131ab72531f02da db349b97c37d22f5ea1d1841e3c89eb4 e372d07207b4da75b3434584cd9f3450 f529f4556a5126bba499c26d6789224
Kaspersky Lab detection names
Trojan-Ransom.Win32.Gen.djd Trojan-Ransom.Win32.Scatter.tr Trojan-Ransom.Win32.Wanna.b Trojan-Ransom.Win32.Wanna.c Trojan-Ransom.Win32.Wanna.d Trojan-Ransom.Win32.Wanna.f Trojan-Ransom.Win32.Zapchast.i PDM:Trojan.Win32.Generic