29 June 2017
More than 50% of organizations attacked by ExPetr (Petya) cryptolocker are industrial companies
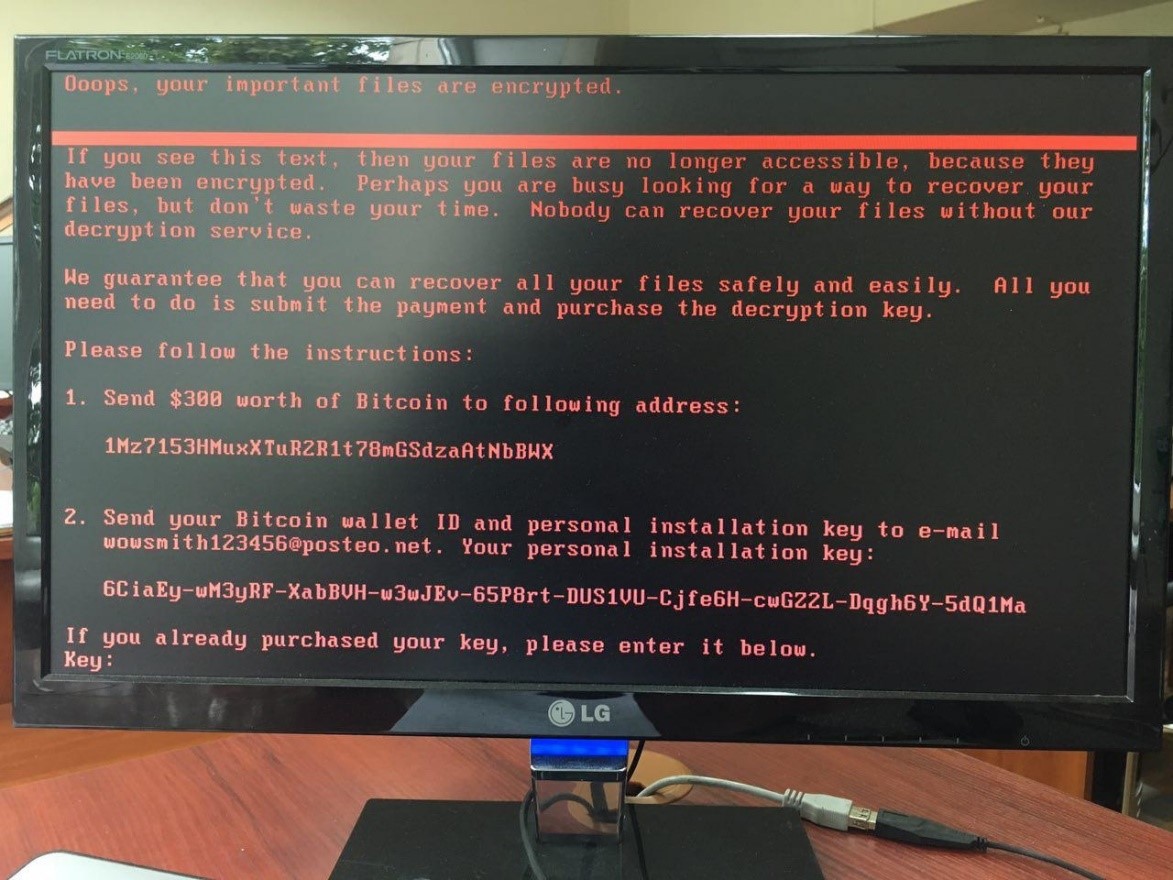
June 27, 2017. Lots of computers were attacked by a cryptolocker ransomware.
Malicious software instructs its victim how to pay the ransom
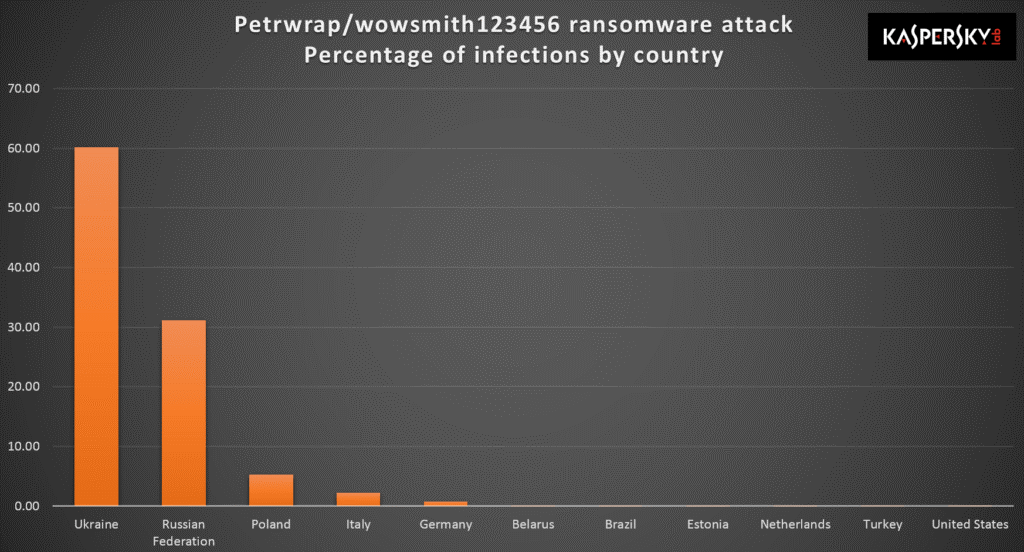
According to Kaspersky Lab telemetry, by the end of the day most of the victims were located in Ukraine and Russia.
By the morning of July 28th, we have seen attacks on companies in U.S., Europe and Asia.
The first publications in mass media stated that new malware was connected to well-known malicious programs WannaCry and Petya. However, according to Kaspersky Lab research this is new malware with some slight similarities to PetrWrap (Petya modification), but most likely having no connection with it. We call it “ExPetr”, to emphasize that this is not PetrWrap.
Since reliable encryption algorithms are used by the malware, there are no known ways to decrypt or restore the encrypted files. After an analysis of malware’s encryption routine, our experts have thought that the threat actor cannot decrypt victims’ data, even if a payment was made (the technical details are available from here).
This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware.
First infections and Attack Vectors
At the moment, there is information on a few infection vectors.
- We have information about at least one known case of infection through a watering hole attack.
- In some cases to launch the malware on victim’s computers the malicious actors used the MEDoc application (which is a Ukrainian tax accounting software, used by local administration). According to some sources MEDoc’s update function was used to infect the victim’s computers.
- In addition, it is also important to note that phishing emails having malicious attachments or links to malicious resources could also be used as one of the infection vectors.
Local network propagation
There are two ways ExPetr (Petya) propagates inside the victim’s local network:
- When it has infected a computer inside the company’s local network, ExPetr starts to infect other computers inside the network, using modified versions of EternalBlue and EternalRomance exploits. These exploits were shared publicly by The Shadow Brokers hackers group on April 14, 2017. They became widely known after the WannaCry attack, as it used EternalBlue to infect tens of thousands victims machines all over the Globe. The exploit utilizes vulnerabilities in SMB v.1 service of various versions of Windows OS, starting from Windows XP, if the operating system is not properly patched. To exploit the vulnerability the computer needs to have SMB v.1 service up and running and TCP 139 и 445 ports should be available for connection.
- The ExPeter is able to execute itself on computers inside victim’s network via PsExec and WMI tools. It uses the local user account credentials stolen by a malicious tool similar to Mimikatz (the tool was found it the ExPetr resources).
The malicious software saves itself as perfc.dat file in Windows folder as it spreads along the victim’s network.
Encryption
The malware overwrites the MBR on the victim’s hard drive with its own loader, that shows the ransom payment instructions and encrypts files of the following formats:
.3ds .7z .accdb .ai .asp .aspx .avhd .back .bak .c .cfg .conf .cpp .cs .ctl .dbf .disk .djvu .doc .docx .dwg .eml .fdb .gz .h .hdd .kdbx .mail .mdb .msg .nrg .ora .ost .ova .ovf .pdf .php .pmf .ppt .pptx .pst .pvi .py .pyc .rar .rtf .sln .sql .tar .vbox .vbs .vcb .vdi .vfd .vmc .vmdk .vmsd .vmx .vsdx .vsv .work .xls .xlsx .xvd .zip
As shown above, the list consists of popular office document file extensions, as well as archives, mailboxes, virtual machine images, databases, backups, and files used by Microsoft Visual Studio development suite, as well as C, C++, C#, Python and PHP program sources.
The malware also uses reliable cryptography algorithms. It securely generates a separate AES-128 encryption key for each file being encrypted, and encrypts it using RSA-2048 public key which belongs to malicious actors. Currently, there are no significant mistakes found in the encryption algorithm implementation which would allow one to restore the victim’s encrypted files.
Facts to notice
In addition to other commonly known reports being mentioned by Kaspersky Lab and other researchers, Kaspersky has also found another interesting fact to note: If you look closely at the ransom payment instructions text, you’ll see that the use of punctuation (in the case below, commas) is not consistent with proper English grammar.
Industrial companies are under attack
As Kaspersky lab specialists have emphasised multiple times recently, the malicious actors that are utilizing ransomware attack vectors are switching their focus to companies and organizations rather than home users, and industrial companies are no exception.
Threats like ExPetr (Petya) are extremely dangerous for critical infrastructures and industrial companies because the attack can potentially impact the victim’s technological process automation/control systems. Such an attack could affect not only business production and finances, but also human safety.
According to our telemetry, we see evidence that many industrial companies are being attacked by ExPetr (Petya) malware. While there were examples of actual industrial control systems being affected, in most cases it was only the business networks that were affected.
Below is the ExPetr (Petya) targets by industry spread graph created using Kaspersky Security Network statistics data as of June 28, 2017.
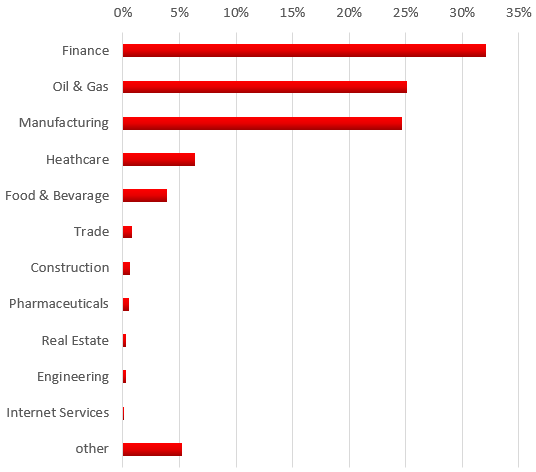
Breakdown of industrial companies attacked by industry
According to our data, at least 50 percent of the companies being attacked are manufacturing and oil & gas enterprises.
How to defend against this threat
- Install Operating System Updates. Be sure that the MS17-010 update is installed.
- If it is possible, disable (or better uninstall) the SMB v.1 service and block TCP 139 and 445 ports on your firewalls.
- Restrict perfc.dat file execution.
- Instruct your personnel to be extremely careful when dealing with incoming email and to not open attachments sent from outside the company.
- Make sure that your business crucial systems get regularly backed up.
- Use a properly configured anti-malware solution.
IOCs and Yara rules are accessible from here.
Our customers and KL ICS CERT subscribers will immediately be informed of all results and related information.
Note for the Kaspersky Lab product users:
Kaspersky Lab products detect the malware as:
UDS:DangerousObject.Multi.Generic Trojan-Ransom.Win32.ExPetr.a HEUR:Trojan-Ransom.Win32.ExPetr.gen
Our products that have the System Watcher component enabled are able to detect and prevent the initial infection attempts even without anti-malware databases properly updated.
System Watcher detects the malware as:
PDM:Trojan.Win32.Generic PDM:Exploit.Win32.Generic