25 September 2017
Infected CCleaner in ICS around the world
On 18 September 2017, Piriform, a software company, announced that its CCleaner utility, which is designed to optimize the operation of Windows, had been hacked. The following 32 bit versions of the software were compromised:
- CCleaner v5.33.6162
- CCleaner Cloud v1.07.3191а
A malicious program called Floxif had been incorporated in these versions of the utility. The malware collects data on infected computers, including their names, IP addresses, lists of installed and active programs and lists of network adapters, and sends the data collected to a third-party server located in the United States.
By 15 September, CCleaner developers had released updates of infected versions and, according to Piriform, the server to which the data was sent had been shut down by US law enforcement agencies.
According to Piriform estimates, infected versions of CCleaner are installed on 2.27 million computers, but there have been no known cases of damage being done to users.
Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) have seen almost 500 infected users in the industrial automation systems category.
Geographically, Floxif infections of industrial systems are distributed among different countries across the globe.
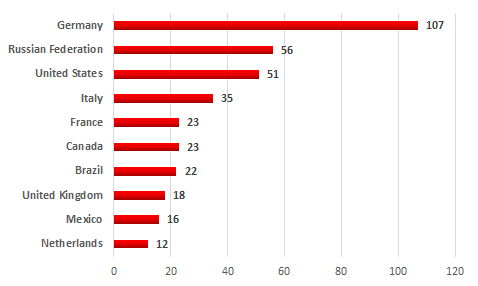
Top 10 countries with infected versions of CCleaner on industrial systems
Infected versions of the software were distributed from trusted domains and were signed with a valid digital certificate, making it harder for antivirus solutions to detect the malware.
Kaspersky Lab products are currently able to “cure” infected files by removing the malicious program’s body from them.
