28 May 2018
VPNFilter malware can be used to detect SCADA equipment
Cisco Talos researchers have detected new malware, which has been dubbed VPNFilter. To date, the malware has infected at least 500,000 routers and network-attached storage (NAS) devices in 54 countries of the world. The list of infected devices includes:
- Linksys E1200, E2500, WRVS4400N;
- MikroTik RouterOS for Cloud Core routers: versions 1016, 1036 and 1072;
- NETGEAR DGN2200 R6400, R7000, R8000, WNR1000, WNR2000;
- TP-link R600VPN;
- QNAP TS251, TS439 Pro and other QNAP NAS devices running QTS software.
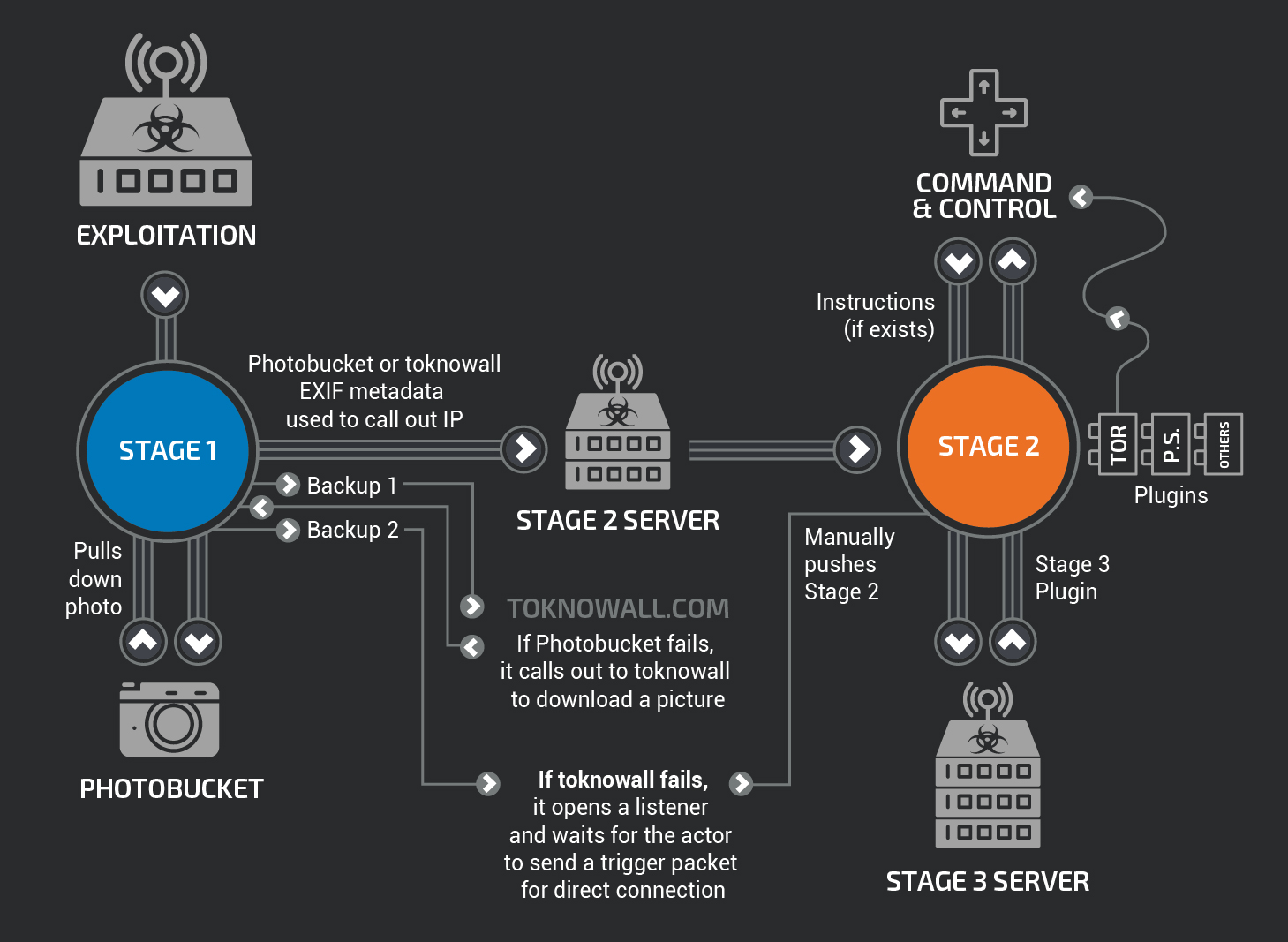
The VPNFilter malware has a sophisticated modular architecture with components that implement various functions at three main stages of its operation:
- At stage 1, a device is infected. According to Cisco Talos experts, in order to infect devices the malware exploits various known vulnerabilities, but the exact infection vector is currently not known. At the time of infection, a component designed to survive the device’s reboot is installed. The component can download additional modules of the malware. According to Symantec experts, the only way to remove VPNFilter at this stage is to perform a hard reset of the device.
- The stage 2 module is designed to collect data, execute commands and control the device. The component’s capabilities include modifying critical parts of the device’s firmware, rendering the device unusable.
- Stage 3 involves downloading additional components that collect network traffic and intercept packets, monitor Modbus SCADA protocols, and communicate to the command server over the Tor network.
After infecting a device, the malware can download further malicious programs usinf several different methods.
First, the malware attempts to access a gallery on Photobucket.com, downloading the first image on the page and extracting the download server’s IP address from six integer values for GPS latitude and longitude in the EXIF information. As Kaspersky Lab experts found out, the Photobucket.com galleries used by VPNFilter have been deleted, so the malware can no longer use this mechanism.
The second method is to extract an image file from the hardcoded domain toknowall[.]com. The domain has now been seized by the FBI.
And finally, if these attempts are unsuccessful, the malware goes into passive backdoor mode, in which it monitors network traffic on the infected device, listening for the attackers’ commands.
VPNFilter workflow (source: Cisco Talos)
This means that the information security community should keep close tabs on VPNFilter, because the malware can be used to steal account credentials, detect industrial SCADA equipment and conduct various attacks involving infected devices united into a botnet, to the point of depriving hundreds of thousands of users across the globe of internet access. In addition, It contains a destructive payload which is capable of rendering infected devices unbootable.
According to experts, the malware uses a broken (or incorrect) RC4 implementation which has been observed before with the BlackEnergy malware. However, the malware cannot be conclusively attributed to that APT group based on this indicator alone, even though Black Energy is known to have deployed router malware going back as far as 2014.
Sources: Cisco Talos, Symantec, Kaspersky Lab