06 August 2018
APT group called RASPITE attacks industrial enterprises
Dragos has published information on a newly-identified APT group, which it calls RASPITE. According to Dragos researchers, the group, which has been active since 2017, targets industrial enterprises in the US, as well as Europe, the Middle East and East Asia.
To date, RASPITE has limited its activity to gaining access to electric utility enterprises’ networks and has not demonstrated any capabilities related to disrupting the operation of industrial control systems (ICS).
Dragos reports that to gain initial access to target networks, RASPITE uses watering hole type attacks. The attackers modify sites visited by potential victims by embedding special links into these sites. The links lead to resources that initiate SMB connections in order to harvest users’ credentials. After that, the group uses scripts to deploy a malicious service on the system under attack, which beacons back to the infrastructure controlled by RASPITE, providing the attackers with remote access to the victim machine.
Dragos experts believe that the operations of RASPITE overlap significantly with those of Leafminer, a group on whose activity has recently been reported by Symantec.
It its report, Symantec provides data on the Leafminer group’s activity against government organizations and businesses in the Middle East. The group’s victims are known to include organizations from Azerbaijan, Israel, Lebanon and Saudi Arabia.
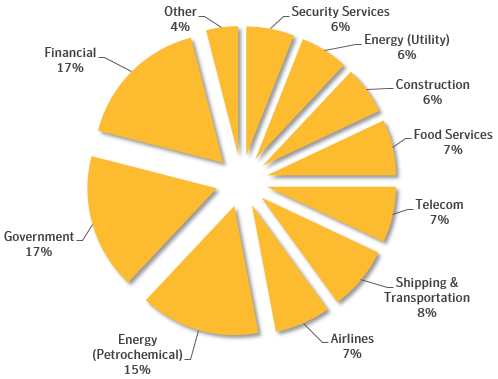
During their investigation, Symantec experts discovered a list of 809 targets scanned by the group. The list is written in the Iranian language Farsi and groups targets by geography and industry. Targeted industries include energy, government, finance, shipping & transportation, etc. Targeted regions include Saudi Arabia, United Arab Emirates, Qatar, Kuwait, Bahrain, Egypt, Israel and Afghanistan.
Figure 1 –Distribution of Leafminer targets by industry (Source: Symantec)
To carry out its attacks, the threat actor uses various publicly available and custom tools, exploits, watering hole tactics and brute-force/dictionary login attempts. The Leafminer group’s arsenal includes the notorious EternalBlue exploit, as well as a modified version of the widespread Mimikatz tool.
Symantec experts believe that the group may have links to the Iranian government, but there is no direct evidence to support this.