17 April 2020
New ransomware attacks on industrial enterprises
On the night of April 7-8, DESMI, a Danish manufacturer of pumping solutions for marine and industrial applications, suffered a ransomware attack. No information is available on the malware used in the attack.
According to an official statement, the attack affected the company’s communications systems, including email, which had to be temporarily disconnected. By April 14, DESMI managed to recover these systems. The ERP and financial systems were not affected. This enabled the company’s production sites in China, India, America, and Denmark to continue working as normal, with only minor disturbances.
The company’s management declared they would under no circumstances pay a ransom for recovering their data. The company also believes that data may have been stolen from their information systems as a result of the attack and that criminals would try to misuse that data.
DESMI has reported the incident to the Danish authorities and the police and has involved external experts in the investigation.
Another ransomware attack was reported on April 14. The victim is Energias de Portugal (EDP), a large Portuguese energy company. The attack, which involved the Ragnar Locker malware, left the company’s systems encrypted. Moreover, the cybercriminals claim to have stolen 10 TB of sensitive company files before encrypting the data. They now threaten to make that information public unless they are paid a ransom of 1580 BTC (about $10.9 million).
Various malware operators adopted the extortion method based on threatening to publish stolen data in late 2019. The first to make use of this technique were the operators of Maze and Sodinokibi (REvil) ransomware.
To prove that they really hold sensitive information belonging to EDP, Ragnar Locker operators published some of the stolen data, including employee account names and passwords.
According to the ransom note, the attackers also have confidential information on the company’s billing, contracts, transactions, clients and partners.
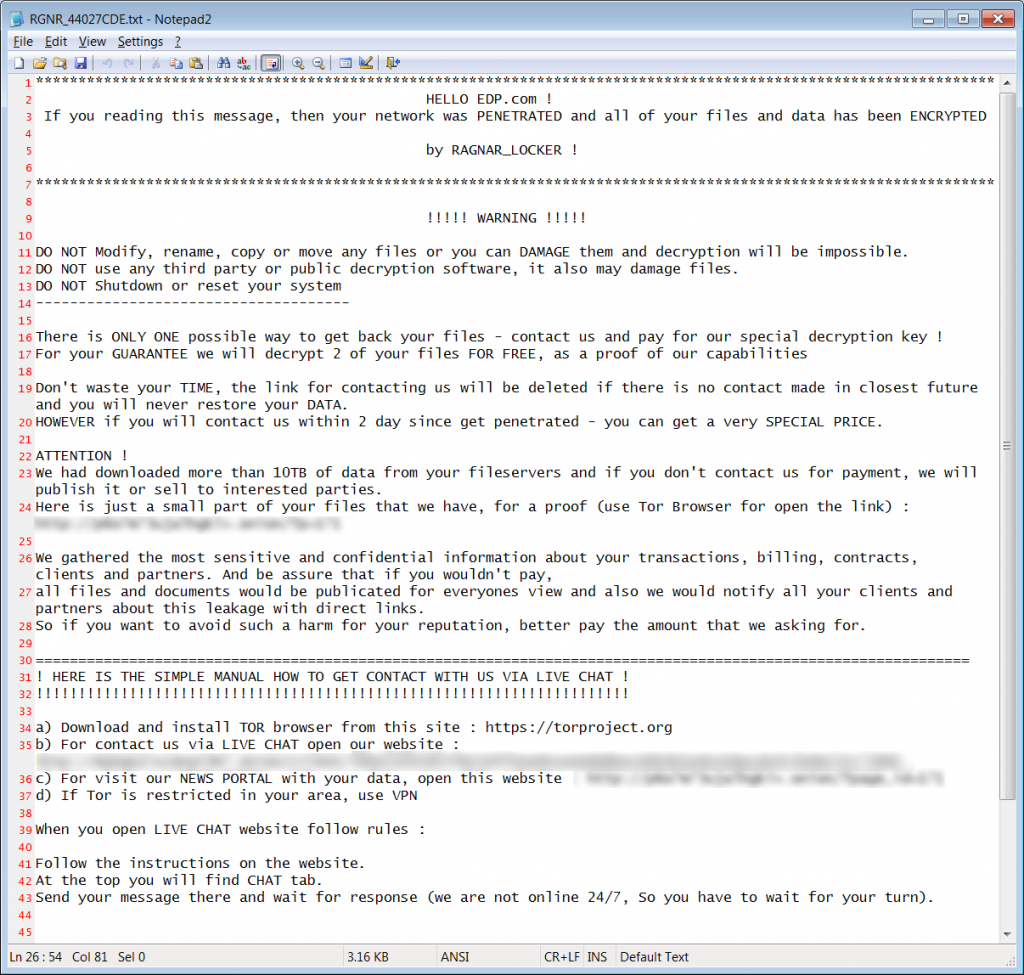
What catches one’s attention in the ransom note is the greeting, which includes the name of the company under attack. After analyzing different samples of the ransomware, we concluded that the entire text of the ransom note is created specifically for each individual victim, including the part describing the stolen data. This means that the attackers create the malicious program’s executable file, into which the ransom note is embedded, in the process of carrying out the attack.
Another distinguishing feature of Ragnar Locker is that the malware checks the language used by the operating system before encrypting files. If Ragnar Locker is running on a system that uses a localization specific to some countries of the former USSR, the ransomware terminates.
Since Ragnar Locker attacks are targeted, it can be assumed that the attackers break into their victims’ networks using methods that are typical of this class of attacks: carefully crafted spear phishing emails, brute-forced user account credentials for RDP connections, and exploitation of vulnerabilities on internet-facing systems or the organization’s web server.
After infecting one computer in the organization, the attackers conduct reconnaissance on the enterprise network, seeking to find and infect the systems that are the most critical for the company’s business processes. At this stage, they also steal the victim organization’s data.
After launching, the malware deletes all Windows shadow copies to make recovering data more difficult. Ragnar Locker also terminates some processes, including those of databases and backup utilities to be able to encrypt their files and those of anti-malware solutions for self-defense purposes.
To ensure that the malware does not crash the system, the malware does not encrypt files required for the system to boot up or files located in system or browser folders.
The extension of each file that is encrypted is changed to .rgnr_<%random7%>, where <%random7%> is a random string of 7 characters. When the encryption process is completed, the user is shown the ransom message described above. Depending on the version of the ransomware, the user can be offered the following options for contacting the attackers: sending an email to the address specified, using a channel in the TOX messenger or using an online chat on the website specified.
Sources: DESMI, BleepingComputer
