27 January 2021
From buffer overflow to switchboard setup errors: vulnerabilities in building operation software by Schneider Electric
Two vulnerabilities, CVE-2021-22697 and CVE-2021-22698, have been identified in Schneider Electric’s EcoStruxure Power Build – Rapsody. Both are rated at 7.8 on the CVSS 3.0 scale.
The product is low-voltage switchboard configuration and quotation software. It is normally used as part of building operation systems and is not designed for use in critical infrastructure.
The first vulnerability, CVE-2021-22697, is a use-after-free flaw. If certain conditions are met, such flaws can be exploited to execute arbitrary code in the application’s context. The second vulnerability, CVE-2021-22698, is a stack buffer overflow flaw, which can also lead to arbitrary code execution.
The dangers behind these two vulnerabilities lie in the possibility of unlimited file uploads, including malicious SSD (system specification description) files.
An SSD file contains electrical installation specifications, including single-line diagrams, functions, connections to logical nodes, such as IEDs (intelligent electronic devices), HMIs (human-machine interfaces), gateways, and so forth. This specification is analyzed together with descriptions of IED devices in ICD (IED Capability Description) files. The system configurator uses these two types of files to assign logical nodes to specific devices and to generate an SCD (Substation Configuration Description) file. The SCD file contains the configurations and settings for all smart (intelligent) devices installed on the substation.
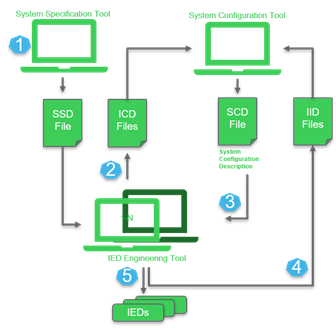
A spoofed SSD file can lead to a variety of consequences. However, a good understanding of these consequences can only be obtained after performing additional analysis of all the software used to configure the electrical installation, as well as making further assumptions about how commissioning and start-up is organized. It is most likely that a damaged or compromised SSD file will result in setup errors that engineers might not spot immediately and that will require additional time to fix.
Over the past few months Schneider Electric has issued several advisories on vulnerabilities in EcoStruxure™ products: SCADA telemetry software for EcoStruxure™ Geo SCADA Expert, EcoStruxure™ Operator Terminal Expert and Pro-face Blue HMI systems for Windows. The previous security advisory for EcoStruxure™ Building Operation products was released in November 2020. Clearly, the vendor is focusing on security for this product line.
However, it is important to note that the way the vulnerability information is presented might confuse the target audience. For instance, the vendor describes these vulnerabilities as follows:
One as a CWE-434 type vulnerability: Unrestricted Upload of File with Dangerous Type vulnerability exists that could allow a use-after-free condition which could result in remote code execution when a malicious SSD file is uploaded and improperly parsed.
The other as a vulnerability of the same type: Unrestricted Upload of File with Dangerous Type vulnerability exists that could allow a stack-based buffer overflow to occur which could result in remote code execution when a malicious SSD file is uploaded and improperly parsed.
It can be concluded from the above descriptions that uploading a malicious SSD file is the attacker’s primary action. However, it is unclear how a use-after-free condition or a stack-based buffer overflow can be the result of uploading an SSD file. In our opinion, the classification of these vulnerabilities as CWE-434 is not quite appropriate. We believe CWE-416 (Use After Free) and CWE-121 (Stack-based Buffer Overflow) would be a better fit for the first and second vulnerability, respectively. As for the possibility of uploading an arbitrary file, this is not a vulnerability in and of itself, but a potential consequence of exploiting vulnerabilities of the above types due to the intended use of the product. A correct and accurate description of vulnerabilities is necessary for choosing the proper mitigation strategy.
Vulnerability Information publication date: January 12, 2021
Sources: Schneider Electric, Kaspersky ICS CERT

