12 December 2022
Unusual penetration techniques – in the wild and in Red Team research
Back in September we recorded a new episode for our Russian language ‘Change your password’ podcast on location at the Sayano-Shushenskaya hydroelectric power plant – deep in Siberia. Naturally, we were talking about ICS cyberthreats, changes in the threat landscape and so forth.
One question continues to niggle at me – unusual attacks on large businesses, specifically industrial facilities. Security expert Alex Gostev, who moderated our chat, asked us to discuss unusual attack vectors. I brought up how USB sticks with malware were scattered around office entrances. Alex retorted that today this is an urban legend.
So, I got thinking and remembered various attack vectors and tricks we have researched in the Red Team, or discovered during investigations or things I have heard from teammates, or read online and so forth.
Today I would like to talk about some of the tricks and methods I have seen used to gain that all important initial access to remote systems. Specifically, the unexpected and unusual.
USBs in the mail
In early 2022 the FBI released an alert about how the group FIN7/Carbanak is sending out malicious USBs to companies in various sectors including logistics, insurance and the military industrial complex. If these are connected to workstations the threat actors can get remote access using the malware.
Not new in itself, but in this case the malicious USBs were disseminated using legitimate mail carriers – United States Postal Service and United Parcel Service. Some of the packages were sent purportedly from the US Department of Health and Human Services and contained a letter with references to new COVD-19 recommendations.
In August 2022 we learned of a case in England where packages spoofing Microsoft Office Professional Plus were sent out. The packages contained malicious USBs.

When the USB was attached a message popped up on screen telling users that the machine is infected with malware and that they should immediately call Microsoft at the number provided. In reality, the phone number belonged to the criminals. The threat actors got access to the computer using Team Viewer and thus got full access to all data on the local machine.
Ocean’s Thirteen attack Antwerp port
Now let’s go back in time a bit.
From where I sit, I think one of the more thrilling campaigns where removable media was used, occurred in Antwerp back in 2011 – 2013. In 2013 Europol revealed that the Antwerp port had been under attack for two years.
I’m talking about the activity of a multinational criminal group with members from the Netherlands, Turkey, Latin America and other countries. The drug smuggling group was named after the movie Ocean’s Thirteen.
The smugglers needed to steal data about the containers used to transport their drugs, so cyber tools were required. They needed to harvest information about where the containers were located, as well as the digital PIN code used by drivers to confirm their right to receive the containers and the cargo. The stolen PIN codes were passed on to the group managing the drug transit in Belgium and the Netherlands. This group provided their drivers with false papers and the access PIN code and sent them to the port to receive the cargo before the legal owners could get at it.
In June 2013 Europol announced that the attack had begun in June 2011. The exact amounts of drugs that had been smuggled thorough this tunnel during this period is not known, but it is believed to be no less than 2 tons of cocaine and 1 ton of heroin. During raids conducted in Belgium and the Netherlands, the police seized hacking equipment, firearms, bulletproof vests, and large sums of money, as well as drugs.
The attackers used spear phishing to deliver malware to port officials and transport agents during phase one of the attack. Some of the phishing emails were messages containing an attachment and a request to update Adobe Reader, for instance. The phishing attacks were launched from Dutch IP addresses. Once the victim computers were infected the malware was used to steal authentication credentials to gain access to the IT systems the threat actors needed to penetrate.
Eventually the target organizations implemented cyber security measures to close down existing channels for data theft. The smugglers then moved on to new tactics for stealing the PIN codes. The second attack began with hacker attacks on port and other logistics websites. The criminals were once again attempting to break into the networks to harvest the necessary information.
Once the hackers decided that the second approach was not very effective, they implemented a third type of attack. The investigators discovered that well known Belgian cyber security experts, ‘ethical hackers’, the ‘best’ pen testers and other ‘top’ IT experts played pivotal roles in this new attack. In fact, one person had National Secret / NATO Secret / EU secret clearance.
In the third attack, the cybercriminals gained physical access to company offices and installed special equipment for intercepting and stealing data. This included USB keyloggers disguised as external hard drives or USB keyboard connectors, both of which contained miniature Wi-Fi transmitters.
The criminals used these interceptors to harvest authentication credentials needed for system access, as well as container PIN codes. To capture network traffic they used PWNIE devices which worked like KVM switches and had Linux microcomputers inside with Metasploit installed.

These devices redirected company network traffic through a 3G connection. Some sources believe that the criminals needed to study local processes in detail to then go from simple observation to direct control of company logistics systems in real time.
Crimesite.nl asserted that the Trojans and keyloggers used in the attacks sent data to a US based server. Belgian authorities were able to extradite this data. The data pointed at the direct involvement of Latin Americans in the attack. Some of the names pointed to people attached to computer security companies in Latin America, people who also appeared in various publications about hacker scandals in politics and in organized criminal circles in Columbia.
Moreover, when the police searched the apartment of one of the gang leaders they found professional spy equipment: devices for blocking police listening equipment and IMSI catchers. The latter look like normal notebooks with a connected antenna, but they function as base cellphone stations. They can be used to intercept any cellphone conversations within a certain radius, including police and other officials. Normally, the caller doesn’t notice that they are being overheard. As a rule, IMSI catchers are issued to police and secret services in very limited quantities. No one, not the Belgian or Dutch police nor the media explains what this equipment was used for and whether it was, in fact, used in the attacks on the Antwerp port companies.
This particular incident is one of the first such to be discussed publicly. It is important because ‘ordinary’ criminals, not cybercriminals, were using cyberattacks as a tool to organize a crime – delivering large quantities of drugs. The collaboration between organized crime and cybercriminals resulted in a new and effective operation, both from a technical and an organizational point of view. Before only government intelligence agencies had been able to conduct such operations.
Drones deliver access points
Private drones took off in 2013 literally and figuratively and we immediately see drones put to use for gaining initial network access.
In 2013 Samy Kamkar showed us the drone he had modified and equipped with a Raspberry PI, which he used to intercept other drones that use Wi-Fi connections.
In 2015 a group of iTrust researchers in Singapore demonstrated how to hack wireless printers in an office building. They wrote a couple of apps which hijacked documents sent to wireless printers without any authentication. They uploaded the apps to a jailbroken Samsung smartphone and attached the phone to a DJI drone.
In 2017 we have researcher Naomi Wu revealing her version of a drone that could be used to gain illegal access to the target’s internal network by compromising the Wi-Fi connection.
Finally, in October 2022 IT security expert Greg Linares opened up about a real world cyberattack on a US financial company using drones. The attackers used two modified drones – DJI Matrice 600 and DJI Phantom, equipped with a WIFI Pineapple device, a Raspberry Pi, a set of batteries, a GPD pocket laptop, a 4G modem, and another Wi-Fi device. Greg noted that such attacks had been detected in the wild before.
Bribing insiders
In 2020 the world was stunned by an attempt to bribe a Tesla employee to facilitate malware installation. This was not the first known insider bribery attempt, but interestingly enough in this case the attempt was made not by a government connected APT, but, most likely, by a criminal group specializing in extortion and selling stolen data.
Insider threats have always been around. For instance, in 2020 a General Electric employee was discovered to have stolen over 8 000 confidential documents over a period of 8 years. The information was used to create a competitor.
So, as we can see from just these examples, insider threats are thriving and we predict that we will see many more going forward.
Attacks via vulnerable drivers
The approach in Bring Your Own Vulnerable Driver (BYOVD) attacks is rather interesting: we see the attackers installing a vulnerable driver on the target system during the attack. These attacks are difficult to detect because the criminals use legitimate ‘trusted’ software with digitally signed code, which is often not scanned thoroughly by automatic cybersecurity solutions. What is worse is that such trusted solutions often have higher privileges – working on the OS kernel level.
Interestingly, Microsoft recommends blocking vulnerable drivers used in attacks with the HVCI technology, which has a number of undocumented limitations, such as block list format compatibility issues and automatic updates not launching with Windows Updates. All of this means that BYOVD is an effective vector for attackers.
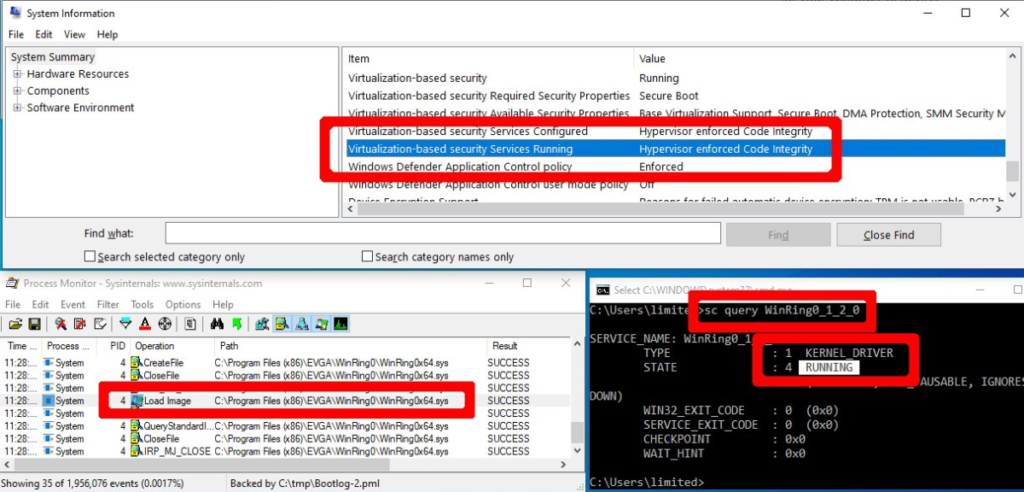
Eset provides some interesting research on such attacks, which they presented at VB 2022 (Virus Bulletin conference). At the end of 2021 the Lazarus APT group used BYOVD and the CVE-2021-21551 vulnerability in a legitimate and signed Dell driver. Unlike other APTs where BYOVD was used, this instance is unique, because the group used a rather complicated set of methods to disable security monitoring interfaces, techniques to change Windows kernel variables and kernel callbacks. None of these have been seen before in any other malware.
It is worth pointing out an interesting detail – in our recent research we discovered some traces of these same techniques targeting the same vulnerable dbutil driver, but in our case it was another group – APT428.
Gemalto’s Sentinel LDK
We discovered and tested this attack vector in our lab in 2017 – 2018. In some sense, it combines two of the attack vectors described above: installing a vulnerable legitimate driver on the target system and unusual use of external devices. The most interesting feature in this attack vector is how these devices were used. There was neither any malware nor any vulnerable legitimate code stored on the device. The connections are simply a trigger for the installation of a fully functional legitimate backdoor from a totally legitimate source.
We are very happy not to have seen this attack vector in the wild. Yet. A sufficient amount of time has already passed since we reported this issue and the vendor fixed the vulnerabilities we had discovered, so we can only hope that the fix has reached the vast majority of vulnerable systems. And we are daring to talk more openly about one of the exploitation methods we have identified.
Let’s take a look at our research. The product in question was a hardware and software combo: A USB token and some drivers and software that was installed on computers to work with license keys. The USB token needed to be connected to a PC or server on which the relevant license was required.
Some such USB tokens are listed in the table below:
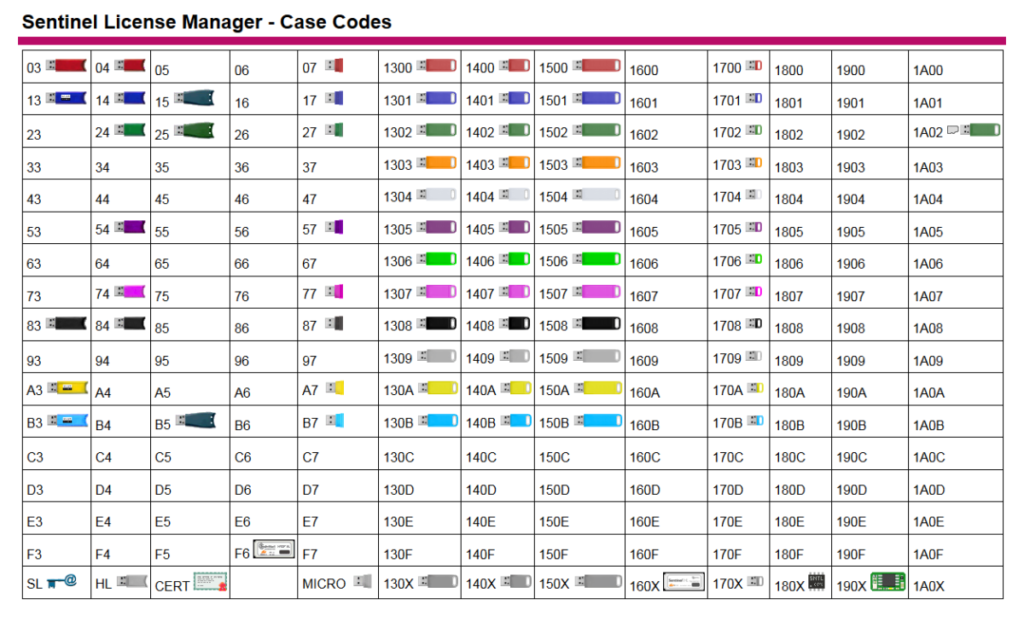
During our research into this license manager we identified about 20 vulnerabilities, among which, in addition to classic vulnerabilities, we found some odd functionality which could be used to conduct an effective attack on the targeted system.
In short, the attack scenario is as follows:
- The attacker needed to connect a USB token to a target Windows system which was connected to the Internet. The attacked computer could be blocked and the attacker did not need to unblock it (aka the user password was not required).
- The driver was installed automatically by Windows Update and services and was automatically launched by the hasplms.exe process with SYSTEM rights. Port 1947 was opened (when Gemalto software was installed as part of a third party installation file or from the Gemalto website, port 1947 was also added to the Windows firewall exceptions list.)
- Once port 1947 was open, the remote attacker could use a “poorly documented API function” that allowed him to turn access to the web interface on and off. The interface could be used to change setting in the software part of the solution.
- This included being able to change settings on the internal proxy server for updating language packs.
Fun fact: standard protection against binary vulnerabilities (ASLR, Stack Cookie, Stack Canary and so forth) was disabled by the developers. And the binary vulnerabilities in these language packs allowed the threat actors to easily execute arbitrary code remotely with SYSTEM rights.
- Once changes were implemented on the proxy server, the service’s internal logic could be used to harvest the NTLM hash for the user account which had been used to launch the hasplms.exe process (SYSTEM).
The general attack workflow is depicted below:
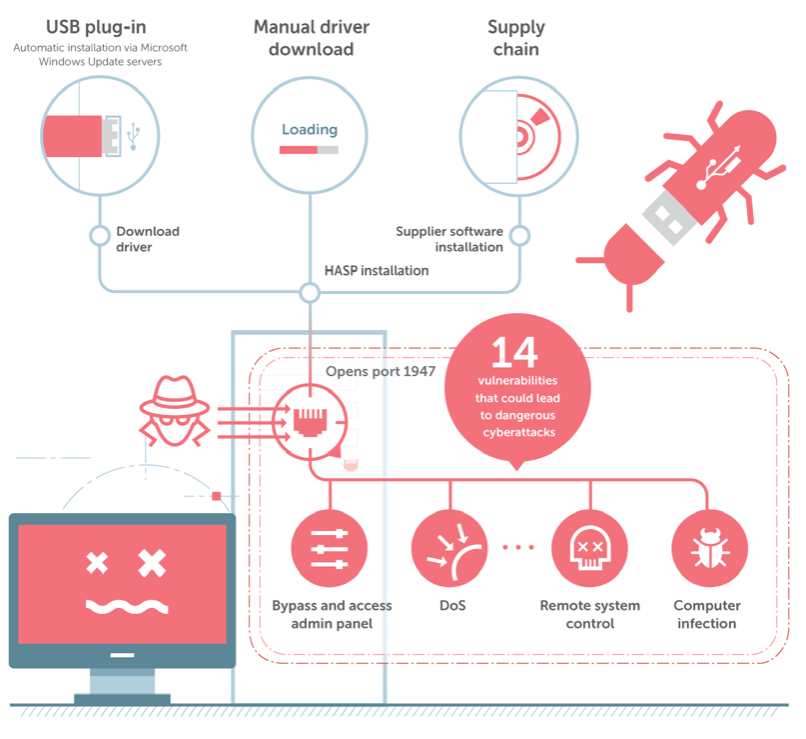
The entire functionality allowed attackers to get remote access undetected, execute arbitrary code, and to mask their presence. And all that was needed to gain access to the computer was to attach a USB token from the above list (in the table), wait a couple of minutes and detach the token. As noted above, the computer could even be blocked during this process. What we have here is legitimate functionality that has all the hallmarks of a backdoor.
Conclusion
As perimeter defenses improve attackers will look to social engineering and will increasingly seek unusual penetration methods for initial access. Security researchers and cybersecurity solution developers will need to detect and study new attack vectors and work to forestall the criminals by creating and releasing protection from new attack vectors, including ones which have only been tested in labs and have not yet been seen in the wild.
If industrial organizations do not wish to become easy targets, their employees need to keep up, because they are desirable targets for the more “advanced” criminals out there. Information security teams need to constantly monitor changes in the threat landscape: study research findings, organize and run training sessions for employees, focusing not only on cybersecurity basics, but also on repelling the more unusual and tricky attack methods. It is crucial not only to study the theory, but also to develop practical and effective skills in thwarting initial penetration, as well as hands on experience in proactively searching for and detecting threats, containing attacks and investigating incidents.
Overall, I hope that my little excursion down memory lane proves useful to you, not just to me. Hopefully, my reminiscing and analysis will get my readers thinking, for instance about building out an awareness training initiative, including how to choose trainers and how to evaluate training materials.

