22 February 2018
3.3% of ICS computers attacked by miners during the past year
On February 20, it was reported that Tesla’s cloud servers had been hacked in order to use part of their capacity for mining the Monero cryptocurrency. Cybercriminals had attacked the Kubernetes framework that is part of the leading electric car manufacturer’s infrastructure and infected it with cryptocurrency mining malware.
Earlier, on February 8, SecurityWeek reported that the computer network of a wastewater facility in Europe had been infected with malware that has cryptocurrency mining functionality. The malware infected four servers running Windows XP and CIMPLICITY SCADA software from GE Digital. The malware slowed down the HMI and SCADA servers used to monitor industrial processes.
This is not nearly the first time a miner has attacked an industrial enterprise’s infrastructure.
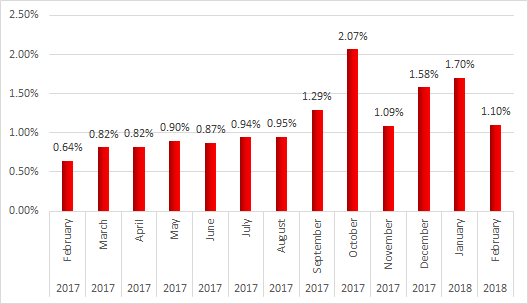
According to Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT), during the period from February 2017 to February 2018, miners attacked 3.3% of computers that are part of industrial automation systems. Such attacks have been on the increase since September 2017.
Percentage of ICS computers attacked by cryptocurrency miners
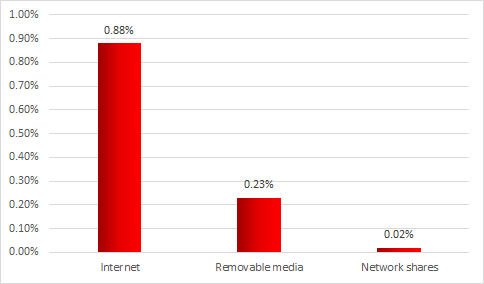
In most cases, the malware entered the industrial network infrastructure from the internet, removable media or enterprise network folders.
Sources of ICS computer infection with miners
Percentage of systems attacked
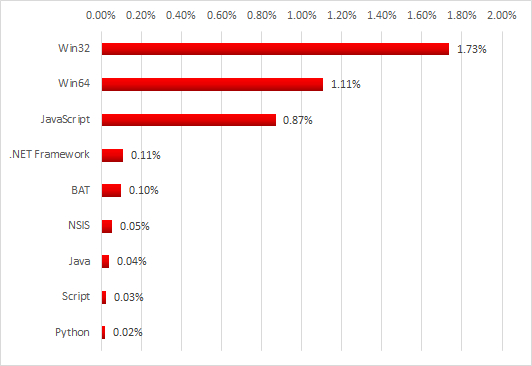
Cryptocurrency mining malware platforms
Percentage of systems attacked
In most cases, miners detected on industrial networks install and run stealthily and use obfuscation.
The main problem associated with cryptocurrency mining malware is that it increases CPU load and consumes bandwidth. For industrial automation systems, which operate in real time and for which response time is critical, this is associated with certain risks, including a reduced level of control over the enterprise’s industrial processes and a threat to their stability.
Source: Kaspersky Lab