19 October 2018
New GreyEnergy malware attacks industrial networks
ESET researchers have identified previously unknown malware that had been used in targeted attacks, primarily on industrial networks of various organizations in Central and East Europe. The new malware and the criminal group behind these cyberattacks have been dubbed GreyEnergy. The group’s activity primarily targets companies in the energy sector, transportation and other critical infrastructure related industries.
In the process of analyzing GreyEnergy, ESET experts identified conceptual similarities of the new malware with the BlackEnergy malware, which was used in attacks on the Ukrainian power grid in 2015. According to ESET researchers, there are some indications of a possible connection between the GreyEnergy group and the activity of the TeleBots criminal group, which is known for numerous destructive attacks, including 2017 attacks involving NotPetya and BadRabbit malware.
ESET researchers closely followed the activity of the GreyEnergy group for several years. The malware was first spotted in late 2015 in an attack on an energy company in Poland. The most recent known instance of GreyEnergy being used was recorded in the middle of 2018.
The GreyEnergy malware is based on a modular architecture, enabling attackers to use different functionality by connecting the relevant DLL libraries as necessary:
| Module name | Module functionality |
| remoteprocessexec | Injecting a PE binary into a remote process |
| Info | Collecting information about the system, event logs, SHA-256 of malicious files |
| File | File system operations |
| Sshot | Capturing screenshots |
| keylogger | Harvesting keypresses |
| passwords | Collecting saved passwords from different applications |
| mimikatz | Mimikatz utility used to collect Windows credentials |
| Plink | Plink software used to create SSH tunnels |
| 3proxy | 3dproxy software used to create proxies |
In some cases, malicious modules are downloaded from the command-and-control server and loaded directly into memory, without being saved on the hard drive.
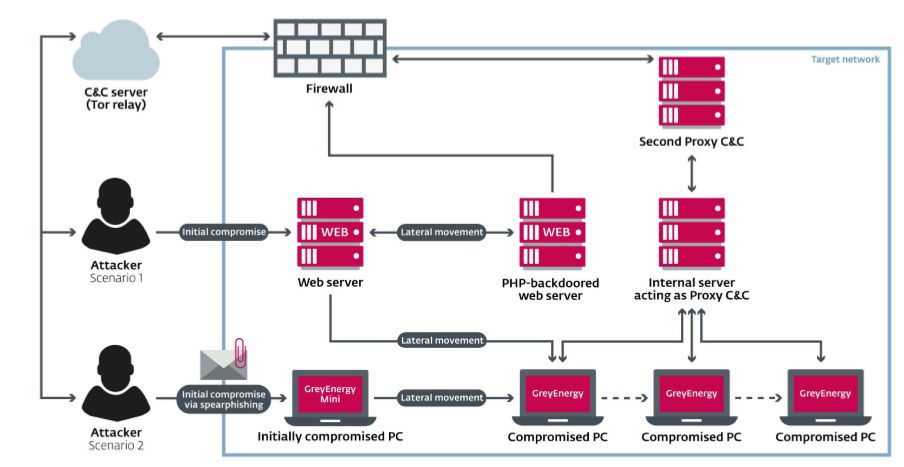
The main GreyEnergy infection vectors are phishing emails and the compromise of public-facing web servers with subsequent attempts to move laterally across the internal network.
Main scenarios of GreyEnergy attacks (Source: ESET)
GreyEnergy enables the attackers to collect user credentials, including for the purposes of gaining access to industrial systems and networks used to control industrial processes. Among other tools, the group uses publicly available utilities such as Mimikatz, PsExec, WinExe, Nmap, etc., to carry out its malicious network activity.
In the course of their research, ESET experts also discovered GreyEnergy samples signed with a valid digital certificate, which had likely been stolen from a Taiwanese industrial equipment manufacturer.
Source: ESET