10 January 2020
Dustman wiper attack on Bapco oil company
Bahrain’s national oil company Bapco has been affected by an attack involving Dustman malware. The incident occurred on December 29, 2019. The attack caused no severe consequences. Only some of the computers on the Bapco network were infected and the company was able to avoid disruption to its operations.
The attack was mentioned in a security alert published by Saudi Arabia’s National Cybersecurity Authority (NCA). The document reported the detection of a new malicious program that had been dubbed Dustman.
Dustman is wiper malware designed to delete (wipe) data from infected computers. An analysis of the malware revealed that Dustman is an upgraded and improved variant of the ZeroCleare wiper, which was discovered last fall and which has some similarities with Shamoon malware.
Both ZeroCleare and Dustman use a third-party driver, Eldos RawDisk, as well as a skeleton of the modified “Turla Driver Loader (TDL)” published on GitHub in March 2019. However, the techniques used in the Dustman attack are different from those used in ZeroCleare attacks. Dustman implements an optimization mechanism: while ZeroCleare uses two files to deliver the destructive capability and all needed drivers and loaders, Dustman uses only one executable file for this purpose. Another difference is that Dustman overwrites the volume and ZeroCleare wipes the volume by overwriting it with garbage data (0x55).
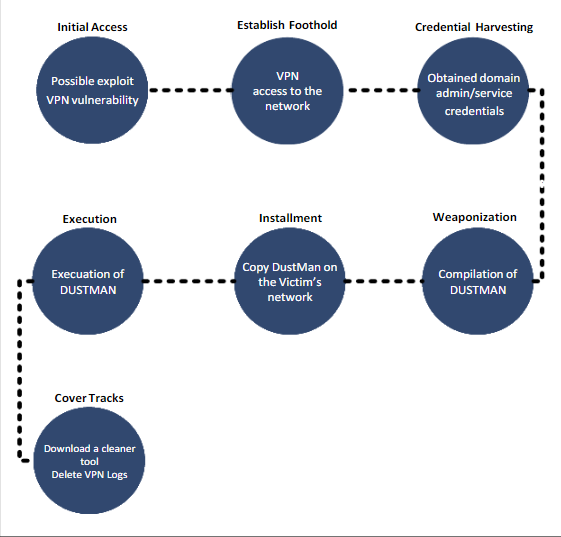
According to the report released by NCA, the attackers are likely to have gained initial access to the victim’s network by exploiting a remote execution vulnerability in a VPN appliance. Next, the threat actor gained access to the VPN server. After that, according to the NCA report, the attackers “obtained domain admin and service accounts on the victim’s network, which was used to run “DUSTMAN” malware on all of the victim’s systems. The attacker utilized the anti-virus management console service account to distribute the malware across the network.” The malware, together with a remote execution tool, PsExec, was copied to the antivirus management console server, which was used to launch Dustman.
Attack lifecycle (source: National Cybersecurity Authority)
Sources: ZDNet, Saudi Arabia’s National Cybersecurity Authority