09 December 2016
Vulnerability in Industrial Control software and quality of the patch management
Kaspersky Lab ICS-CERT is launching a series of articles devoted to vulnerability analysis across the world. The articles aim to highlight patch management problems in the ICS world. Each article will focus on one popular ICS vendor and known vulnerabilities according to the MITRE Common Vulnerabilities and Exposures (CVE) database.
The graphs below contain the following information:
- Vulnerable – percentage of ICS systems with vulnerable components;
- Not vulnerable – percentage of patched ICS systems;
- Possibly patched – inconsistent or partially patched ICS systems. Some files might be patched, other files still not.
This article covers vulnerabilities found in Rockwell Automation solutions from 2014 to 2016 and contains the following CVEs:
CVE-2014-0755 – RSLogix 5000 Password Vulnerability allows a local attacker to compromise user
passwords;
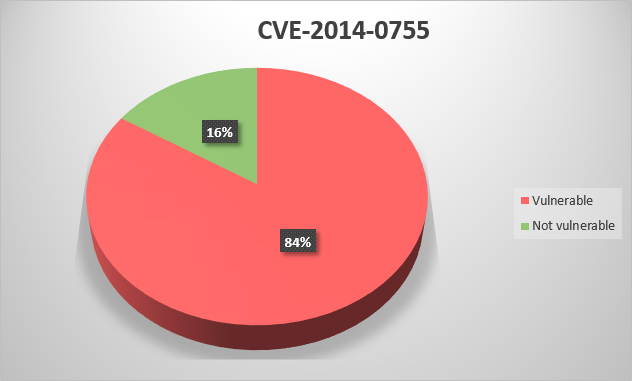
CVE-2014-5424 – Rockwell Automation Connected Components Workbench (CCW) before 7.00.00 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via an invalid property value to an ActiveX control that was built with an outdated compiler;
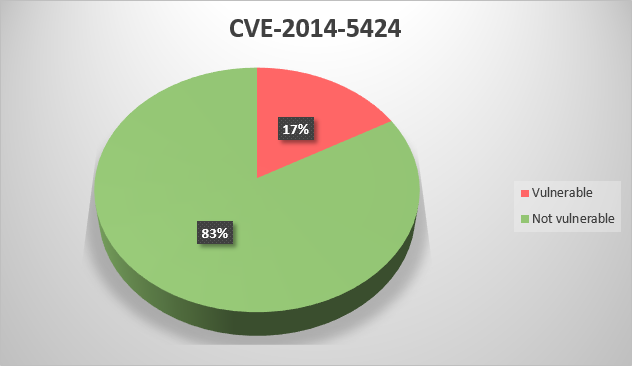
CVE-2014-9204 – Stack-based buffer overflow in OPCTest.exe in Rockwell Automation RSLinx Classic before 3.73.00 allows remote attackers to execute arbitrary code via a crafted CSV file;
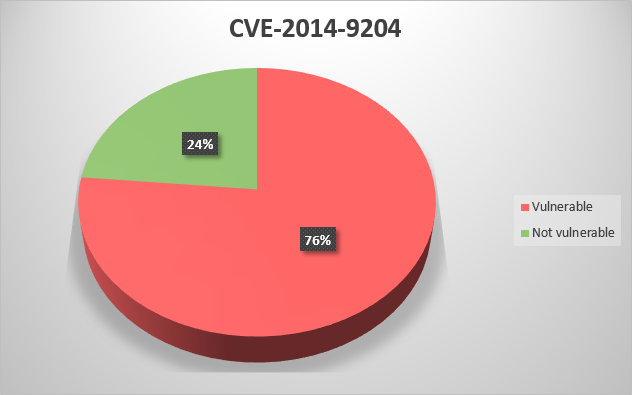
CVE-2014-9209 – Untrusted search path vulnerability in the Clean Utility application in Rockwell Automation FactoryTalk Services Platform before 2.71.00 and FactoryTalk View Studio 8.00.00 and earlier allows local users to gain privileges via a Trojan horse DLL in an unspecified directory;
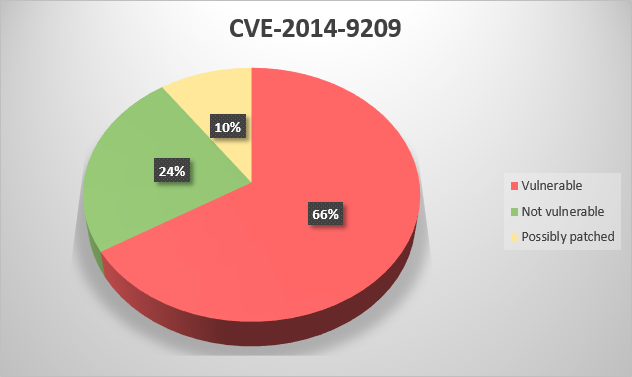
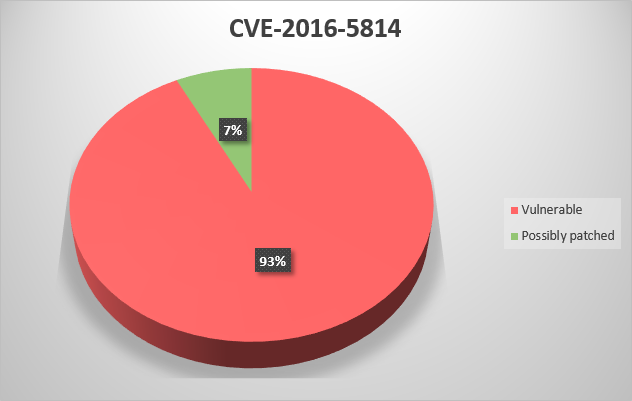
CVE-2015-1010 – Rockwell Automation RSView32 7.60.00 (aka CPR9 SR4) and earlier does not properly encrypt credentials, which allows local users to obtain sensitive information by reading a file and conducting a decryption attack;
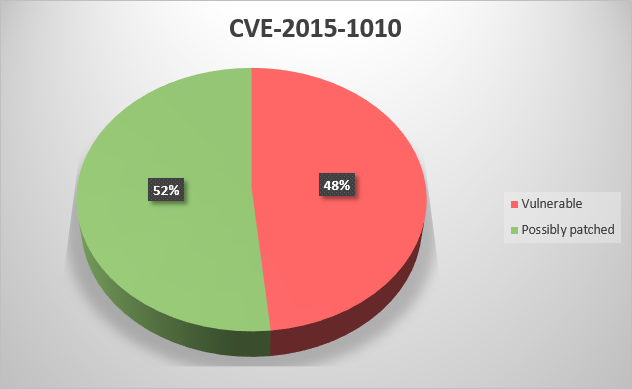
CVE-2016-2277 – IAB.exe in Rockwell Automation Integrated Architecture Builder (IAB) before 9.6.0.8 and 9.7.x before 9.7.0.2 allows remote attackers to execute arbitrary code via a crafted project file;
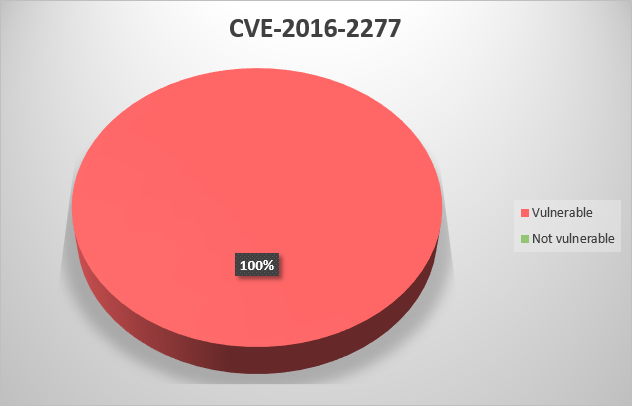
CVE-2016-4522 – SQL injection vulnerability in Rockwell Automation FactoryTalk EnergyMetrix before 2.20.00 allows remote attackers to execute arbitrary SQL commands via unspecified vectors;
CVE-2016-4531 – Rockwell Automation FactoryTalk EnergyMetrix before 2.20.00 does not invalidate credentials upon a logout action, which makes it easier for remote attackers to obtain access by leveraging an unattended workstation;
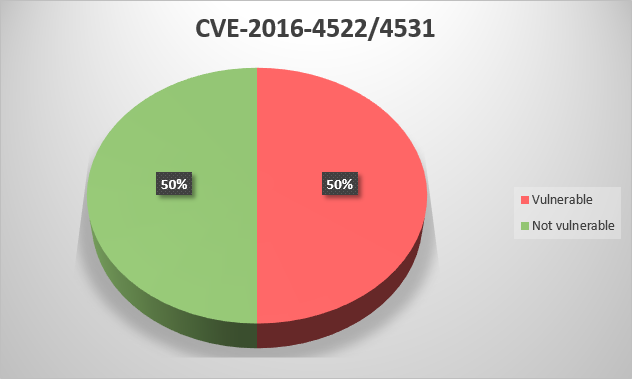
CVE-2016-5814 – Buffer overflow in Rockwell Automation RSLogix Micro Starter Lite, RSLogix Micro Developer, RSLogix 500 Starter Edition, RSLogix 500 Standard Edition, and RSLogix 500 Professional Edition allows remote attackers to execute arbitrary code via a crafted RSS project file.
The analysis presented above demonstrates that most of the Industrial organizations do not have effective vulnerability patch management and currently vulnerable to cyber-attack with use of the critical vulnerabilities. The intruder can take advantage of the missing patches and establish remote control over the vulnerable components.
However, not every Industrial organization can quickly update their systems. We recommend to review current state of the Control network cyber security, remove unnecessary connections to external and corporate network, enforce authentication and authorization policy, reduce use of portable devices from outside in Control network, review and adjust security policy for external vendor/contractors/service providers and prevent possible leaks of access credential.
For those who is interested to know more about their region, KL ICS CERT team can provide details per requested country. This information can be useful for local CERT/CIRT, Law enforcement agencies, other cyber security service providers working with Industrial organizations.
