24 April 2020
Threat landscape for industrial automation systems. Vulnerabilities identified in 2019
- 2019 Report at a glance
- Vulnerabilities identified in 2019
- APT attacks on industrial companies in 2019
- Ransomware and other malware: key events of H2 2019
- Overall global statistics – H2 2019
Vulnerabilities in various ICS components
The analysis of vulnerabilities was performed based on vendor advisories, publicly available information from open vulnerability databases (US ICS-CERT, CVE, Siemens Product CERT), as well as the results of Kaspersky ICS CERT’s own research.
Vulnerability information published on the US ICS-CERT website in 2019 was used as the source of statistical data for this report.
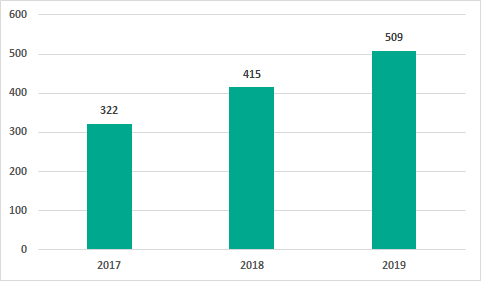
Number of vulnerabilities identified
In 2019, the number of vulnerabilities identified in different ICS components and published on the US ICS-CERT website was 509. This number has increased over the 2017 and 2018 figures. In our opinion, this increase relates to the increased attention of security researchers to the security of industrial automation solutions and does not mean that there has been a decrease in the quality of product development.
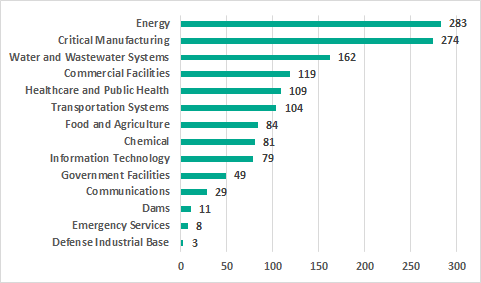
Analysis by industry
The largest number of vulnerabilities affect industrial control systems in the energy sector (283), systems used to control industrial processes at various enterprises categorized as critical infrastructure facilities in the US (274); and water supply and sewage systems (162).
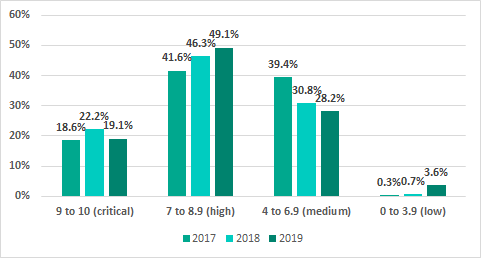
Severity levels of vulnerabilities identified
More than half of the vulnerabilities identified in ICS systems (358, compared with 284 in 2018) were assigned CVSS v.3.0 base scores of 7 or higher, corresponding to a high or critical level of risk. Two vulnerabilities were not assigned risk levels, since they are attributed to numerous CVEs and did not receive a unique CWE ID.
| Severity score | from 9- to 10 (critical) | from 7 to 8.9 (high) | from 4 to 6.9 (medium) | from 0 to 3.9 (low) |
|---|---|---|---|---|
| Number of vulnerabilities | 97 | 249 | 143 | 18 |
Compared with the previous year’s data, the proportion of vulnerabilities that have a high or critical severity score has grown.
The highest possible base score of 10 was calculated for vulnerabilities identified in the following products:
- Alaris Gateway Workstation
- Proton/Enterprise Building Management System
- Spectrum Power 4.7
- CODESYS V3 web server
- Relion 670 Series
- FlexAir
- RSLinx Classic
- WibuKey Digital Rights Management (DRM)
- PR100088 Modbus gateway
It should be noted that the CVSS base score does not account for the aspects of security that are specific to industrial automation systems or for the distinctive characteristics of each organization’s industrial process. This is why, when assessing the severity of a vulnerability, we recommend keeping in mind, in addition to the CVSS score, the possible consequences of its exploitation, such as the non-availability or limited availability of ICS functionality affecting the continuity of the industrial process.
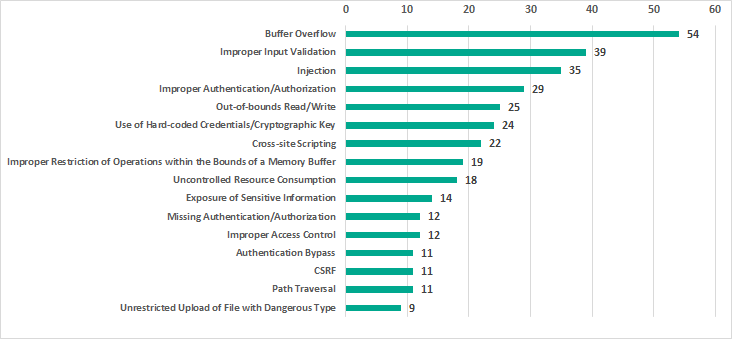
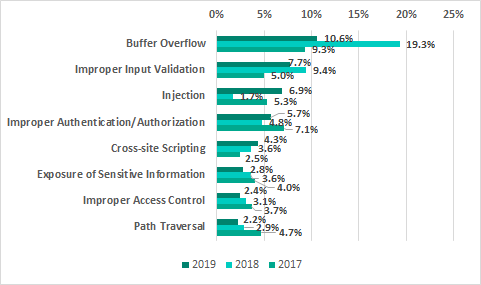
Types of vulnerabilities identified
The most common types of vulnerabilities in 2019, just like in 2018, include buffer overflow (Stack-based Buffer Overflow, Heap-based Buffer Overflow, Classic Buffer Overflow), improper input validation and injection (SQL Injection, Code Injection, Command Injection).
17.3% of published vulnerabilities affect authentication (Improper Authentication, Authentication Bypass, Missing Authentication for Critical Function) and access control (Access Control, Incorrect Default Permissions, Improper Privilege Management, Credentials Management).
15.5% of published vulnerabilities are web vulnerabilities (Injection, Path traversal, Cross-site request forgery (CSRF), Cross-site scripting). Compared with 2018 this number has increased by 5.5 p.p.
Exploitation of vulnerabilities in various ICS components by attackers can lead to arbitrary code execution, unauthorized control of industrial equipment and denial-of-service conditions (DoS) affecting that equipment.
It should also be noted that:
- Most of these vulnerabilities (420) can be exploited remotely without authentication,
- The majority of the vulnerabilities (480) can be exploited without the attackers having any specialized knowledge or high skill levels,
- Exploits have been published for 23 vulnerabilities, which increases the risk of malicious actors using them.
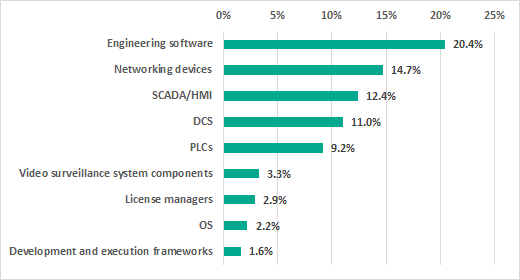
Vulnerable ICS components
The largest number of vulnerabilities were identified in:
- engineering software (103; 20%),
- networking devices designed for industrial environments (78;15%),
- SCADA/HMI components (63; 12%),
- DCS (56; 11%),
- PLCs (47, 9%).
Security issues in industrial automation systems are often due to vulnerabilities in third-party common software components used by vendors in many ICS solutions. Such components include operating systems (OS), license managers, modules implementing various security mechanisms, as well as frameworks used to develop and execute industrial control system software.
Vulnerabilities in operating systems
The operating system is one of the main components of any industrial automation system. Since vendors could be using the same operating system in various products, a single OS vulnerability will most often affect entire product lines.
For instance, in 2019 the security issues around the RUGGEDCOM ROX II OS meant that all of the Siemens RUGGEDCOM industrial devices based on this OS ended up vulnerable.
Additionally, multiple vulnerabilities discovered in the VxWorks real-time OS affected solutions from Rockwell Automation, Schneider Electric, Xerox and Dräger.
Another example of an OS vulnerability with sweeping security effects was the TCP SACL Panic vulnerability discovered in the Linux kernel. This vulnerability affected multiple Siemens products.
Vulnerabilities in license managers
In 2019 security researchers reported vulnerabilities in several license managers at the same time:
- Yokogawa License Manager Service
- Schneider Electric Floating License Manager
- RC-LicenseManager
- SafeNet Sentinel LDK License Manager
- FlexNet Publisher
License managers are often used in different solutions, therefore vulnerabilities in them can affect several industrial control products simultaneously. For instance, Yokogawa’s CENTUM VP distributed control system and their ProSafe-RS safety instrumented system (SIS) were both affected by vulnerabilities discovered in Yokogawa’s License Manager Service.
In a similar case, vulnerabilities in the Floating License Manager affected several Schneider Electric products simultaneously, including the EcoStruxure Control Expert engineering software, the EcoStruxure Hybrid Distributed Control System (also known as the Plant Struxure PES), Power SCADA Expert and others. Vulnerabilities in this license manager also affected Vijeo Citect and Citect SCADA from AVEVA, a Schneider Electric subsidiary. It is worth noting that the vulnerabilities in the Floating License Manager are in turn connected with multiple vulnerabilities in third party software — Flexera FlexNet Publisher.
In addition, products from several industrial vendors at once, including Siemens, Phoenix Contact, Sprecher Automation and COPA-DATA, were found to be affected by vulnerabilities in the WibuKey Digital Rights Management (DRM) solution.
Vulnerabilities in program development and execution frameworks
It is worth taking a separate look at the security of frameworks used by vendors for the development and execution of ICS software. Vulnerabilities were discovered in 2019 at the same time in several components of CoDeSys, an industrial automation software solution, including the web server, the communication server and the OPC UA server.
Vulnerabilities identified by Kaspersky ICS CERT
In 2019, Kaspersky ICS CERT experts continued their research on security issues affecting third-party hardware-based and software solutions that are widely used in industrial automation systems, internet of things (IoT) and industrial internet of things (IIoT) solutions, etc. A special emphasis was made on cross-platform solutions and open-source products. Such solutions and their components are widely used as standalone products or as part of commercial solutions.
Number of vulnerabilities identified
In 2019, Kaspersky ICS CERT identified 103 vulnerabilities in industrial, IIoT/IoT, and other types of solutions.
Every time we identified a vulnerability, we promptly notified the respective product’s vendor.
Possible consequences of exploitation of the vulnerabilities identified
In 2019, we divided vulnerabilities that can be exploited to execute code into two types:
- Execute Unauthorized Code or Commands – execution of code in the context of the application/execution environment. Examples: XSS, SQLi, XXE, ReadObject.
- Remote code execution (RCE) – execution of arbitrary machine code. Examples: execution of system commands / operating system commands and machine code.
It should also be noted that RCE often gives rise to various issues, including reading and modifying arbitrary folders and files, denial of service, etc.
In the statistics below, RCE and Execute Unauthorized Code or Commands are two distinct categories.
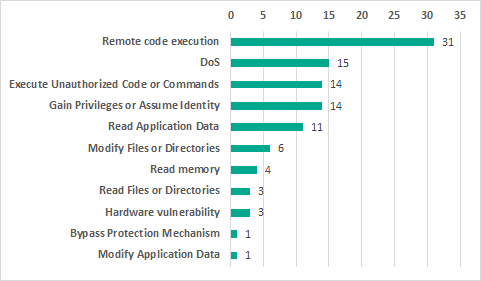
If exploited, 30.1% of the vulnerabilities identified could lead to remote code execution, 14.6% to a DoS condition. The exploitation of 13.6% of vulnerabilities could allow privilege escalation or session hijacking. The statistics also include three hardware vulnerabilities. If exploited, such vulnerabilities could provide the attackers with access to sensitive data due to the hardware platform or component base of the solution analyzed being insufficiently secure.
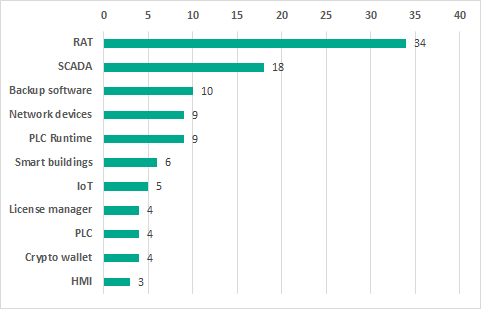
Results we consider the most important
| Software / solution | Number of vulnerabilities identified | Possible consequences of exploitation | Status |
|---|---|---|---|
| RAT based on VNC protocol | 34 | Vulnerabilities of different severity levels, some allowing arbitrary code to be executed both on the server side and on the client side | Vulnerabilities fixed by the vendor. Article published |
| License managers | 4 | Vulnerabilities of different severity levels allowing threat actors to develop an attack on the internal infrastructure | Vulnerabilities fixed by the respective vendors |
| Popular PLC execution environment | 9 | The vulnerabilities identified are potentially the most destructive for the industrial process, because the exploitation of such vulnerabilities is difficult to detect. The vulnerabilities allow attackers to make stealthy changes to the industrial process. As a consequence, the attack can be highly persistent and can have grave consequences with possible physical impact | Information on the vulnerabilities provided to the vendor |
| Non-industrial solutions | |||
| Smart city infrastructure devices | 6 | The vulnerabilities identified allow attackers to:
|
Vulnerabilities fixed by the vendor |
| Hardware wallet for storing cryptocurrency | 4 (in software and hardware) | The vulnerabilities identified allow attackers to gain full control of the wallet and conduct any operations with it. | Vulnerabilities fixed by the vendor |
Assessing the severity of the vulnerabilities identified
To assess the severity of the vulnerabilities identified, Kaspersky ICS CERT used a vulnerability rating system based on the metrics defined in CVSS v3.0 (Common Vulnerability Scoring System). The following vulnerability severity levels were identified:
- least severe: CVSS v3.0 base score of 5.0 or less;
- medium severity: CVSS v3.0 base score of 5.1 to 6.9 (inclusive);
- most severe: CVSS v3.0 base score of 7.0 or more.
The absolute majority of those vulnerabilities identified by Kaspersky ICS CERT for which CVEs were published in 2019 have CVSS v.3 base scores of 7.0 or more, which places them in the most severe group. Ten of these vulnerabilities were assigned the highest possible base score of 10. These include vulnerabilities in software components that are common to many products – cross-platform solutions which work over the VNC protocol.
Why vulnerabilities occur
All existing vulnerabilities arise from errors made in the process of developing software, including solution architecture. A classification of such errors exists, called the Common Weakness Enumeration. Based on Kaspersky ICS CERT research conducted in 2019, the most popular error was CWE-787, “Out-of-bounds Write”, which was identified in the process of analyzing RAT solutions. This type of error is a necessary, but not sufficient condition for exploiting a Remote Code Execution vulnerability.
Number of CVE entries published
In 2019, 43 CVE entries were published based on Kaspersky ICS CERT research.