17 June 2020
Steganography in attacks on industrial enterprises (updated)
Kaspersky ICS CERT experts have identified a series of attacks on organizations located in different countries. As of early May 2020, there are known cases of attacks on systems in Japan, Italy, Germany and the UK. Up to 50% of the attackers’ targets are organizations in various industrial sectors. Attack victims include suppliers of equipment and software for industrial enterprises. Attackers use malicious Microsoft Office documents, PowerShell scripts, as well as various techniques that make it difficult to detect and analyze malware.
Phishing emails, used as the initial attack vector, were customized using text in the language of each specific country. The malware used in this attack continued to run only if the operating system had a localization that matched the language used in the phishing email. For example, in the case of an attack on a company operating in Japan, the text of a phishing email and a Microsoft Office document containing a malicious macro were written in Japanese. Also, to successfully decrypt the malware module, the operating system had to have a Japanese localization as well.
As a result of an attack, banker Trojans from the Bebloh family (Shiotob, URLZone) and the Ursnif family (Gozi, ISFB) are installed on victim computers.
Technical analysis
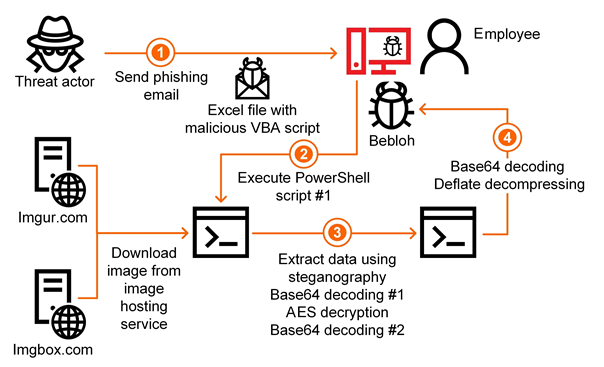
The attackers send a phishing email to the victim. The email contains a request to open the attached document urgently.
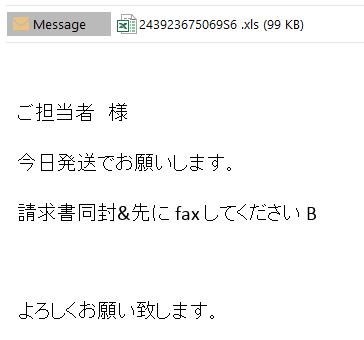
The Excel document attached to the email contains a malicious macro script (verdict: Trojan.MSExcel.Agent.be). After opening the document, the user sees a message with the request to enable the document’s active content. If the user agrees to do that, the malicious macro is executed.
The main task of the macro is to decrypt and execute a PowerShell script. The script is executed with the following parameters:
-ExecutionPolicy ByPass,
-WindowStyle Hidden,
-NoProfile,
i.e., the script is executed in spite of the configured policy, in a hidden window and without loading the user configuration.
The PowerShell script (verdict: HEUR:Trojan.PowerShell.Generic) randomly selects one of the URL addresses listed in it. The URLs lead to public image hosting services, imgur.com and imgbox.com. The script downloads the image to which the URL points and starts the data extraction procedure.

The data is hidden in the image using steganographic techniques and is extracted by the malware from pixels defined by the algorithm. Using steganography enables the attackers to evade some security tools, including network traffic scanners.
The data extracted from the image is consecutively encoded using the Base64 algorithm, encrypted with the AES algorithm and encoded using Base64 again. Curiously, the script has an error in its code, included on purpose, with the exception message used as the decryption key. Notably, the text in the exception message depends on the language pack installed in the operating system. Apparently, the attackers prepare the malicious script specifically for victims from a particular country.
The decrypted and decoded data makes up one more PowerShell script, which is executed.
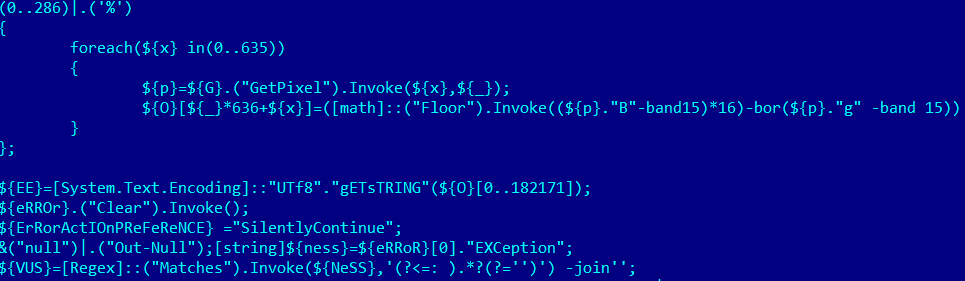
The second PowerShell script also decodes part of its contents using the Base64 algorithm, after which it unpacks the resulting data buffer using the Deflate algorithm. As a result, the malware gets one more PowerShell script – in this case, an obfuscated sample of malware from the Bebloh family (Shiotob, URLZone). In other cases, the attackers have used Trojans from the Ursnif family (Gozi, ISFB).
The Bebloh/Shiotob family has been known since 2009. Trojans from that family steal FTP client and email account passwords and ‘listen’ to browsers’ internet traffic to steal authentication data for various websites. The Ursnif family has broader functionality; its latest versions include updated data stealing modules, including those designed to steal cryptocurrency wallets.
Conclusions
Researchers observed previous variants of this attack starting at least from 2018.
The new wave of attacks has caught the attention of researchers because industrial enterprises and companies that develop and supply products for industrial enterprises make up a high percentage of potential victims and because the attackers use several unconventional technical solutions.
First, the malicious module is encoded in an image using steganographic techniques and the image is hosted on legitimate web resources. This makes it virtually impossible to detect such malware using network traffic monitoring and control tools while it is being downloaded. From the standpoint of technical solutions, this activity is indistinguishable from sending ordinary requests to legitimate image hosting services.
A second curious feature of the malware is the use of the exception message as the decryption key for the malicious payload. This technique can help the malware evade detection in automatic analysis systems of the sandbox class and makes analyzing the functionality of the malware slightly more difficult for researchers if they do not know what language pack was used on the victim’s computer.
In all the cases identified, the malware was blocked by Kaspersky solutions.
If you have encountered an attack of this kind, you can report it to us through a special form on our website.
Recommendations
- Train employees at enterprises in using email securely and, specifically, in identifying phishing messages.
- Restrict macros in Microsoft Office documents.
- Restrict PowerShell script execution (wherever possible).
- Pay special attention to events of launching PowerShell processes initiated by Microsoft Office applications.
- Restrict the ability of programs to gain SeDebugPrivilege privileges (wherever possible).
- Install antivirus software with support for centrally managing the security policy on all systems; keep the antivirus databases and program modules of security solutions up to date.
- Use accounts with domain administrator privileges only when necessary. After using such accounts, restart the system on which the authentication was performed.
- Implement a password policy with password strength and regular password change requirements.
- If it is suspected that some systems are infected, scan these systems with antivirus software and force a change of passwords for all accounts that have been used to log on to compromised systems.