21 May 2021
DarkChronicles: the consequences of the Colonial Pipeline attack
This article began as an overview of the Colonial Pipeline incident. However, the events unfolded so rapidly that the scope of the publication has gone beyond a single incident.
Attack on Colonial Pipeline
During the period from May 7 to 12, fuel transportation over the Colonial Pipeline, the largest pipeline system for refined oil products in the US, was suspended. The cause of this was a cyberattack involving DarkSide ransomware.
Colonial Pipeline is one of the largest pipeline operators in the United States. The company delivers about 45% of fuel for the East Coast, including gasoline, diesel fuel, heating oil, jet fuel and fuel used by the military.
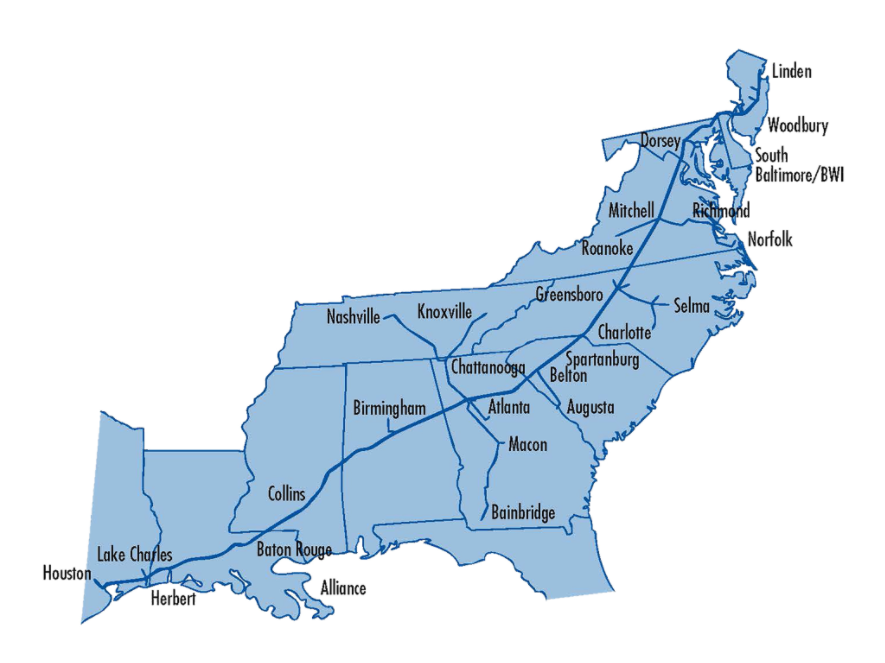
Source: Colonial Pipeline
On May 7, a statement that Colonial Pipeline had suffered a cyberattack appeared on the company’s website. Later, it became known that the company had fallen victim to DarkSide ransomware.
When it was discovered that the malware had infiltrated the company’s IT network, Colonial Pipeline operators were forced to shut down some of the OT systems to prevent it from spreading. This resulted in the pipeline’s operation being completely blocked. According to CISA, there are currently no signs of the attackers having gained access to Colonial Pipeline’s OT systems.
According to Bloomberg, the attackers were able to obtain almost 100 gigabytes of data in just two hours before the attack’s active phase began.
Experts from FireEye Inc. were engaged to conduct an investigation and help mitigate the attack’s consequences. FBI, the Department of Energy and the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency were also involved in investigating the incident.
The incident was reported to President Biden.
Exactly how the malware penetrated the company’s network is not known. Standard ransomware distribution schemes – phishing emails, vulnerability exploitation, the use of previously stolen RDP or VPN accounts of employees – are among the possibilities being considered.
Colonial Pipeline reported that it was working to resume fuel transportation through the pipeline but that it could only be fully restored when experts had made sure that it was safe and when the federal regulator’s approval had been obtained.
Meanwhile, the consequences of Colonial Pipeline suspending fuel supplies were becoming increasingly dramatic. Due to the threat of a shortage, four US states – North Carolina, Virginia, Georgia, and Florida – declared a state of emergency. For the first time since 2014, the average price of a gallon of gasoline across the US increased to almost $3 (the last time the price exceeded $3 per gallon had been in 2014).
There were no reports of the Colonial Pipeline coming back online until May 12. On May 9, the company was able to restore the operation only on some smaller lateral lines between terminals and delivery points .
On the evening of May 12, Colonial Pipeline announced that it had initiated the restart of pipeline operations. On May 13, the company started fuel deliveries in a majority of its markets. However, the company warned it would take some time for the product delivery supply chain to return to normal.
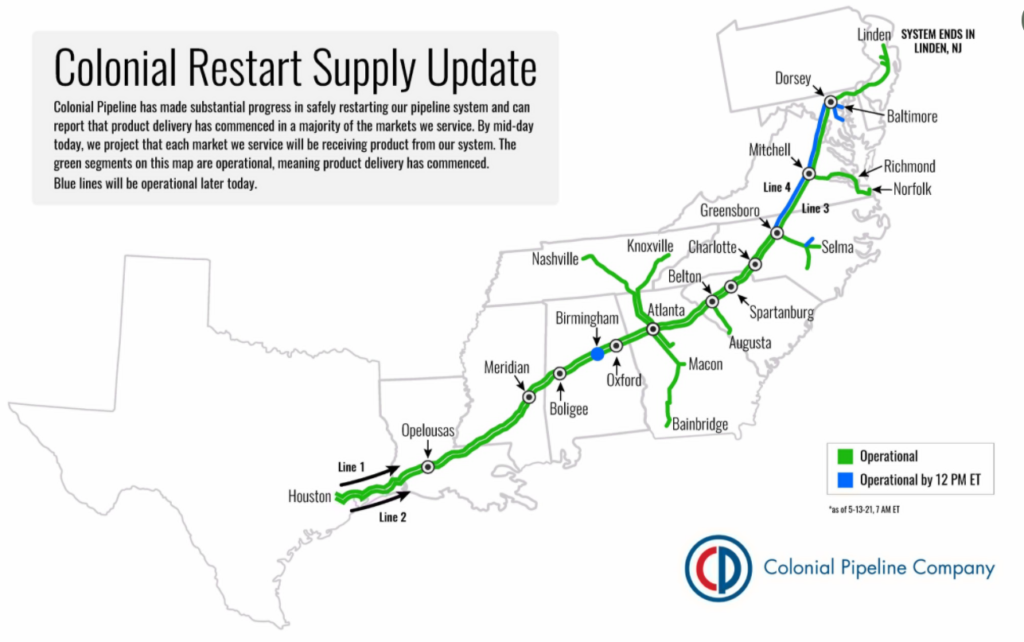
This story has demonstrated the enormous danger posed by today’s cybercriminals. The Colonial Pipeline attack was one of the largest-scale cybersecurity incidents affecting critical infrastructure to date. It was also one of the most dramatic examples of how significantly an attack on an industrial organization’s IT systems could disrupt its operations.
The villains
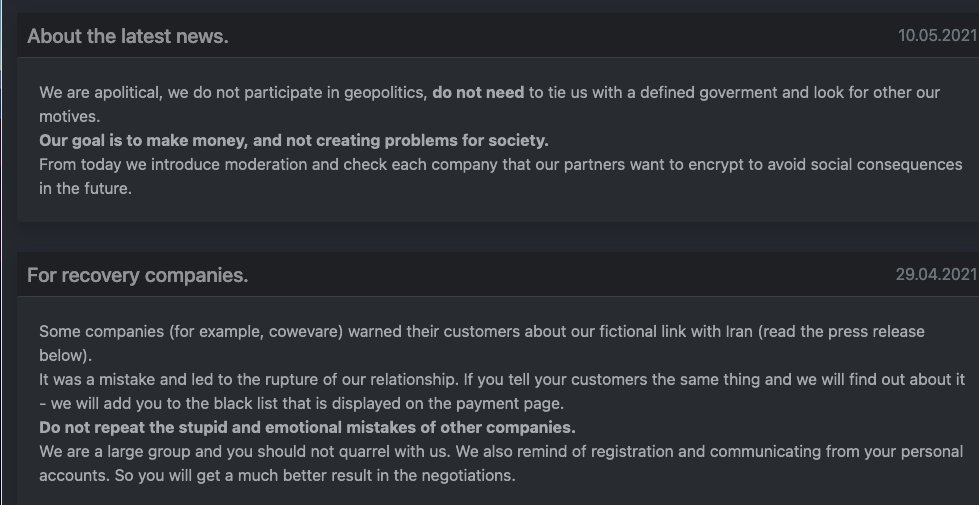
The impact of the attack was so severe that DarkSide developers published a statement on their website on May 10 to the effect that ‘third-party’ operators, rather than them, were responsible for the attack.
The DarkSide threat actor used the Ransomware-as-a-Service (RaaS) scheme, under which the developers of the ransomware maintained and developed the malware, the infrastructure for their affiliates, wallets for ransom payments, etc., provided tools for conducting negotiations with victim companies (and did the negotiations themselves, if necessary), while ‘external’ operators used the malware in attacks on systems they had compromised. In the event of success, the money made was shared in proportions agreed upon in advance.
So far, the operator behind the DarkSide attack on Colonial Pipeline has not been named. It is likely to be a Russian-speaking group – at the least, the developer requires that its affiliates “speak Russian” and not use DarkSide to attack organizations in CIS (the Commonwealth of Independent States, which unites several republics of the former Soviet Union). The malware itself has an option of terminating without encrypting data on computers with the Russian locale enabled.
DarkSide developers were explicit about their interests: “Our goal is to make money, and not creating problems for society” (see the screenshot above). They also claim that they don’t attack social facilities (schools, universities, hospitals, etc.), leave non-profit and government organizations alone and even do charity work.
DarkSide promised they would check in the future what companies their affiliates plan to attack in order “to avoid social consequences in the future.”
The DarkSide ransomware uses a hybrid encryption scheme, which is based on the Salsa20 stream cypher combined with the RSA-1024 public-key algorithm. This indicates, at the least, a sufficiently high level of ‘creativity’ on the part of the developers. They also use the aPLib library to compress the executable files of their malware.
There are two versions of the DarkSide malware – for the Windows family of operating systems and for Linux. In January 2021, Bitdefender made a decryption tool available for the first version of the malware for Windows. However, the threat actor learnt from its mistakes and no decryptor has been developed so far for version 2 of the DarkSide encryption malware.
FireEye described the technical characteristics of the malware in their latest report. Sophos published a report describing tools used in several attacks involving the DarkSide ransomware.
In April 2021, Kaspersky released a private report on earlier attacks involving the DarkSide malicious toolset. Another private report was released on May 12 (both reports are available by subscription).
The ransom
On May 12, CNN reported on its website, citing sources familiar with the matter, that the attackers had demanded a ransom of nearly $5 million from the victim company. However, according to one more trusted source of CNN, Colonial Pipeline, with help from the authorities, managed to retrieve stolen data that the attackers had not yet moved from intermediary servers within the United States. If that this information was accurate and Colonial Pipeline could recover encrypted data without the attackers’ participation, the question of whether to pay the ransom could be taken off the agenda for the victim company.
However, on May 13, Bloomberg, also citing two people familiar with the transaction, published information that Colonial Pipeline had payed the hackers about $5 million in cryptocurrency as early as Friday, May 7, several hours after the attack. One more well-informed source told Bloomberg that US government officials were aware that Colonial had paid the ransom.
So why did it take Colonial Pipeline so long to restore the pipeline’s operation? That was because the decrypting tool received from the attackers was so slow (!) that the company had to continue using its own backups to restore its systems.
Both a representative of Colonial Pipeline and a representative of the US National Security Council declined to comment on the situation.
On May 14, Elliptic reported that its experts had identified (based on their intelligence collection and analysis of blockchain transactions) the Bitcoin wallet used by DarkSide to receive ransom payments from its victims. That wallet received a 75 BTC payment from Colonial Pipeline on May 8. On May 9, a large part of that amount was moved out of the wallet.
On May 19, a Colonial Pipeline representative confirmed that the company had paid ransom to the attackers.
Who won
Once again it has turned out that information security issues are relevant to villains, too. The successful (though, it turns out, not that brilliant) operation which involved stealing data, doing encryption and receiving ransom from Colonial Pipeline was not the end of the story.
On May 14, DarkSide developers announced that they had lost access to part of their infrastructure, including their blog, payment server, and the CDN. All the money, including their own money and “client” funds (apparently, the money of their affiliates) had been moved to an unknown address. They promised to pay compensation to their affiliates by May 23, 2021 from a previously made deposit payment and to provide all their affiliates with decryption utilities through their “technical support” channel. They also announced that the service and the affiliate program were discontinued.
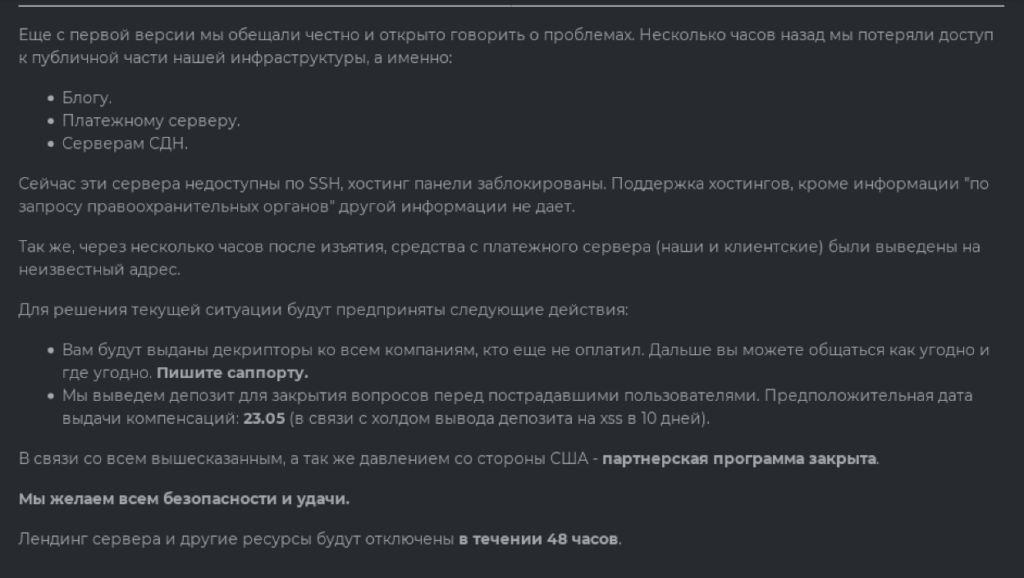
This is likely the end of the DarkSide story. If the affiliate program resumes its operation, it will probably be under a different name.
Victims
DarkSide first appeared on the radar in August 2020. According to DarkTracer, data of 99 victim companies has been leaked to the darkweb.
Specifically, DarkSide was implicated in attacks on large energy companies. For example, in February 2021 the group targeted Eletronuclear (a nuclear energy division of the Brazilian giant Eletrobras) and Copel (the largest electric power company in the state of Paraná, Brazil).
As the Colonial Pipeline story was unfolding, two more DarkSide attacks were uncovered.
Attack on Brenntag
On May 13, information appeared on the BleepingComputer website that in early May Brenntag had fallen victim to a DarkSide ransomware attack. The company paid a sum in Bitcoins amounting to $4.4 million to get a decryption utility and prevent data stolen by the attackers from being publicly leaked.
Brenntag is a world-leading chemical distribution company. It is headquartered in Germany and has over 670 sites worldwide. The attack affected the company’s North American division.
As soon as Brenntag employees realized that the company’s computers were infected with ransomware, affected systems were disconnected from the network. Third-party experts were immediately engaged. The company also informed law enforcement of the incident.
According to information provided to BleepingComputer by an anonymous source, the attackers claimed to have stolen 150 GB of the company’s data in addition to encrypting information on its computers. As proof of the theft, a private post was published on the darknet with a list of the types of data stolen and screenshots of some of the stolen files. Bleeping Computer published a screenshot received by Brenntag employees with the threat to make the information public if the company failed to start negotiations with the attackers.
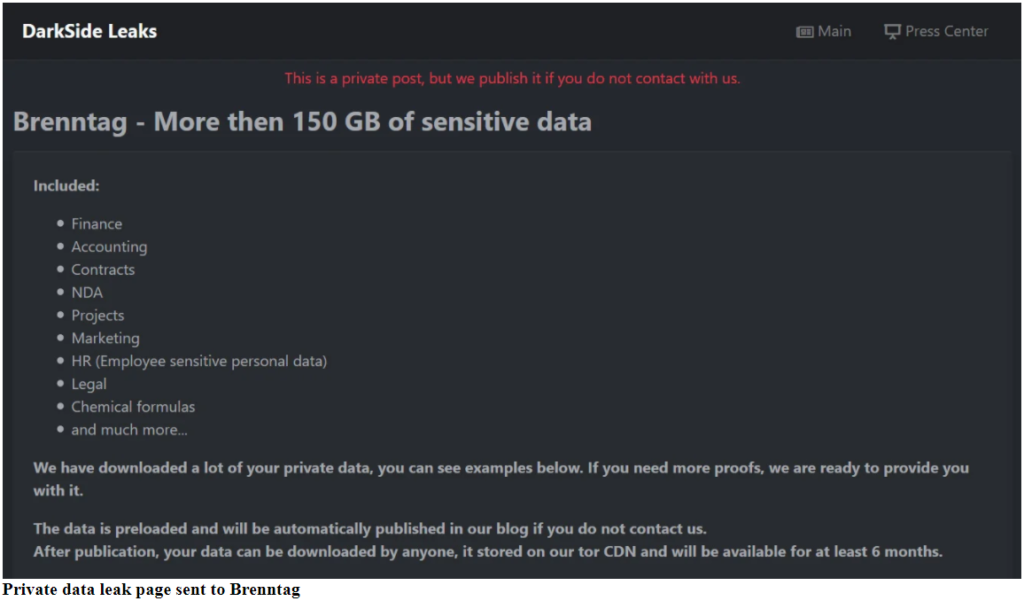
Brenntag did in fact negotiate. The attackers demanded a ransom of 133.65 Bitcoins (about $7.5 million), but the amount was negotiated down to $4.4 million. It was paid on May 11.
Attack on Toshiba
On May 14, the Toshiba Tec Group disclosed that the group’s European companies had fallen victim to a DarkSide attack.
After discovering an infection, the company stopped the networks and systems connecting the group’s Japanese and European subsidiaries, as well as systems linking its European companies. Measures were taken to backup data and recover affected systems. Toshiba Tec Group immediately reported the incident to the relevant European authorities.
The group engaged experts from an external organization to investigate the incident.
According to Toshiba Tec Group, a minimal amount of data was stolen as a result of the ransomware attack. Reuters, citing screenshots from the DarkSide website provided by a cybersecurity firm engaged by the victim (these screenshots were not included in the publication, however), wrote that over 740 gigabytes of data had been stolen, including passports and other personal information.
CNBC clarified that the DarkSide ransoware had attacked Toshiba on the evening of May 4. A representative of Toshiba Tec Group told CNBC that the company had not negotiated with the attackers or paid a ransom.
The money
On May 18, Elliptic, the company that identified the Bitcoin wallet used by DarkSide to receive the ransom payment from Colonial Pipeline, published interesting data based on its blockchain transaction analysis. Elliptic experts did not limit their research to an analysis of one wallet – they analyzed all wallets used by DarkSide in the past nine months (i.e., since September 2020) to receive Bitcoin ransom payments from victims. It is worth reminding that the DarkSide threat actor first appeared on security researchers’ radar in August 2020.
The results of the analysis performed by Elliptic are impressive:
- 47 companies that fell victim to DarkSide paid the threat actor a total amount of ransom in excess of $90 million.
- Elliptic has estimated that the average ransom amount was $1.9 million.
- Any ransom received by the threat actor was divided between the developer and the affiliate that participated in attacking the victim. Money was transferred in previously agreed proportions to the relevant affiliates’ Bitcoin wallets.
- In total, the DarkSide developers received $15.5 million worth of Bitcoins (17%) and the remaining $74.7 million (83%) were passed on to affiliates.
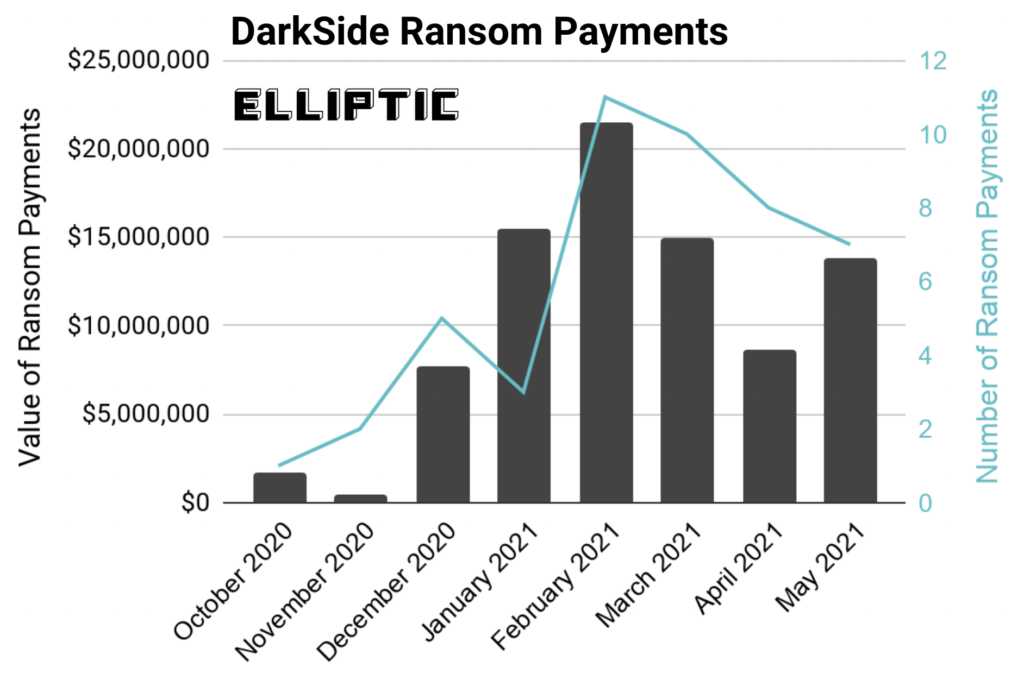
Source: Elliptic
In the course of their investigation, Elliptic discovered that money for operators that conducted the attacks on Colonial Pipeline and Brenntag were sent to the same Bitcoin address. Based on this, Elliptic believes that the same threat actor was responsible for infecting both companies.
What now?
The attack on a company that is part of the US critical infrastructure and the shutdown of the DarkSide service forced following the attack could affect the situation in the ransomware market as a whole: the story was too high-profile and the attack’s consequences were too severe – both for the victim company and for the attackers.
The villains
It is to be hoped that threat actors will learn the lesson: security is no longer guaranteed, even if you live in one country and select your victims in another.
It can be assumed that, at the least, attackers will select attack targets more carefully, avoiding critical infrastructure and infections with severe consequences.
Some groups could change their tactics and shift their activity from encryption to sensitive data theft and subsequent blackmailing of victim companies. Sometimes threat actors gain access to information that victim companies do not want law enforcement to see – which means they will not report the theft and will try to settle everything as quietly as possible.
There is also the possibility that the most cautious will change their specialization and focus on other activities. They are unlikely to abandon cybercrime altogether, but cyber-villains have many opportunities to make money these days.
Hackers
We count on the hacker community and hacker resources to start treating ransomware developers and their affiliates appropriately – that is, as the cybercriminals that they are.
A good example is the Russian-language user forum called XSS (formerly DaMaGeLab). In the past, ransomware developer groups (REvil, LockBit, DarkSide, Netwalker, Nefilim, etc.) often used that forum to advertise and attract new customers. On May 14, the forum’s administration banned advertising and selling any ransomware on their website. As rightly mentioned on the website, “the word <ransomware> has become dangerous and toxic.”
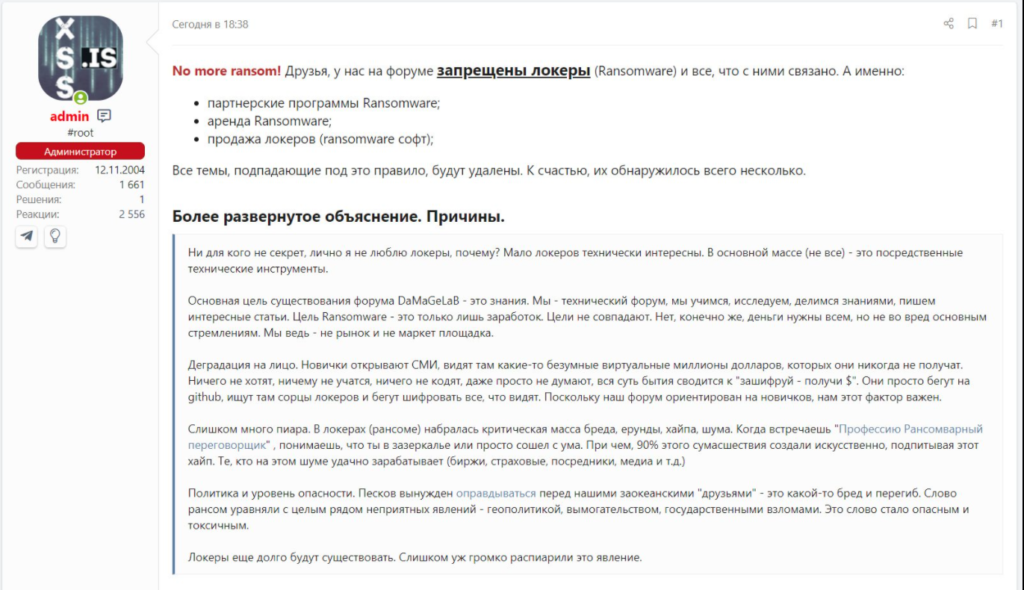
A similar decision was made on Exploit and RAID user forums.
Companies
Unfortunately, statistics show that not only office networks can be accessed by ransomware. According to Kaspersky ICS CERT data, the percentage of ICS computers on which ransomware was blocked increased in the second half of 2020 in Australia, North America and Western Europe.
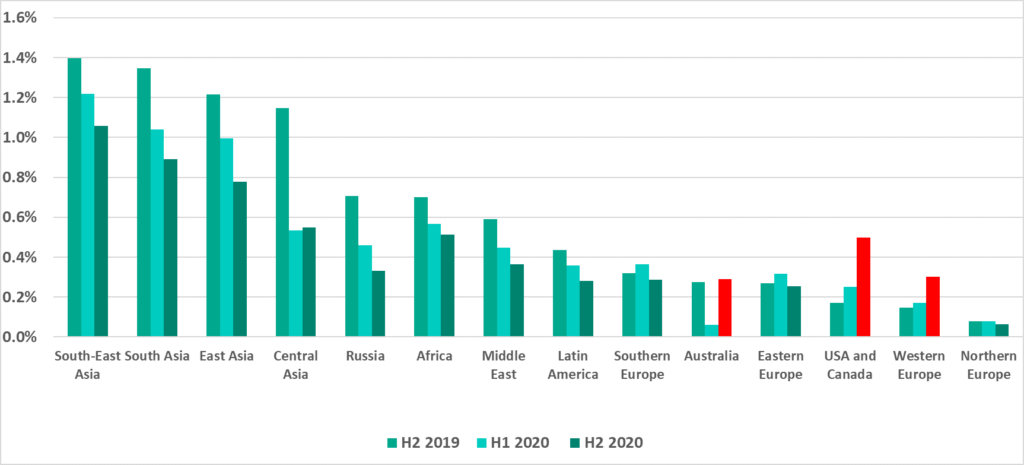
In the first quarter of 2021, that percentage decreased in Europe and North America:
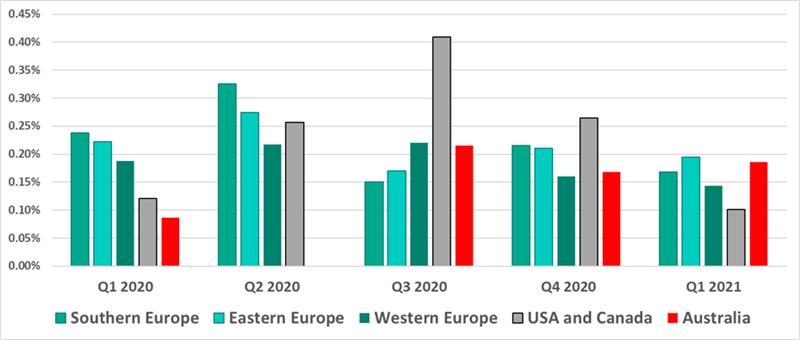
In spite of the clear downward trend in the percentage of attacked ICS computers, that percentage is unlikely to reach zero in the coming years.
We can say with certainty that the attacks will not stop. We urge companies, including industrial organizations, to recognize the dangers of ransomware (and not only ransomware) infection and to do everything necessary for their protection.
Appendix I – Indicators of Compromise
Linux Ransomware Samples
b0fd45162c2219e14bdccab76f33946e 85547c6e720886c33bdacae81c180c46 8b0bc89bc1fb3f5fe01d5c8cdffdaa98 4bbfcdb7e491ae66b20f5b797945094a
Linux Ransomware Decryptor sample
267a7f456e276dd4979f1b1420d2e331
Windows Ransomware Samples
0390938e8a9df14af45e264a128a5bf8 04fde4340cc79cd9e61340d4c1e8ddfb 0e178c4808213ce50c2540468ce409d3 0ed51a595631e9b4d60896ab5573332f 130220f4457b9795094a21482d5f104b 1a700f845849e573ab3148daef1a3b0b 1c33dc87c6fdb80725d732a5323341f9 222792d2e75782516d653d5cccfcf33b 29bcd459f5ddeeefad26fc098304e786 3fd9b0117a0e79191859630148dcdc6d 47a4420ad26f60bb6bba5645326fa963 4d419dc50e3e4824c096f298e0fa885a 5ff75d33080bb97a8e6b54875c221777 66ddb290df3d510a6001365c3a694de2 68ada5f6aa8e3c3969061e905ceb204c 69ec3d1368adbe75f3766fc88bc64afc 6a7fdab1c7f6c5a5482749be5c4bf1a4 84c1567969b86089cc33dccf41562bcd 885fc8fb590b899c1db7b42fe83dddc3 91e2807955c5004f13006ff795cb803c 979692cd7fc638beea6e9d68c752f360 9d418ecc0f3bf45029263b0944236884 9e779da82d86bcd4cc43ab29f929f73f a3d964aaf642d626474f02ba3ae4f49b b0fd45162c2219e14bdccab76f33946e b278d7ec3681df16a541cf9e34d3b70a b68be0dacf09904cd4a0fbe0aab3842e b9d04060842f71d1a8f3444316dc1843 c2764be55336f83a59aa0f63a0b36732 c363e327287081251b820276cd9ce1f8 c4f1a1b73e4af0fbb63af8ee89a5a7fe c81dae5c67fb72a2c2f24b178aea50b7 c830512579b0e08f40bc1791fc10c582 cfcfb68901ffe513e9f0d76b17d02f96 d6634959e4f9b42dfc02b270324fa6d9 e44450150e8683a0addd5c686cd4d202 f587adbd83ff3f4d2985453cd45c7ab1 f75ba194742c978239da2892061ba1b4 f87a2e1c3d148a67eaeb696b1ab69133 f913d43ba0a9f921b1376b26cd30fa34 f9fc1a1a95d5723c140c2a8effc93722
Enigma Packed Windows Ransomware Sample
ec0e75c477fc54c92c47788bb9ccc034
Infrastructure
Domain – IP – First seen – ASN
baroquetees[.]com - 176.103.62.217 - 2021-03-18 - 59729 catsdegree[.]com - 99.83.154.118 - 2021-02-05 - 16509 rumahsia[.]com - 99.83.154.118 - 2020-12-18 - 16509 securebestapp20[.]com - 185.105.109.19 - 2020-09-21 - 210079 temisleyes[.]com - 198.54.117.197 - 2021-02-09 - 22612
More indicators are available for subscribers of Kaspersky Threat Intelligence service.
