29 April 2019
Kaspersky Industrial CTF 2019 Finals Results
The finals of Kaspersky Industrial CTF 2019, an international industrial cybersecurity contest, were held in Singapore on April 9-10 at the Kaspersky Security Analyst Summit (SAS) conference. It was the fourth CTF tournament organized by Kaspersky Lab.
Participants of the qualifications round included 443 teams from different countries. The four teams that made it to the finals were VoidHack (Russia), LC/BC (Russia), PwnThyBytes (Romania), and TokyoWesterns (Japan). TokyoWesterns was also a finalist of last year’s Kaspersky Industrial CTF contest.
Contest format
This year, the tournament followed the classic Attack/Defense CTF rules. The teams were provided with identical servers, each having five vulnerable services created by the Kaspersky Lab team. Each service had 1 to 5 vulnerabilities – binary, web, or logical. The goal for each team was to find the vulnerabilities, fix them on their server and take advantage of these same vulnerabilities on the other servers to attack their opponents.
Whether the services were available over the network and whether they operated correctly was monitored in real time by the verification system. Points were awarded based on the duration of each service’s uptime, as well as the participants’ ability to fix vulnerabilities in their own services and to exploit them in their opponents’ services.
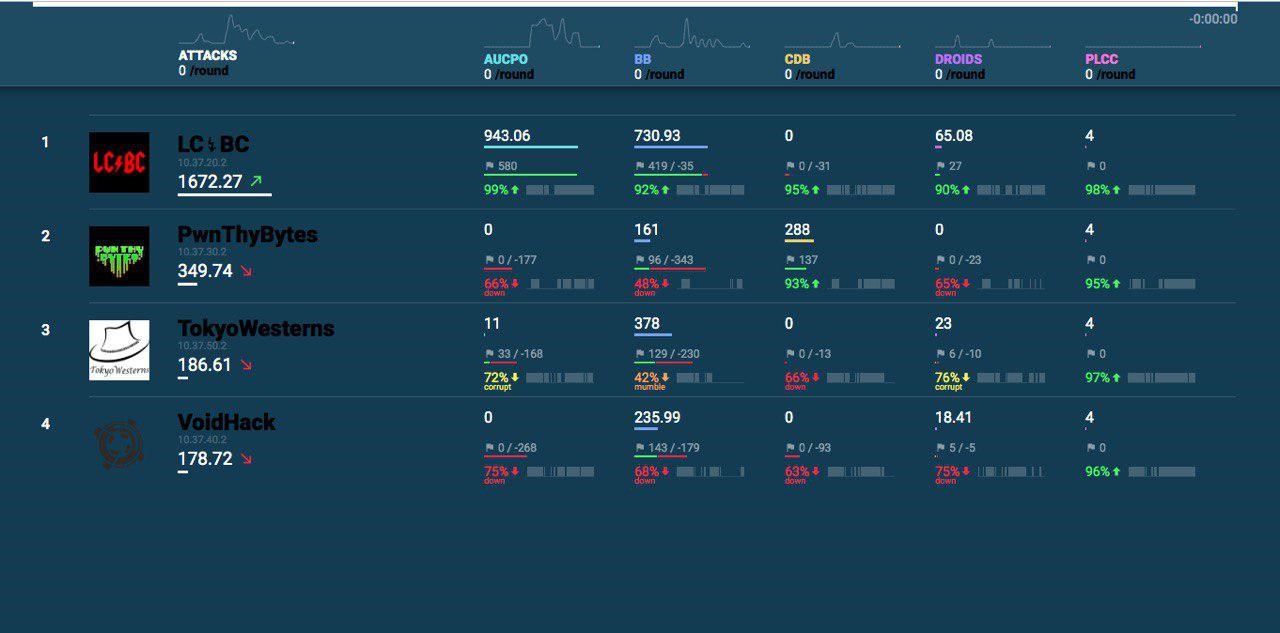
Contest results
Highlights from the battlefield
The high point of the CTF was the VoidHack team members discovering a vulnerability in one of the services that had not been included intentionally by the contest organizers. The vulnerability caused a denial of service and was successfully exploited in attacks against opponents.
The participants found the CDB – a key-value data store – the most difficult to come to grips with. According to the PwnThyBytes captain, it offered a great combination of simple and very complicated vulnerabilities.
The AUCPO service, an OPC server based on the OPC UA specification (open62541 implementation) was of particular interest to the participants from the industrial cybersecurity perspective.
The LC/BC team, which took a confident lead from the start and led throughout the game, became the winner. The Romanian team, PwnThyBytes, earned second place. In the last hours of the contest, VoidHack and TokyoWesterns engaged in a fierce fight for third place. In the end, the Japanese team succeeded in becoming one of the three leaders.
Contest participants received various valuable prizes and presents as awards.
Personal impressions
All of the participants left positive feedback on the contest. The teams praised both the tasks and the overall organization level of the event.
“The Kaspersky Industrial CTF team that prepared tasks for the finals included experts from different Kaspersky Lab departments. This helped make the services really varied and interesting, which the participants all appreciated. For the first time, the Kaspersky Industrial CTF finals were in the Attack and Defense format, and it went down well both with the participants and the organizers,” said Vladimir Dashchenko, head of vulnerability research at Kaspersky Lab ICS CERT. “We are going to continue developing these contests – specifically, to add attack visualization, which will help make the tournament more thrilling both for the teams and for the audience.”
The Kaspersky Industrial CTF organizers team would like to thank Cisco for providing equipment for the CTF finals.
See also
-
Detective investigation of APT and rare virus specimens: Kaspersky ICS CERT experts to present new research at KICC
17 September 2025
-
Industrial cybersecurity in 2024: trends and forecasts presented by Evgeny Goncharov, head of Kaspersky’s ICS CERT
26 March 2024
-
TÜV Austria Academy will offer Kaspersky training courses
22 December 2021