22 October 2018
Phishing attack targeting Italian naval and defense industry
Researchers from Yoroi Cyber Security Defence Center (Yoroi CERT) have identified several attacks targeting enterprises in the Italian naval and defense industry. Employees of these enterprises received phishing emails with a malicious Excel file attached to them.
The suspicious emails were intercepted between October 9 and October 15. Their contents indicate that this was a carefully prepared phishing attack. To ensure that the malicious file would be opened by the victims, the attackers sent their emails on behalf of existing large customers, purportedly to make orders or request quotations for marine ship parts.
The malicious Excel file was designed to download a remote-access Trojan, which the researchers dubbed MartyMcFly, to the victim’s system. The attackers can use the Trojan to gain control of a remote system or steal data from it. The attackers also use a modified version of the QuasarRAT remote-access tool, whose source code is available on GitHub.
The researchers have so far not been able to provide attribution for the cyberattack, but they do believe that an APT group is behind it. They emphasize that many known APT groups use publicly available utilities to make attribution difficult.
We believe it is worth noting that well considered and carefully prepared phishing emails and remote administration tools can also be used by ‘advanced’ phishers. We believe that a cybercriminal group is behind this attack. The group conducts massive campaigns that involve sending phishing emails to various companies, some of which are critical infrastructure facilities. The objective of such groups is to steal financial data and money.
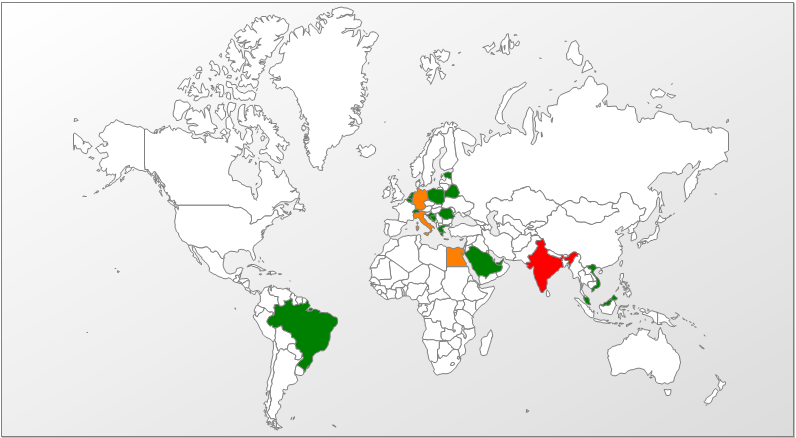
According to our data, the phishing documents mentioned in the Yoroi publication have been emailed, under different names, to companies located in many different countries, including Germany, Spain, Bulgaria, Kazakhstan, India, Romania, etc. The companies attacked work in a variety of areas, from supplying beans to providing consulting services.
Geographical distribution of detections of the xlsx document from phishing emails
(based on Kaspersky Security Network data)
Lately, we have seen numerous well-designed phishing emails sent on behalf of existing companies that have profiles similar to those of target companies. Because of this, it can now be impossible to tell whether a phishing email represents a spear phishing attack that targets just a few recipients in the same industry or a mass phishing campaign which affects companies with different profiles located in different countries.
Sources: Yoroi, Kaspersky Lab