19 June 2017
Vulnerable System Update Statistics. General Electric
- Update Installation Problems
- Vulnerable System Updating Statistics for General Electric
- OVAL Definitions
- Neutralizing Threats
- Comment by General Electric
The Kaspersky Lab Industrial Control Systems Cyber Emergency Response Team (Kaspersky Lab ICS CERT) continues its series of articles devoted to analyzing vulnerabilities in industrial automation systems across the globe. In conducting such research, Kaspersky Lab reports any information regarding vulnerabilities to affected vendors in accordance with coordinated vulnerability disclosure best practices. We would like to thank General Electric for its cooperation and coordination with regards to this research.
Update Installation Problems
Not every organization is able to immediately install all critical updates on its various industrial system components. As a rule, updating industrial automation system software is a complicated procedure that is potentially risky for the stability of the systems involved and for the entire industrial process of the enterprise. The problem of quickly installing and configuring critical updates may be due to a number of factors:
- Industrial process continuity. Many software updates require the system to be restarted, which is extremely problematic for industrial control systems. If it is necessary to install a critical update that requires system restart, the question arises of when this should be done. As a rule, this is only possible during scheduled system downtime, since unscheduled downtime can result in very significant financial losses (direct loss of profit, damage to individual system components or the entire system, etc.). For example, one minute of unscheduled downtime in an auto glass production line can cost the enterprise’s owners about US$50,000.
- The critically important requirement to perform full-scale testing of all changes to the structure and configuration of industrial software. There are risks related to software or hardware incompatibility of new elements or system settings. Prior to being commissioned, a system is tested not only by the industrial control system vendor but also by the owner, upon completion or as part of commissioning and start-up operations. After being commissioned, the system is covered by a warranty that can be annulled by the solution’s vendor or supplier if changes to software or hardware are made by the system’s owner or operator without the correct prior testing. Regulatory requirements for the relevant industry can also play an important role. For some types of production, e.g., the manufacture of pharmaceuticals, the requirements for verifying that system functionality matches the properties stated during the certification process can result in any changes to the ICS structure or configuration taking several years to implement.
This state of affairs inevitably results in a large number of unclosed vulnerabilities, including critical, not only in software components of industrial automation systems, but also in those parts that are traditionally regarded as the classical IT components of ICS, including operating systems, document processing software and other programs used in the industrial infrastructure.
In part, the large number of unclosed vulnerabilities may be the result of an enterprise lacking effective IT security policies to cover software updates for industrial automation system components.
Vulnerable System Updating Statistics for General Electric
All statistics were received via Kaspersky Security Network (KSN), a distributed antivirus network, from those KSN users who had explicitly consented to statistical data being sent anonymously from their computers.
In our previous article, we focused on product security updates delivered by Rockwell Automation, a popular industrial hardware vendor. This article discusses updates to General Electric products. We look at vulnerabilities that were known at the time of writing – a list was prepared using the MITRE CVE database. Updates that close these vulnerabilities were released by General Electric in 2012-2016. Not all publicly known CVEs are represented in this study, only those for which we were able to get a representative sample.
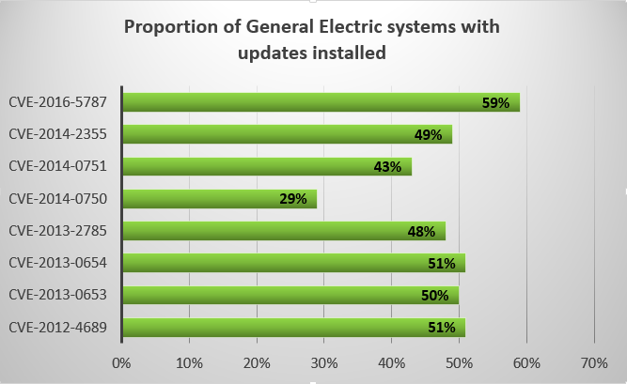
For each of the vulnerabilities, we calculated the proportion of vulnerable to non-vulnerable systems on industrial computers of Kaspersky Lab users. The results are displayed below. It is important to emphasize once more that the data reflects the situation on the machines of Kaspersky Lab customers who voluntarily participate in the KSN program only, and may not represent the distribution of vulnerable and non-vulnerable systems on all industrial computers of General Electric customers.
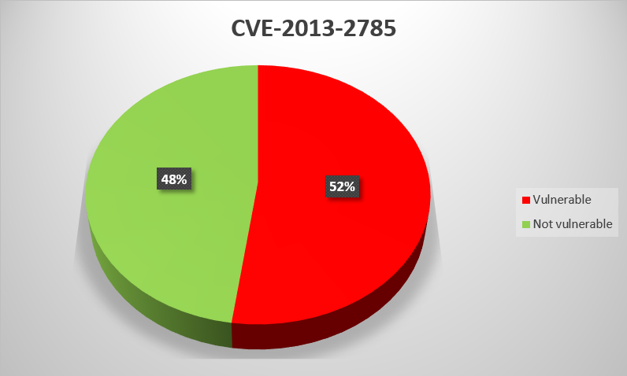
CVE-2012-4689
Remote attackers can use a specially crafted HTTP request to cause denial of service in CimWebServer.exe, which is part of GE Digital Proficy HMI/SCADA – CIMPLICITY versions 4.01 through 8.0 and Proficy Process Systems with CIMPLICITY.
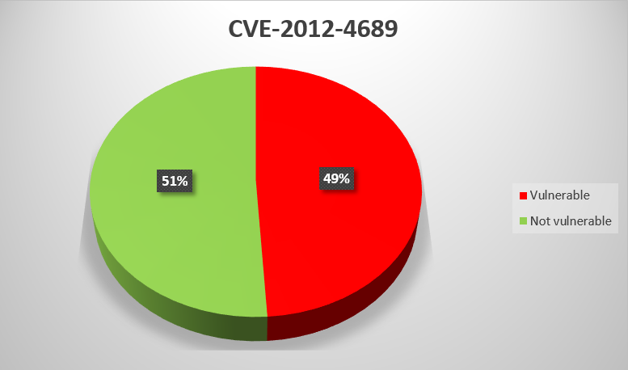
CVE-2013-0653
Directory traversal vulnerability in substitute.bcl, which is part of the WebView CimWeb subsystem in GE Digital Proficy HMI/SCADA – CIMPLICITY versions 4.01 through 8.0 and Proficy Process Systems CIMPLICITY, allows remote attackers to read arbitrary files via a specially crafted packet.
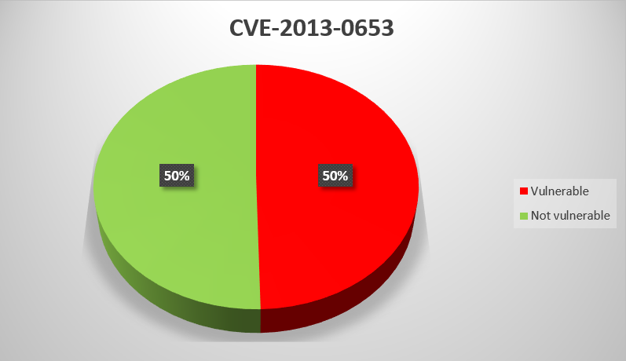
CVE-2013-0654
Remote attackers can use a specially crafted packet to cause denial of service and execute arbitrary code on the target system due to a vulnerability in CimWebServer, which is part of GE Digital Proficy HMI/SCADA – CIMPLICITY versions 4.01 through 8.0 and Proficy Process Systems CIMPLICITY.
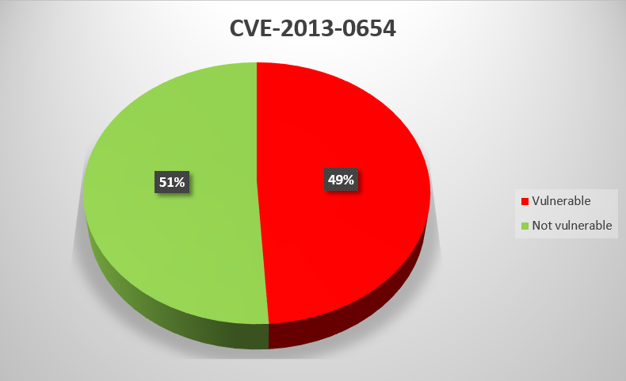
CVE-2013-2785
Multiple buffer overflows in CimWebServer.exe in the WebView component, which is part of GE Digital Proficy HMI/SCADA – CIMPLICITY versions before 8.0 SIM 27, 8.1 before SIM 25 and 8.2 before SIM 19, and Proficy Process Systems CIMPLICITY, allow remote attackers to execute arbitrary code on the target system using specially crafted packets to port 10212/tcp.
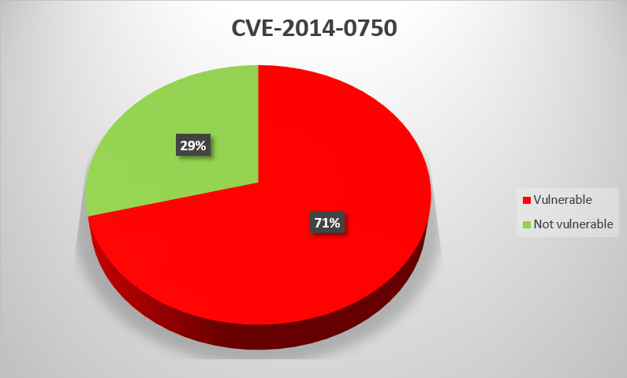
CVE-2014-0750
Directory traversal in gefebt.exe, which is part of the WebView CimWeb subsystem of GE Digital Proficy HMI/SCADA – CIMPLICITY up to 8.2 SIM 24 and Proficy Process Systems CIMPLICITY, allows remote attackers to execute arbitrary code on the target system via a specially crafted HTTP request.
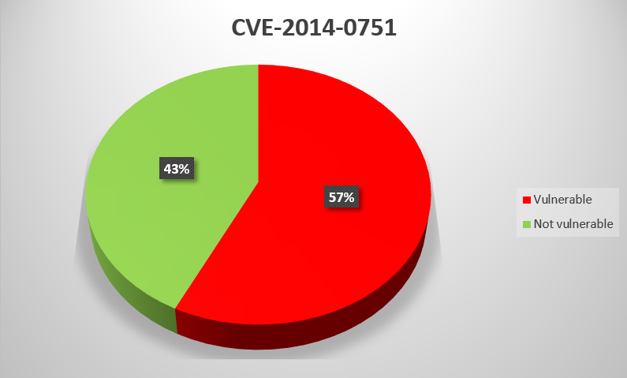
CVE-2014-0751
Directory traversal in CimWebServer.exe in GE Digital Proficy HMI/SCADA – CIMPLICITY before 8.2 SIM 24 and Proficy Process Systems CIMPLICITY allows remote attackers to execute arbitrary code on the target system via a specially crafted request to port 10212/tcp.
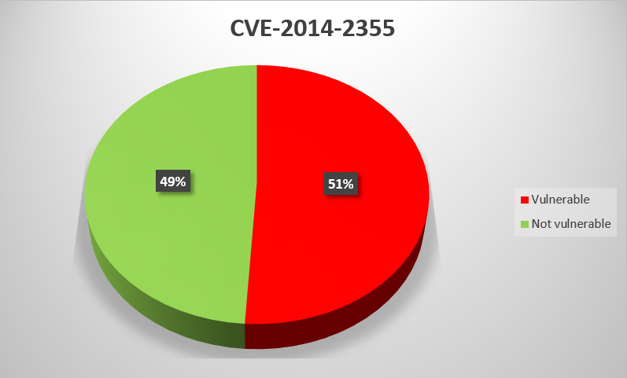
CVE-2014-2355
CimView and CimEdit software components, which are part of GE Proficy HMI/SCADA – CIMPLICITY versions 8.2 and earlier, allow remote attackers to gain certain privileges via a specially crafted .CIM file.
CVE-2016-5787
Digital Proficy HMI/SCADA – CIMPLICITY software, versions before 8.2 SIM 27, mishandles service DACLs, which allows local attackers to modify service configuration via an unspecified attack vector.
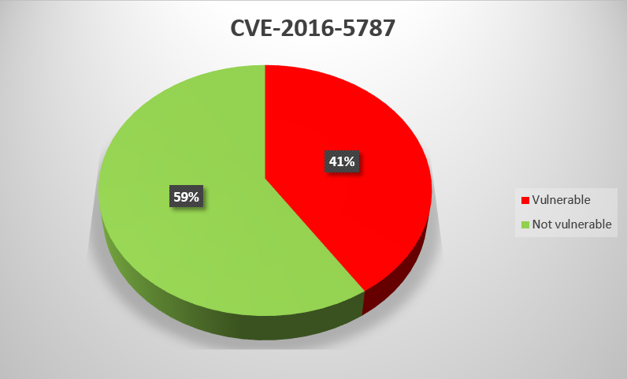
For virtually all General Electric product vulnerabilities that we analyzed, the proportion of systems with updates installed is between 40% and 60%. There is one exception – CVE-2014-0750, for which the figure is as low as 29%. The low proportion may be due to the fact that General Electric has not released a patch for this vulnerability, only instructions on how to fix it “manually”.
We recommend that administrators scan their systems for these vulnerabilities.
OVAL Definitions
To automate the process of analyzing the system for vulnerabilities described in this article, we created OVAL definitions – special XML files with rules for automatic scanning.
Open Vulnerability and Assessment Language (OVAL) is a language that formalizes the representation of rules for scanning the system for vulnerabilities/installed software/applied patches and reporting the results of this assessment. OVAL is an open international standard that is part of SCAP (Security Content Automation Protocol). In the past, it was maintained by the MITRE Corporation now it is done by CIS (Center for Internet Security).
To use OVAL definitions, an interpreter needs to be downloaded and installed on the system to be tested – e.g., the free OVAL interpreter from MITRE. An interpreter uses OVAL definitions to collect information about the system and generate an HTML file containing a report on the presence/absence of vulnerable software.
Alternatively, one of the commercial OVAL interpreters available in the market can be used. A list of available interpreters can be found on the MITRE website.
Despite all the difficulties in installing critical updates, owners of industrial automation systems need an objective view of their systems’ security status. In the table below, you will find links to OVAL definitions that we have prepared. You can use these to check your system for the vulnerabilities listed in this document. If a vulnerability is present, you can use links to General Electric’s problem elimination recommendations (requires registration on the GE website).
Neutralizing Threats
In cases where ICS owners are unable to install updates and critical patches without delay, we recommend minimizing the chances of critical vulnerability exploitation in systems with industrial automation. This requires carrying out a set of measures:
- On vulnerable systems, make an inventory of running network services; where possible stop vulnerable network services, provided that this will not be detrimental to the continuity of the industrial process, and other services that are not directly required for the automation system’s operation; place a special emphasis on services that provide remote access to file system objects, such as SMB/CIFS and/or NFS.
- Perform an audit of ICS component access control; try to achieve maximum access granularity – whenever possible, overlapping of authentication credentials for different ICS components should be avoided; ensure that the password strength meets security requirements and that the most secure available authentication systems are used (e.g., NTLM v2 and Kerberos). Check that ISC authentication credentials are stored securely, are not left in plain sight by employees and are not shared by them. Ensure that passwords are regularly changed, that the accounts of employees who have left the organization are destroyed in a timely manner and that accounts of employees who are absent for extended periods of time are blocked.
- Carry out an audit of network activity inside the enterprise’s industrial network and on its boundaries. Eliminate any network connections found with other adjoining information networks that are not required by the industrial process.
- Check that remote access to the industrial network is provided securely; place special emphasis on ensuring that demilitarized zones are set up in accordance with IT security requirements – network segments marked in diagrams as DMZ often cannot be considered as such in reality (because they do not conform to the basic principles of ‘demilitarized zone’ design). Try to minimize or completely avoid using remote administration tools (such as RDP or TeamViewer). Completely refrain from using ‘portable’ builds of these programs. Completely refrain from using little-known administration tools.
- Make an inventory of installed software. Stop and, where possible, uninstall any software that is not an absolutely essential part of the ICS, without which the system or the system’s users cannot work. Remove any ‘cracked’ software. We recommend sending cracked versions of software to highly qualified experts for analysis to check them for infection and/or backdoors. We recommend contacting Kaspersky Lab ICS CERT for this purpose.
- Keep signature databases, heuristics, and decision algorithms of security software on endpoints up-to-date. Check that all the main protection components are enabled and running and that ICS software directories are not excluded from the protection scope. In industrial environments, application startup control technologies configured in ‘whitelisting’ mode and application behavior analysis technologies have proved to be highly effective.
- Carry out audits of policies and practices related to using removable media and portable devices. Block mobile phones, tablets and untrusted removable media from connecting to the industrial network’s hosts. Wherever possible, disable the relevant ports or control access to these ports using properly configured dedicated tools.
- Implement network traffic monitoring and cyberattack detection tools on industrial networks. In most cases, these measures do not require changes being made to the structure or configuration of ICS hardware and can be carried out without ICS downtime.
- Provide staff with training in the relevance of security threats for industrial automation systems. Establish a process for regular briefings and periodical training of employees. Place particular emphasis on the most popular infection and attack methods, including social engineering techniques. Kaspersky Lab ICS CERT is developing free training courses and will make them available in the nearest future.
- Monitor security policy compliance not only by employees of the enterprise but also by suppliers, vendors of ICS systems and components, and contractor organizations that perform work on the enterprise’s industrial control system and that have access to the industrial network’s components.
Comment by General Electric
At General Electric, the security of data and critical infrastructure assets is one of our top priorities, and we build our machines and software with security embedded at multiple levels, working closely with our customers to identify and address potential vulnerabilities within installed systems.
The Industrial Internet is a shared ecosystem and we have a shared responsibility to secure it. GE believes that collaboration is the best path to effective cybersecurity solutions, which is why we are partnering with public and private institutions to strengthen IoT security and develop industry best practices.
GE encourages customers to adopt a responsible cyber maintenance plan that includes updating software to apply security patches and ensures the software is a supported version. GE makes SIMs and Service Packs available as they are released at GE’s Customer Center under the Knowledge section. Choosing to filter by product will guide users to specific product information. GE HMI/SCADA CIMPLICITY SIMs are cumulative and installing the most current SIM ensures users have all available fixes.
To receive immediate notices of security alerts and information, please sign up for notifications by visiting the customer profile page on the support site. Instructions are provided at How to sign up for Auto-Notifications for updates.
GE encourages users to be aware of any instances that might result in the public release of the critical patch status of systems as this increases the chances of exploitation.
In addition to data presented in the report, Kaspersky Lab ICS CERT is prepared to provide statistics on the distribution of vulnerable ICS software versions for specific countries or regions upon request from computer emergency response teams, law enforcement agencies and companies that provide IT security services to industrial enterprises in these countries or regions, as well as authorized representatives of industrial organizations that operate in these countries or regions. To request these statistics, it is sufficient to send an email to ics-cert@kaspersky.com.
