24 April 2020
Threat landscape for industrial automation systems. Ransomware and other malware: key events of H2 2019
- 2019 Report at a glance
- Vulnerabilities identified in 2019
- APT attacks on industrial companies in 2019
- Ransomware and other malware: key events of H2 2019
- Ransomware attacks on industrial enterprises
- Indian Kudankulam nuclear power plant infected with malware
- Attack on Rheinmetall technology group
- New wipers attack industrial enterprises
- Attacks on Mitsubishi Electric
- Overall global statistics – H2 2019
Ransomware attacks on industrial enterprises
This section presents an overview of threats related to ransomware activity against municipal institutions, industrial enterprises and critical infrastructure facilities.
Statistics on ransomware attacks against industrial enterprises
In H2 2019, we did a detailed analysis of data on detected Trojan-Ransom attacks and corrected a number of inconsistencies in the classification of malicious objects. The Trojans and worms that had been mistakenly identified as Trojan-Ransom because they demonstrated similar binary code and/or behavior patterns were removed from the sample and the data for past periods was recalculated to provide more accurate estimates.
In H2 2019 ransomware was blocked on 0.61% of ICS computers. According to the refined data, in H1 2019 that figure was 0.76%.
Overall, in 2019 ransomware infection attempts were prevented on 1.0% of ICS computers.
The data for each month of 2019 is shown below.
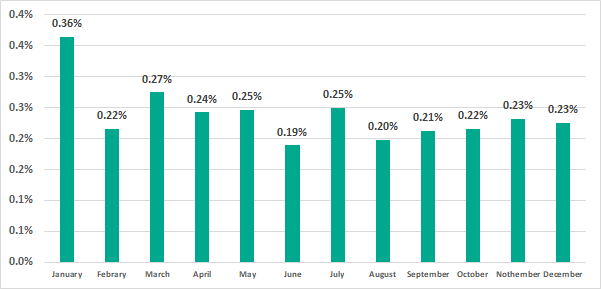
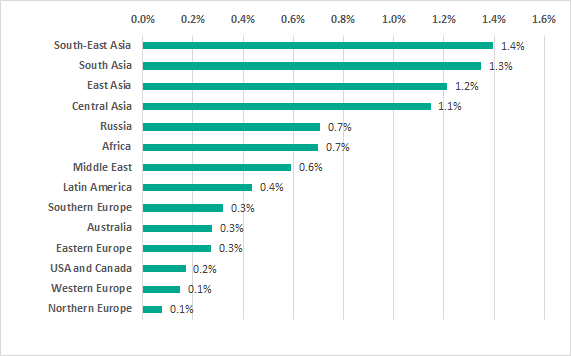
The highest percentage of ICS computers on which ransomware was blocked in H2 2019 was in Asia.
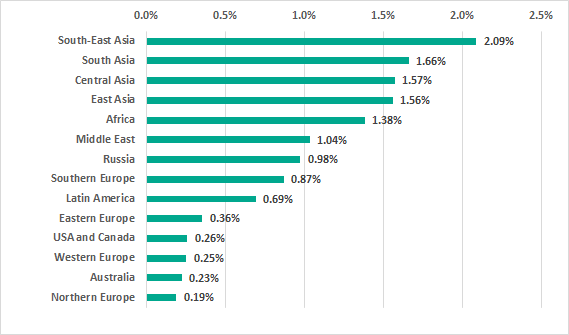
Regions of Asia were in top positions in the ranking for the entire year 2019.
However, Asian countries did not take all of the positions on the TOP 15 ranking for H2 2019.
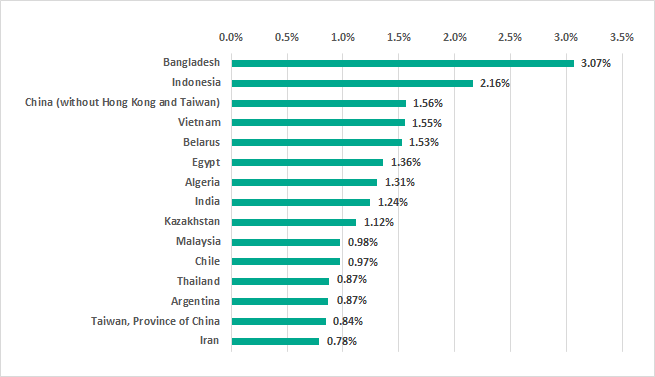
It is worth noting that three European countries, Italy, Ukraine and Belarus, ranked among the TOP 15 countries for the whole year 2019.
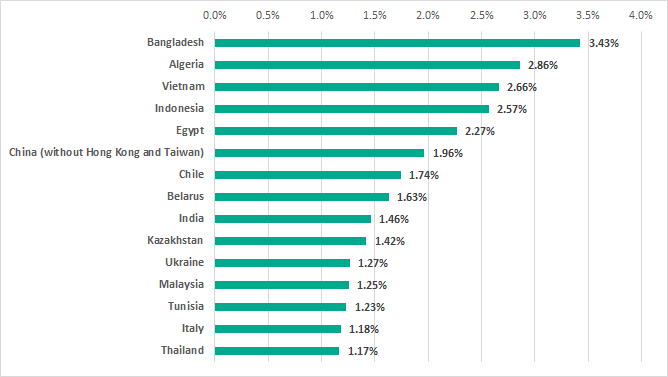
Based on the results of the entire year 2019, the percentage of ICS computers in Russia on which ransomware was blocked amounted to 1.0%.
Cities and industrial facilities targeted by ransomware
A wave of ransomware attacks was observed across the globe throughout 2019. Attack victims included, among others, various critical infrastucture organizations and industrial companies. There has been a significant increase in the number of ransomware attacks on municipal services. Based on publicly available statistics and statements tracked by Kaspersky experts, at least 174 municipal organizations were targeted by ransomware in 2019. This is about 60% more than in the previous year.
Ryuk
In many cases, operators of the Ryuk ransomware (verdict: Trojan-Ransom.Win32.Hermez) were behind the highest-profile encryption ransomware attacks. Throughout 2019, Ryuk infections were mentioned in reports on incidents affecting large enterprises and municipal services.
One example is an attack on Lake City in Florida, USA. As a result of a Ryuk attack, the servers of all city services were disabled, with the exception of police and fire departments, which were on a separate server. The city administration’s phone system was also down (this can happen if IP telephony is used). It has been reported that the city’s services had backed up their systems, but the backup copies could not be used because they had been deleted by the attackers. As a result, the city had to pay a $460,000 ransom.
It should be kept in mind that it is important not only to back up critical systems in a timely fashion, but also to take other measures, designed to safeguard the backup copies created. Specifically, backup copies should be stored on a separate server with access rights configured to enable only creating new and reading existing backup copies. The integrity of backup copies should be verified on a regular basis and the condition of the hardware on which they are stored should be monitored.
In December 2019, the US Coast Guard released an information bulletin on an attack of Ryuk ransomware against a Maritime Transportation Security Act (MTSA) regulated facility. The bulletin did not identify the attacked facility. What is known about the attack is that it used a phishing email campaign and the malware was downloaded to the system after an employee had followed a malicious link. The malware infected the industrial control systems that monitor and control cargo transfer and encrypted files critical to process operations. As a result, all operations on the affected facility were shut down for over 30 hours. Other consequences of the Ryuk infection included the disruption of the facility’s camera and physical access control systems.
Ryuk malware also harmed five oil and gas facilities. The attacks did not bring down any of the facilities, but remote monitoring of the industrial equipment was paralyzed for up to 72 hours, forcing the facilities to switch to manual mode.
The absolute majority of attacks involving Ryuk follow the same pattern. In the first stage, a victim receives a phishing email containing a document with a malicious macro embedded into it. If the victim allows the macro to be executed, the TrickBot malware is downloaded to the machine. The malware enables the attackers to connect to the infected computer and explore the network of the organization being attacked. TrickBot operators attempt to find vulnerable systems and to steal user credentials.
The attackers seek to infiltrate systems running services that are critical for the organization under attack. These are the systems on which the Ryuk malware encrypts data.
Ryuk uses cryptographically secure encryption algorithms. This means that, unfortunately, decrypting files without the private decryption key is impossible. However, risks associated with losing access to data can be mitigated if the organization is prepared for attacks of this type or detects them in their initial stages. You can find our recommendations here.
RobinHood
One of the highest-profile encryption ransomware attacks on municipalities in 2019 was the infection of systems in Baltimore, Maryland in the US with RobinHood malware (verdict: Trojan-Ransom.Win32.Robin). Although the city government’s IT specialists were quick to take action (which included disconnecting all computers and servers to prevent the ransomware from spreading), the malware had taken down about 10,000 devices, including databases used by municipal services. As a result of the attack, some of the city’s services were completely paralyzed. After a short while, a message was posted on the city’s website that contacting the authorities was only possible by telephone.
According to The New York Times, the attackers had used the EternalBlue exploit for the CVE-2017-0144 vulnerability in SMB v1 service. The vulnerability exists in different versions of Windows. EternalBlue got massive coverage in connection with other ransomware, WannaCry, which caused a major outbreak in 2017, infecting millions of computers.
The Baltimore incident highlights another serious issue, which affects both municipal services and systems that are part of the industrial infrastructure – outdated versions of operating systems and other software, which have critical vulnerabilities. In the absolute majority of incidents involving encryption ransomware, the attackers exploit known vulnerabilities, security updates for which have long since been released. For example, Microsoft released the MS17-010 update, which fixes the vulnerability exploited by EternalBlue, on March 14, 2017.
In the case of industrial enterprises, this situation is often due to systems being based on obsolete hardware, which makes updating the software impossible. However, replacing such systems requires substantial financial investment. In such cases, we recommend creating a reliable network perimeter to make it harder for attackers to gain access to vulnerable systems. You can find more details on the techniques used by threat actors to exploit such vulnerabilities and on methods that can be used to provide protection against such attacks in our article.
Sodinokibi (REvil)
In August 2019, systems of 22 towns in Texas, US were attacked at the same time using the Sodinokibi ransomware, also known as REvil (verdict: Trojan.Win32.DelShad). The mass attack became possible when the network of a managed service provider (MSP) used to remotely manage the infrastructure of these towns was breached. Based on available data, the provider in question could be CyrusOne. After compromising the MSP’s systems, the attackers gained remote access to systems of municipalities served by the provider. Their files were encrypted and part of the social services became unavailable. According to public statements, all victim towns refused to pay the attackers for decrypting their files. However, the incident recovery process took several weeks and required significant resources, both human and financial.
Unfortunately, attacks that involve compromising the systems of contractor organizations and third-party software vendors are increasingly common. Such attacks can be based on a wide variety of scenarios. Threat actors can attack a potential victim’s business partner to steal the contents of the business correspondence. The information stolen can subsequently be used, for example, to create phishing emails. In other cases, such as the incident described above, the attackers may use the remote access tools that the contractor uses to serve the organization being attacked. Finally, third-party software vendors can be attacked, as in the case of attacks involving the ExPetr encryption malware, which was installed on a victim’s computer with an update of M.E.Doc accounting software.
To reduce the risk of such incidents, it is essential to control the connections between the organization’s network and the networks of other companies (suppliers, contractors, etc.). A special emphasis should be made on controlling the use of remote administration tools. As a rule, incidents involving ransomware attacks on large enterprises occur over a long period of time, during which the attackers explore the enterprise network and select the systems to be encrypted. This means that the incident response team stands a good chance of nipping the criminals’ activity in the bud. An arrangement whereby contractor organizations need to get all remote connection sessions approved in advance would help identify such incidents. Testing all application software updates before installing them on critical systems is also recommended.
New encryption ransomware is designed to disrupt the operation of industrial software
Why the operation of industrial software is under threat
Encryption ransomware identified in 2019 attacks includes new malware, MegaCortex and Snake. These malicious programs were of particular interest to researchers because of their lists of processes that are terminated before data encryption starts. In addition to processes of anti-malware solutions, database servers and browsers, these lists include processes of industrial automation system software.
MegaCortex, which was discovered in mid-2019 in attacks on the corporate sector, was the first such malicious program. It actively evolved during the year and saw new versions with new functionality emerge. The MegaCortex list of processes terminated before starting encryption includes over 1,000 process names.
In mid-December, one more encryption ransomware program, which was dubbed Snake (or EKANS) was identified. Snake also contains a list of processes that are terminated before starting encryption. It is worth noting that the process list mostly matches that used by MegaCortex, including processes specific to industrial systems.
These are processes associated with industrial automation system software:
- General Electric Proficy data historian (client and server parts);
- General Electric Fanuc licensing server;
- Honeywell’s HMIWeb application;
- FLEXNet licensing server;
- Sentinel HASP license managers;
- ThingWorx Industrial Connectivity Suite;
- Various database processes used in various Historian servers.
It is important to note that both ransomware programs only terminate processes and don’t do anything else to them. In other words, they cannot enter commands or manipulate industrial processes in any way. However, the fact that they terminate processes specific to ICS software can lead to negative cyber-physical consequences. It is most likely that the attackers need to terminate application processes to be able to encrypt databases whose files may be in use and whose modification may be blocked.
The emergence of two different ransomware programs designed, among other things, to disrupt industrial automation systems is one more proof of threat actors’ interest in attacking industrial enterprises. In the event of having to shut down the industrial process due to the failure of a system whose files have been encrypted, an organization may suffer severe losses, making it likely that the victim of such an attack would be prepared to pay a large sum for getting its files decrypted.
Attack details
We believe that MegaCortex and Snake attacks are highly targeted and this belief is in line with other experts’ conclusions. Consequently, it can be assumed that, as in other similar cases, such infections are mostly carried out manually. As a rule, the initial attack vector is brute forcing the credentials for accounts of those employees who have remote access to systems over RDP.
Upon gaining remote access to the first system, the attackers commonly use Mimikatz or similar utilities to steal credentials for accounts used on the infected system. By collecting more and more credentials, the attackers gain access to more and more systems, until they reach a computer on which an account with domain administrator privileges has been used.
Conclusions on the techniques used to distribute this malware are indirectly supported by the fact that in MegaCortex attacks, the attackers were able to compromise the domain controller of the attacked organization, possibly by using previously stolen credentials.
The file encryption process used by MegaCortex and Snake is standard, with no major differences from the process used by other malware in this class.
Remarkably, in MegaCortex attacks, the malicious executables had valid digital signatures. One signature had been issued to Mursa Pty Ltd., the other to ABADAN PIZZA Ltd. It is most likely that the criminal group behind MegaCortex either stole the digital signatures from these organizations itself or bought it from other criminals on the black market.
In the latest versions of MegaCortex, the attackers not only demand a ransom for decrypting the files, but also threaten to make public the victim’s sensitive data should the victim refuse to pay the ransom.
A curious feature of Snake is the ability of the attackers to configure the malware to start encryption at a specific moment in time, e.g., outside the organization’s working hours, when the IT security staff or IT administrators may not be available. This can delay and complicate the victim organization’s incident response.
Connections with other attacks
As mentioned above, a major part of the process list used by Snake (including processes specific to industrial system software) matches the list used by MegaCortex. This has given rise to theories that there is a connection between these two ransomware families. We believe that matching lists is not sufficient grounds for such conclusions, because the MegaCortex malware was analyzed before the emergence of Snake, and the developers of Snake may have got the list of processes from public sources. Importantly, no other technical evidence of connections between the two ransomware families has been found.
After completing the encryption, Snake leaves a message with instructions and demands that the victim connect to the operators by email. The address specified in the ransom message is bapcocrypt@ctemplar.com. This has given rise to a theory that one of the main targets of Snake attacks was BAPCO, an oil-and-gas company that had fallen victim to the Dustman wiper’s attacks. In addition, according to publicly available information, BAPCO uses General Electric equipment, and processes of General Electric software are on the list of processes terminated by MegaCortex and Snake.
However, there is no technical evidence connecting Snake with Dustman. At the same time, the fact that the same enterprise has been attacked by both malicious programs is insufficient to make such conclusions. The theory of these attacks being connected is also contradicted by the different characters of the malicious programs: while Dustman is a wiper, i.e., it attempts to destroy the victim’s data, Snake has the technical capability to decrypt the files.
According to available data, the Snake ransomware is in no way associated with the Snake criminal group, also known as Turla – the name match is a coincidence.
Thus, at this time there is not sufficient evidence to support the attribution of MegaCortex and Snake malware to specific known criminal groups.
LockerGoga: up-to-date information
In the previous report, we wrote about attacks of the LockerGoga encryption ransomware on industrial enterprises. Its victims included Norsk Hydro, a Norwegian metallurgical company, Altran Technologies, a French consulting company, and two US chemical companies, Hexion and Momentive.
The consequences of the attack on Norsk Hydro were substantial: according to an official statement posted on the company’s website, the total financial damage from the attack amounts to 550–650 million Norwegian crowns (about 60.5–71.5 million US dollars).
LockerGoga attacks continued in the second half of the year. In December 2019, the Federal Bureau of Investigation (FBI) issued an alert on the danger of MegaCortex and LockerGoga ransomware attacks. According to the alert, the attackers use phishing emails, SQL injections, and stolen authentication credentials, as well as exploiting vulnerabilities.
In March 2020, the story of the Norsk Hydro attack took a new, unexpected turn. Dragos published a report, in which it expressed doubts as to whether LockerGoga operators had wanted to encrypt files to get a ransom. According to the report, the attackers aimed to destroy files, not encrypt them.
This is supported by the additional functionality that was implemented in the LockerGoga sample used to attack Norsk Hydro. After encrypting files, the malware changed all user account passwords to the same encrypted value, the system’s network card was disabled (apparently to prevent other accounts from authenticating via requests to the domain controller) and a logoff was performed.
In this situation, users were not even able to read the ransom demand left by the malware on the hard drive, so they could not contact the criminals to discuss the conditions on which they might recover access to their files. All of this prevented the attack’s monetization.
Dragos experts believe that the same criminal group called FIN6 (according to FireEye classification) is behind both LockerGoga and Ryuk malware. They also believe that the Norsk Hydro attack may have been sponsored by another country’s government. They argue that other facilities in Norway were attacked at the same time, but these attacks were thwarted thanks to the quick exchange of information between Norsk Hydro and government authorities.
This is not the first instance of data wiping malware being disguised as ransomware. In 2017, Kaspersky experts had discovered that it was technically impossible to decrypt systems infected by ExPetr malware.
WannaCry: is still alive
Almost three years have passed since the outbreak of the WannaCry malware, in which systems were infected in 150 countries across the globe and the total damage reached 1 billion US dollars. Victims of the outbreak included companies involved in different kinds of manufacturing, oil refineries, city infrastructure and electric power distribution facilities.
In one of our publications, we provided details on the way networks of industrial enterprises are infected with the WannaCry worm and on the measures that should be taken for protection.
According to our statistics, among all users of Kaspersky products who were attacked by ransomware Trojans in 2019, over 23% were attacked by the WannaCry malware (verdict: Trojan-Ransom.Win32.Wanna). For industrial organizations, the proportion of users attacked by WannaCry in 2019 to all users attacked by ransomware is in excess of 35%. Both these figures mean that WannaCry continues to spread over the internet and still poses a significant threat, particularly to industrial automation systems.
It should be noted that, in most cases, this means that the MS17-010 security update was not installed on the attacked system, enabling WannaCry to exploit the vulnerability in the SMB v1 service. However, the malicious code was not executed because it was blocked by the Kaspersky product.
The diagram below provides information on operating systems used on ICS computers attacked by WannaCry:
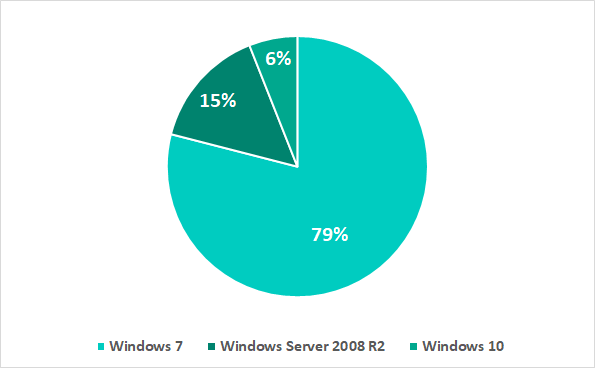
As we can see, the overwhelming majority of systems run Windows 7 (79%) and Windows Server 2008 R2 (15%). The extended support of these systems was discontinued in January 2020. This is particularly worrying, since updates for such systems are released only in exceptional cases.
GandCrab: ransoware-as-a-service in attacks on industrial enterprises
GandCrab (verdict: Trojan-Ransom.Win32.GandCrypt) is notorious encryption ransomware, whose developers chose the RaaS (Ransomware-as-a-Service) business model. GandCrab developers used a web portal to grant various criminal groups access to the malware, after which these groups distributed the ransomware on their own. The service also took care of the ransom payments.
In 2019, law enforcement agencies of several countries and anti-malware companies carried out a set of measures aimed at combating GandCrab. The result was a fully functional utility for decrypting data encrypted by the ransomware, which can successfully handle data encrypted by all GandCrab versions up to 5.1. However, the last version of the ransomware is 5.2. It uses strong encryption based on the RSA and AES algorithms, making it impossible to decrypt data without the private key.
In summer 2019, the group behind GandCrab announced they were closing the ‘service’. In spite of this, GandCrab attacks are still being conducted today. They affect enterprises from various sectors of the economy. Since the ransom payment mechanisms are no longer functional, in the event of infection with the last version of the ransomware (5.2), there is no chance of getting the files decrypted, even by paying a ransom. This has essentially turned the ransomware into a wiper.
Attack details
Two system infection scenarios are currently in use. In both cases, the attack starts with phishing emails, the text in which is written in the language of the country in which the organization under attack operates.
The attack’s further scenario varies depending on the attachment type. In some cases, the attackers use an Excel document with an obfuscated VBA macro, which downloads the GandCrab executable from the attackers’ server and runs it.
After opening the document, the user is prompted to enable active content in the document. If the user agrees to do this, the malicious macro is executed.
In other cases, the GandCrab executable is attached to the email. In most cases, attackers use a double extension, such as .doc.exe or .pdf.exe. This technique enables them to deceive the user, because by default Windows hides extensions for known file types. On a system with default settings, the visible part of the file name will end in .doc or .pdf, respectively. Combined with a replaced application icon, this can convince the user that the attachment is a document rather than an executable file.
Until the middle of 2019, some of the known GandCrab infections used brute forced user authentication data to connect to the system under attack via RDP and execute the ransomware ‘manually’. Today, this attack vector us used by other encryption ransomware.
After launching, the GandCrab executable exploits the CVE-2018-8120 vulnerability. This is an improper handling of objects in memory vulnerability in the Windows Win32k component. To make recovering the information more difficult, the malware also deletes all Windows shadow copies.
The diagram below shows the attack kill chain for GandCrab ransomware attacks:

Indian Kudankulam nuclear power plant infected with malware
In September 2019 information was published regarding the discovery of malware at India’s Kudankulam nuclear power plant. Later, on October 30, the Nuclear Power Corporation of India Ltd (NPCIL) confirmed that a computer in the Kudankulam power plant’s administrative network was infected on September 4. Malware was discovered only on this computer and the plant’s ICS systems were not affected.
The subsequent investigation revealed that the most likely infection vector was a phishing attack via either an infected website or a phishing email.
Some researchers believe that the computer in the Kundakulam plant administrative network was infected with the Dtrack malware, which allows attackers to collect and harvest data from the victim computer.
One of the Dtrack samples captured contained user credentials and IP addresses from the Kudankulam internal network. This could point to a targeted attack on the Indian nuclear power plant.
Attack on Rheinmetall technology group
On September 24, 2019 Rheinmetall Group, a large German technology group, discovered that the IT infrastructure of Rheinmetall Automotive plants in Brazil, Mexico, and the USA had undergone malware attacks.
The attacks caused significant disruptions in production at these plants. The infrastructure at other divisions and Rheinmetall group companies was not affected.
According to the company’s estimates, attack mitigation and restoration of normal system functioning would require 2-4 weeks and the expected costs would run between 3 and 4 million euro a week.
Attack on sPower wind and solar power installations
In September 2019 it was reported that an electric power generation supplier in western US had been hit by a cyberattack, which had caused temporary disruptions in the electrical systems.
Later it was announced that the target of this attack were the wind and solar stations belonging to the Sustainable Power Group (sPower) in Wyoming and California, as well as their 24 hour control center and corporate headquarters in Utah.
According to the US National Energy Technology Laboratory, several power facilities belonging to sPower experienced periodic firewall outages for about 10 hours between 9:12 AM and 6:57 PM on March 5, 2019. These firewalls controlled communications between the control center and several remote solar and wind farms.
Incident investigation showed that Cisco firewalls had rebooted periodically and became inaccessible for about 5 minutes at a time during each reboot. This in turn disrupted connections between the control center and devices located at remote generation sites, whereby power grid operators temporarily lost sight of device data at generation sites producing a total of 500 megawatts. However, these disrupted connections did not affect power generation and no consumers lost power.
The North American Electric Reliability Corporation (NERC) released a report which concluded that the reboots of the firewalls were caused by an attack exploiting a known vulnerability in the firewall’s web interface. Some researchers believe that the vulnerability in question is a DoS vulnerability in the Cisco Adaptive Security Appliance (ASA) (CVE-2018-0296).
New wipers attack industrial enterprises
Bapco, the Bahrain national oil company, was attacked by the Dustman malware on December 29, 2019. According to the National Cybersecurity Authority (NCA) of Saudi Arabia the attack did not cause any severe consequences. Only part of the computers in the Bapco network were affected by the malware and the company was able to continue operations.
Dustman belongs to the wiper malware class (i.e., malware designed to destroy data on the victim computer’s drives) and is designed to delete (wipe) data from infected machines. The malware analysis showed that Dustman is an upgraded version of the previously discovered ZeroCleare wiper. ZeroCleare was used in targeted attacks in the energy and industrial sectors in the Middle East and shares certain features with the Shamoon malware.
Attacks on Mitsubishi Electric
In January 2020 Mitsubishi Electric reported an incident that had occurred on June 28, 2019. The cyberattack allowed the threat actors to gain access to internal networks and systems in around 14 divisions in Japan, China, Russia and other countries.
Mitsubishi Electric staff discovered the attack after they noticed some suspicious activity on a company server. An analysis of this activity revealed that data from the network was collected on one computer and then sent out of the company. The investigation showed that data was sent out several times.
At least 120 computers were compromised in Japan and beyond during this attack. Various data were stolen, including confidential information. The company issued a press release stating that about 200 MB of data was stolen overall.
The attack on Mitsibishi Electric is attributed to the Tick criminal group (also known as The Bald Knight, BronzeButler, and ShadowWali), as well as the BlackTech group (also known as Copper Turtle and PLEAD).
According to media reports, the unauthorized access began with hacking a user account of an employee in China and then the attack spread to sites in Japan. A zero-day vulnerability in an antivirus solution was exploited to gain unauthorized access, however the antivirus solution was not named.
It is most likely that the attackers exploited the CVE-2019-18187 directory traversal vulnerability in Trend Micro OfficeScan (now called Apex One). The vulnerability allows arbitrary files to be uploaded, which in turn makes remote code execution (RCE) possible. In October 2019, Trend Micro fixed the vulnerability and warned that cybercriminals were already exploiting it as part of their attacks.
Также It is thought that the 2019 attack was preceded by an attack by Black Tech in 2017, also through a division in China.
After the 2019 attack was revealed, information was disclosed that over the past 10 years Mitsubishi Electric had undergone a number of attacks at various times. In addition to the Tick and Black Tech groups, it is possible that Aurora Panda (APT 17) and Stone Panda (APT 10, Cloud Hopper) may have also been responsible for some of these.
