24 April 2020
Threat landscape for industrial automation systems. Overall global statistics – H2 2019
- 2019 Report at a glance
- Vulnerabilities identified in 2019
- APT attacks on industrial companies in 2019
- Ransomware and other malware: key events of H2 2019
- Overall global statistics – H2 2019
In this section, we present the findings of an analysis of statistical data obtained using the Kaspersky Security Network (KSN), a distributed antivirus network. The data was received from those KSN users who gave their voluntary consent to have data anonymously transferred from their computers and processed for the purpose described in the KSN Agreement for the Kaspersky product installed on their computer.
Connecting to the KSN network enables our customers to reduce the time it takes the security solutions installed on their systems to respond to previously unknown threats and to improve the overall detection quality provided by the security products through querying the cloud infrastructure in which malicious object data is stored. That data is technically impossible to transfer entirely to the client side due to its large size and resource consumption.
The telemetry data transferred by the user includes only those types and categories of information which are described in the relevant KSN Agreement. That data is not only significantly helpful in analyzing the threat landscape, but it is also necessary to identify new threats, including targeted attacks and APTs1.
Methodology used to prepare statistics
The statistical data presented in the report was received from ICS computers protected by Kaspersky products that Kaspersky ICS CERT categorizes as part of the industrial infrastructure at organizations. This group includes Windows computers that perform one or several of the following functions:
- supervisory control and data acquisition (SCADA) servers,
- data storage servers (Historian),
- data gateways (OPC),
- stationary workstations of engineers and operators,
- mobile workstations of engineers and operators,
- Human Machine Interface (HMI),
- computers used for industrial network administration,
- computers used to develop software for industrial automation systems.
For the purposes of this report, attacked computers are those on which Kaspersky security solutions blocked one or more threats during the reporting period. When determining percentages of machines on which malware infections were prevented, we use the ratio of the number of computers attacked during the reporting period to the total number of computers in our sample from which we received anonymized information during the reporting period.
Percentage of computers on which malicious objects were blocked
In H2 2019, malicious objects were blocked on 39.2% of ICS computers – this is lower than H1 2019 by 2 percentage points.
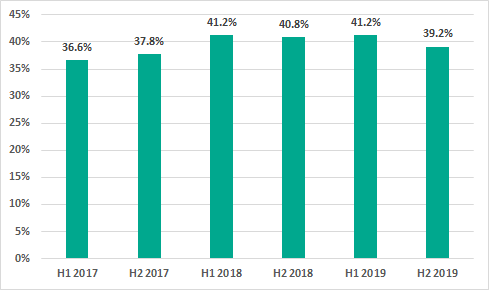
In H2 2019 the highest percentage of ICS computers on which malicious objects were blocked was recorded in October. The numbers for October are only 0.3% less than in April, the leader in H1 2019.
It’s worth noting that the seasonal dynamics that we have observed in recent years continued in 2019: the highest percentage of ICS computers on which threats were blocked was recorded in in spring and autumn. However, the decrease in numbers over November and December 2019 was greater than in 2018.
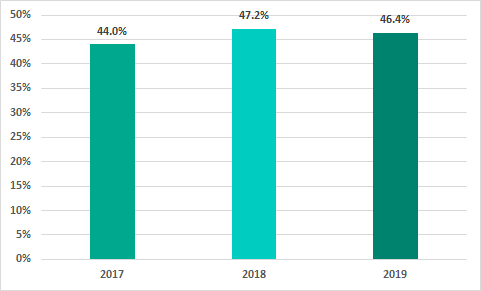
Altogether, in 2019 the percentage of ICS computers on which malicious objects were blocked decreased by 0.8 p.p.
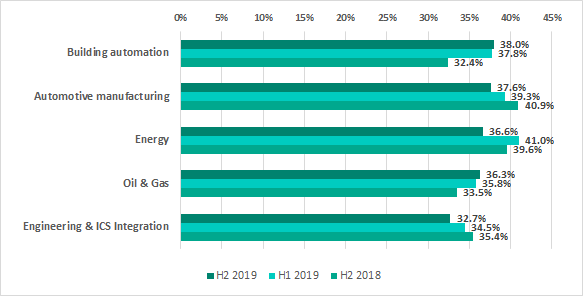
The variety of malware detected
In H2 2019, Kaspersky security solutions blocked over 19.5 thousand malware modifications from 2.3 thousand different families on industrial automation systems.
Malicious object categories
Malicious objects blocked by Kaspersky products on ICS computers fall into many categories.
To give a better idea of types of detected threats, we conducted a detailed classification, which in turn required significant amounts of manual analysis. The resulting percentages should not be summed up because in many cases threats of two or more types may have been blocked on a single computer during the given reporting period.
The results of our detailed analysis revealed the following estimates of the percentages of ICS computers on which malware from different categories had been blocked:
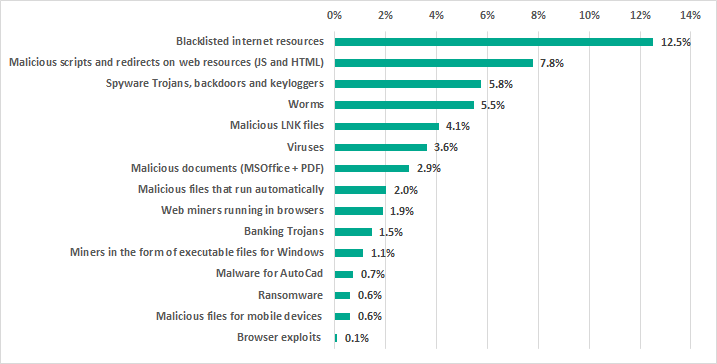
- 12.5% – blacklisted internet resources. Web-antivirus protects a computer when programs installed on it (browsers, email clients, automatic application update modules and others) attempt to connect to blacklisted IP addresses and URLs. Such web resources are associated in some way with distributing or controlling malware.Specifically, blacklisted resources include, among others, those used to distribute such malware as Trojan-Spy or ransomware disguised as utilities for cracking or resetting passwords on controllers of various manufacturers, or as cracks/patches for industrial and engineering software used in industrial networks.
- 7.8% – malicious scripts and redirects on web resources (JS and HTML) executed in the context of the browser, as well as browser exploits – 0.16%.
- 5.8% – Spy Trojans, backdoors and keyloggers, which appear in numerous phishing emails sent to industrial enterprises. As a rule, the ultimate goal of such attacks is to steal money.
- 5.5% – worms (Worm), which usually spread via removable media and network shares, as well as worms distributed via email (Email-Worm), network vulnerabilities (Net-Worm) and instant messengers (IM-Worm). Most worms are obsolete from the network infrastructure viewpoint. However, there are also worms like Zombaque (0.02%) which implement a P2P network architecture allowing threat actors to activate them at any point.
- 4.1% – malicious LNK files. These files are mainly blocked on removable media. They are part of the distribution mechanism for older families such as Andromeda/Gamarue, Dorkbot, Jenxcus/Dinihou and others.This category also includes a wide variety of LNK files with the CVE-2010-2568 vulnerability (0.62%), which was first exploited to distribute the Stuxnet worm and has later been exploited to spread many other families, such as Sality, Nimnul/Ramnit, ZeuS, Vobfus, etc.
Today, LNK files disguised as legitimate documents can be used as part of a multistage attack. They run a PowerShell script that downloads a malicious file.
In rare cases, the malicious PowerShell script downloads binary code – a specially crafted modification of a passive TCP backdoor from the Metasploit kit – and injects the code into memory.
- 3.6% – Virus class malware. These programs include such families as Sality (1.1%), Nimnul (0.7%), and Virut (0.5%), which have been detected for many years. Although these malicious families are considered obsolete because their command-and-control servers have long been inactive, they usually make a significant contribution to the statistics due to their self-propagation and insufficient measures taken to completely neutralize them.
- 2.9% – malicious documents (MSOffice + PDF) containing exploits, malicious macros or malicious links.
- 2.0% – malicious files (executables, scripts, autorun.inf, .LNK and others) that run automatically at system startup or when removable media are connected. These files come from a variety of families that have one thing in common – autorun. The least harmful functionality of such files is automatically launching the browser with a predefined home page. In most cases, malicious programs that use autorun.inf are modifications of malware from old families (Palevo, Sality, Kido, etc.).
- 1.9% – web miners running in browsers. 1.1% – miners in the form of executable files for Windows.
- 1.5% – banking Trojans.
- 0.7% – malware for AutoCad. It is worth noting that malware for AutoCad, specifically viruses, is mainly detected on computers that are part of industrial networks, including network shares and engineering workstations, in East Asia.
- 0.6% – malicious files for mobile devices that are blocked when such devices are connected to computers.
- 0.6% – ransomware.
Geographical distribution
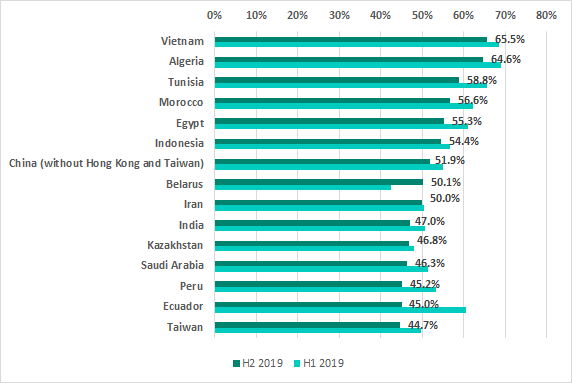
The top five positions in the ranking based on the percentage of ICS computers on which malicious activity was prevented have remained the same for a year and a half now. The only exception was H1 2019 when Bolivia unexpectedly jumped to second place and squeezed Egypt out of the TOP 5.
The most noticeable increases in the percentages of ICS computers on which malicious activity was prevented were observed in Singapore (an increase of 9.2 p.p.), Belarus (7.6 p.p.) and South Africa (6.2 p.p). It is worth noting that the percentages for Singapore had decreased during the previous 3 reporting periods.
In Russia, malicious objects were blocked at least once during H2 2019 on 43.1% of ICS computers, which is 1.7 p.p. lower than the level observed in H1 2019 (44.8%).
In H2 2019 the US (18.3%) dropped out of the TOP 10 ranking of most secure countries. Great Britain (19%) and Singapore (24.2%) were replaced in the ranking by Romania, Austria and Australia.
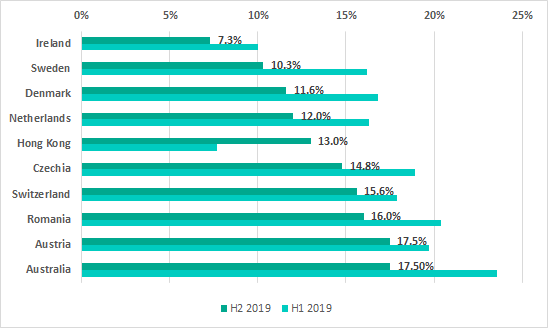
Africa, Southeast Asia and South Asia continue as the traditional leaders in the ranking of regions of the world based on the percentage of ICS machines on which malicious activity was prevented.
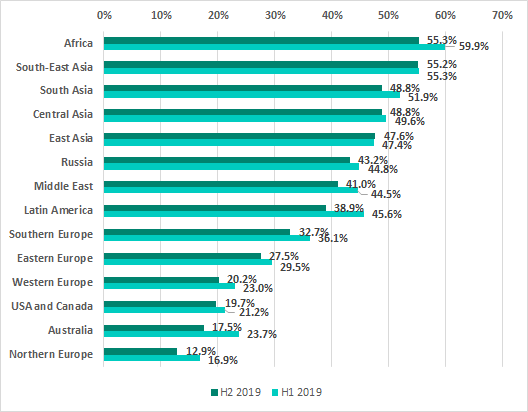
Threat sources
In recent years, the internet, removable media and email have been the main sources of threats for computers in the industrial infrastructure of organizations.
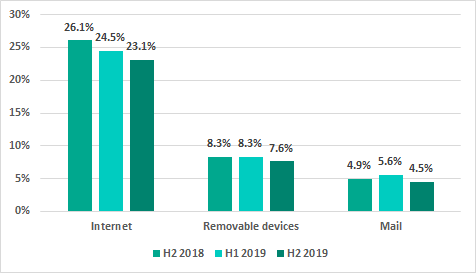
* percentage of ICS computers on which malicious objects from different sources were blocked
The downward trend continues for the percentage of ICS computers on which malicious objects from the internet were blocked. In H2 2019, this percentage has decreased by another 1.4 p.p.: the internet is now the source of threats blocked on 23.1% of ICS computers.
A significant proportion of internet threats are associated with web pages on various sites infected with web miners, Trojan downloaders and scripts designed to steal cookie files. A decrease in the percentage of ICS computers exposed to these threats is due in part to a smaller number of page views on such sites and to infections being eliminated from web resources.
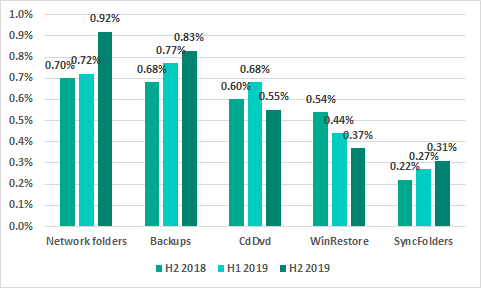
* percentage of ICS computers on which malicious objects from different sources were blocked
Main threat sources: geographical distribution
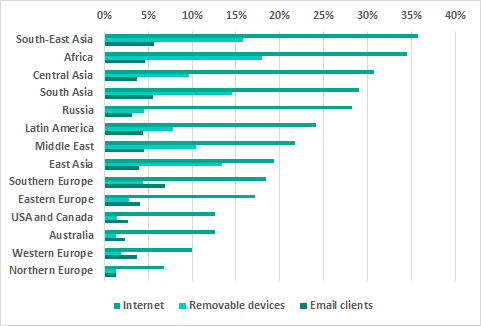
* percentage ICS computers on which malisious objects from different sources were blocked
Internet
The internet is the main source of threats in all regions of the world. However, the percentage of ICS computers on which internet threats were blocked is much lower in Northern and Western Europe and in North America than in other regions.
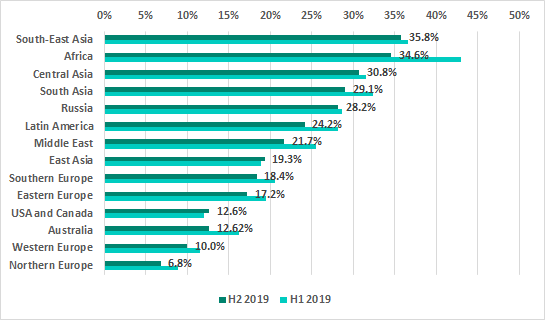
Most countries in the TOP 15 by percentage of ICS computers on which internet threats were blocked have remained on the ranking. Chile, Ukraine and Bolivia have been replaced by “newcomers” Belarus, Russia and Iran.
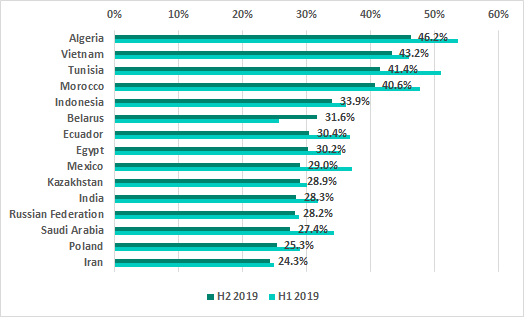
Removable media
There are no changes in the ranking of regions by the percentage of ICS computers where threats were blocked when removable media was attached. The highest percentage of ICS computers on which threats were blocked when removable media were connected to them was recorded in Africa, South Asia and South-East Asia. That percentage was the lowest in Australia, Northern Europe and North America.
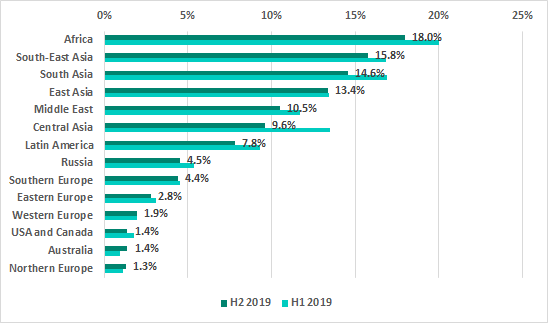
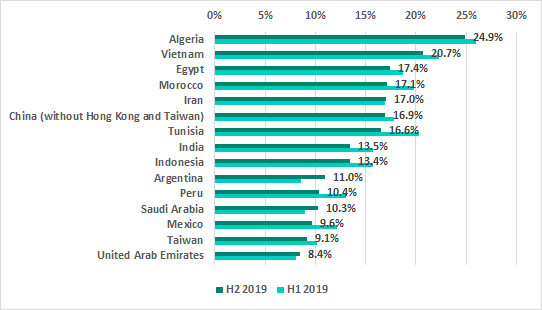
In H2 2019 the TOP 15 countries ranked by percentage of ICS computers on which malware was blocked when removable media were connected to them did see a few changes: Turkey, Kazakhstan, Thailand and Bolivia were ousted by Taiwan, Saudi Arabia, Argentina and the United Arab Emirates.
Email clients
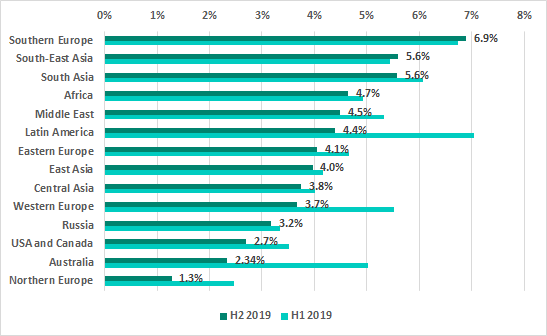
For the first time we see Southern Europe lead in the ranking of regions based on the percentage of ICS computers on which malicious email attachments were blocked.
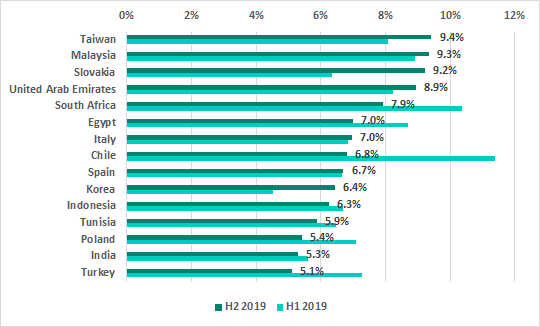
In H2 2019 we saw changes in a third of the TOP 15 countries ranked by the percentage of ICS computers on which malicious email attachments were blocked.
Germany, Japan, Mexico, Argentina and Ecuador left the ranking, while the newcomers included Slovakia, which immediately jumped to third place, as well as Spain, South Korea, Tunisia and India.
Kaspersky Industrial Control Systems Cyber Emergency Response Team (Kaspersky ICS CERT)
is a global project of Kaspersky aimed at coordinating the efforts of automation system vendors, industrial facility owners and operators, and IT security researchers to protect industrial enterprises from cyberattacks. Kaspersky ICS CERT devotes its efforts primarily to identifying potential and existing threats that target industrial automation systems and the industrial internet of things.
Kaspersky ICS CERT
ics-cert@kaspersky.com
1. We recommend that organizations which have any restrictions in place with respect to transferring data outside the organization’s perimeter should consider using the Kaspersky Private Security Network service.

